Hi @Anonymous ,
How do you connect to the azure sql from outside the vnet?
How about trying connecting by DNS and you can check this link, following the steps on it :https://social.technet.microsoft.com/wiki/contents/articles/36674.access-azure-vm-sql-server-outside-of-network.aspx#:~:text=Access%20Azure%20VM%20SQL%20Server%20Outside%20of%20Network,5%20Step%205%3A%20Access%20from%20different%20machine.%20
Has anyone seen this before and know a solution?
Pls take the following steps:
- Open SQL Server Configuration Manager, and then expand SQL Server 2005 Network Configuration.
- Click Protocols for InstanceName, and then make sure TCP/IP is enabled in the right panel and double-click TCP/IP.
- On the Protocol tab, notice the value of the Listen All item.
- Click the IP Addresses tab:
If the value of Listen All is yes, the TCP/IP port number for this instance of SQL Server 2005 is the value of the TCP Dynamic Ports item under IPAll.
If the value of Listen All is no, the TCP/IP port number for this instance of SQL Server 2005 is the value of the TCP Dynamic Ports item for a specific IP address. - Make sure the TCP Port is 1433.
- Click OK.
Is there a way to bind ports on SQL managed instance?
You can set the ports number in SSCM----SQL Server Nerwork Configuration----TCP/IP
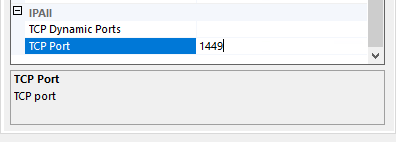
Delete the 'zero' in the dynamic ports window
Then enter TCP port: user-defined
If the answer is helpful, please click "Accept Answer" and kindly upvote it. If you have extra questions about this answer, please click "Comment"

