@AmitJaiswal-8743 Thank you for reaching out to Microsoft Q&A. Based on your statement, you are making a request from Client (Laptop) -> Azure Front Door -> Application Gateway -> API Management and want to see Client IP as Laptop IP in APIM logs. Unfortunately, Client IP will not reflect the originating client, instead will return the IP address of the client from which it received the request (App Gateway here) and you cannot change it (or append to existing value).
This is where you can use "X-Forwarded-For" header to identify the originating client IP. Both Front Door and Application Gateway support X-Forwarded-For header. If the header is already present, it will append the Client IP to existing value otherwise it adds the Client IP as value. Refer Front Door and Application Gateway docs which describes about this header.
- You can rewrite this header in the application gateway as original client IP as mentioned in Remove port information from the X-Forwarded-For header. Refer a similar thread on this discussion.
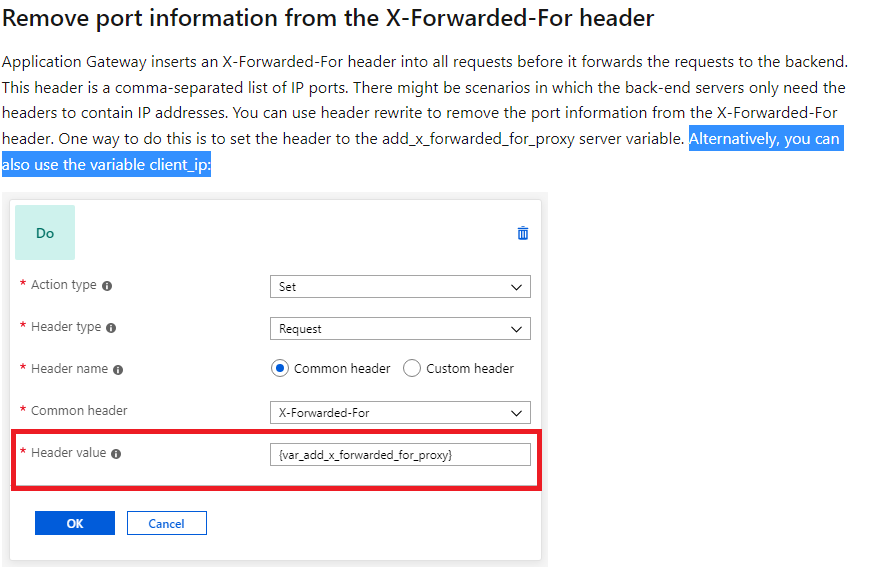
- You can also do a filter or rewrite this header in API Management using policy and here is a sample policy.
Both will enable you to have "X-Forwarded-For" header reflecting the originating Client IP instead of appending multiple IPs. I hope this answers your question and feel free to add if you have any questions. I would be happy to assist you. Please 'Accept as answer' and ‘Upvote’ if it helped so that it can help others in the community.