Hello @NeverKnow ,
Thank you for posting here.
Based on the description "The schema is already updated to a 2019 schema.", do we mean we want to replace Windows server 2012 R2 DCs using Windows server 2019 DCs? If so, from the link below, we can see:
The minimum requirement to add a Windows Server 2019 Domain Controller is a Windows Server 2008 functional level. The domain also has to use DFS-R as the engine to replicate SYSVOL.
Forest and Domain Functional Levels
https://learn.microsoft.com/en-us/windows-server/identity/ad-ds/active-directory-functional-levels
If we want to add 2019 DCs to the existing domain, we must check functional level (forest functional level should be at least Windows Server 2008 functional level)and SYSVOL replication type (should be DFSR replication).
The method to check functional level (run the following commands):
(Get-ADForest).ForestMode
(Get-ADDomain).DomainMode
The method to check SYSVOL replication type:
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\DFSR\Parameters\SysVols\Migrating Sysvols\LocalState registry subkey. If this registry subkey exists and its value is set to 3 (ELIMINATED), DFSR is being used. If the subkey does not exist, or if it has a different value, FRS is being used.
Check AD environment health:
1.do a dcdiag and identify any existing issues and fix them
1)Check if AD replication works properly by running repadmin /showrepl and repadmin /replsum on both DCs, also. If we find any AD replication issue, fix it, too.
2)Check both SYSVOL folder and Netlogon folder are shared by running net share on each DC.
3)Check we can update gpupdate /force on each DC successfully.
4)Back up all domain controllers if needed.
5)We had better perform the DC migration during downtime.
Add server to domain and promote the server as domain controller:
2.Join new AD server to domain with IP address: 192.168.1.240
3.Add the AD DC and DNS role - all replication to fully happen
Add AD DS and DNS roles on this server 2019 (also as GC).
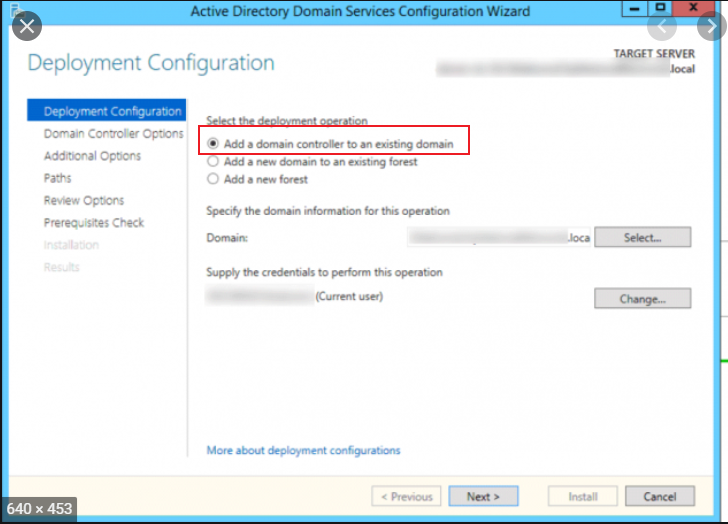
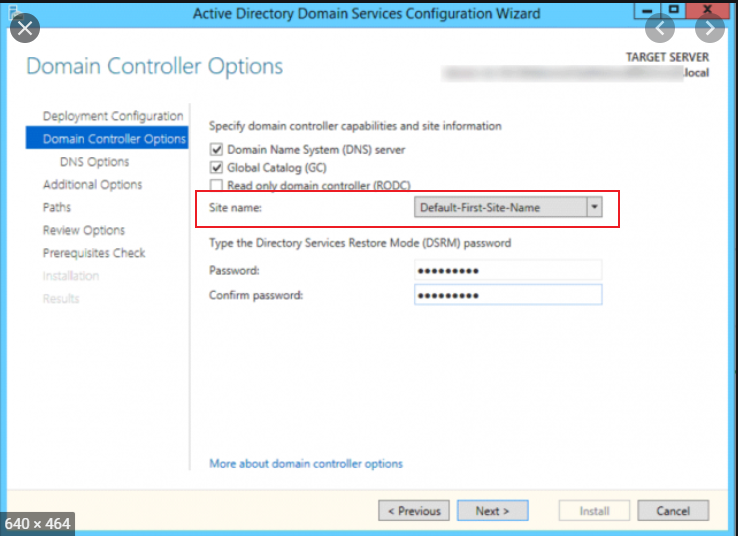
Promote this server 2019 as a domain controller. During promotion, we should select "add a domain controller to the existing domain" and select the correct site name we want for this DC.
Check AD environment health again.
Transfer FSMO roles from 2012 R2 to 2019
If everything works fine, we can transfer FSMO roles from 2012 R2 to 2019.
Update DNS server for all the machines that points to the old DC
7.Update any client PCs that were using old DNS to use new DNS (via DHCP)
Because the old DCs is also DNS server, before we demote old DCs, we should:
Update the DNS client configuration on all member workstations, member servers, and other DCs that might have used this DNS server for name resolution. If it is required, modify the DHCP scope to reflect the removal of the DNS server.
Update the Forwarder settings and the Delegation settings on any other DNS servers that might have pointed to the old DC for name resolution.
Demote the old DC if needed.
4.Remove the AD DC and DNS role from server (IP: 192.168.1.180)
5.Reboot original AD DC/DNS server to ensure complete
6.Ensure new AD DC server is part of the site (AD Sites & Services)
Raise the functional level after demoting the old DC if needed.
Tip:
- If AD replication is working fine, when we add new a DC to the existing domain, after AD replication is complete, all the AD data in all DCs should be the same.
- If we have installed any other roles in the old Domain Controllers, migrate all the roles if needed.
- Usually, we want a DC to be just a DC, there is nothing else, because this reduces possible resource conflicts and exploit vulnerabilities and minimizes patching of other applications that might cause downtime.
Ideally, a DC should be easy to replace, just by standing up another DC.
When we put other software and roles on one DC, maybe the DC is harder to replace it.
For example,
If we have a DC with AD CS(it is also a CA server), if there is some issues with this DC and we want to demote this DC, we need to remove AD CS first and then demote this DC.
Hope the information above is helpful. If anything is unclear, please feel free to let us know.
Best Regards,
Daisy Zhou
============================================
If the Answer is helpful, please click "Accept Answer" and upvote it.
Note: Please follow the steps in our documentation to enable e-mail notifications if you want to receive the related email notification for this thread.
============================================
If the Answer is helpful, please click "Accept Answer" and upvote it.
Note: Please follow the steps in our documentation to enable e-mail notifications if you want to receive the related email notification for this thread.