Hello @ajc63298 / @ajc63298,
Thanks for posting your query. For single-page apps (SPA) via the authorization code flow the app must be registered as SPA with port 3000 and not as web app. As per: https://learn.microsoft.com/en-us/azure/active-directory/develop/single-page-app-quickstart?pivots=devlang-javascript#step-1-register-your-application
- Sign in to the Azure portal.
- If you have access to multiple tenants, use the Directories + subscriptions filter in the top menu to switch to the tenant in which you want to register the application.
- Search for and select Azure Active Directory.
- Under Manage, select App registrations > New registration.
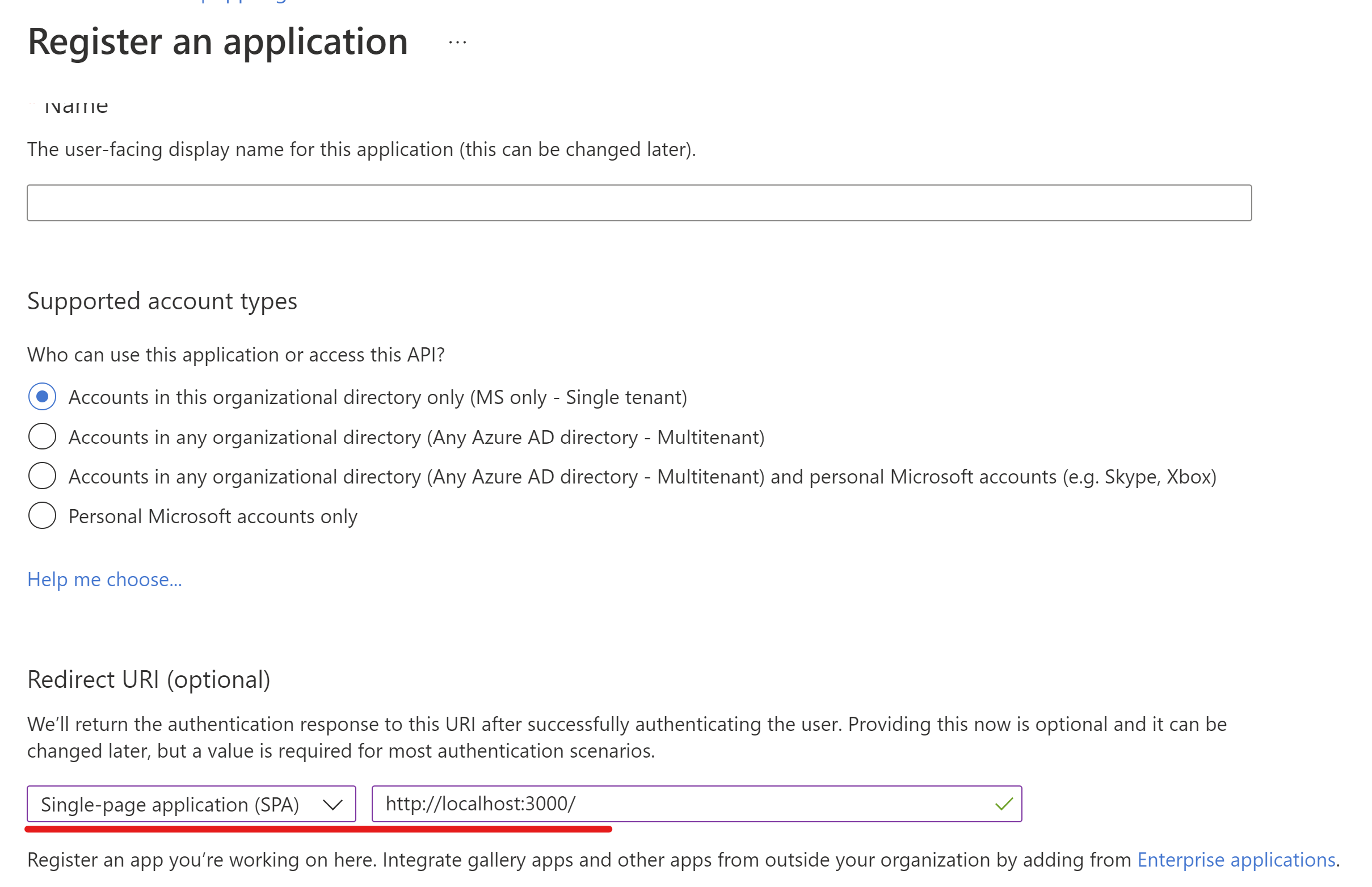
- Enter a Name for your application. Users of your app might see this name, and you can change it later.
- Under Supported account types, select Accounts in any organizational directory and personal Microsoft accounts.
- Select Register. On the app Overview page, note the Application (client) ID value for later use.
- Under Manage, select Authentication.
- Under Platform configurations, select Add a platform. In the pane that opens select Single-page application.
- Set the Redirect URI value to http://localhost:3000/.
- Select Configure.
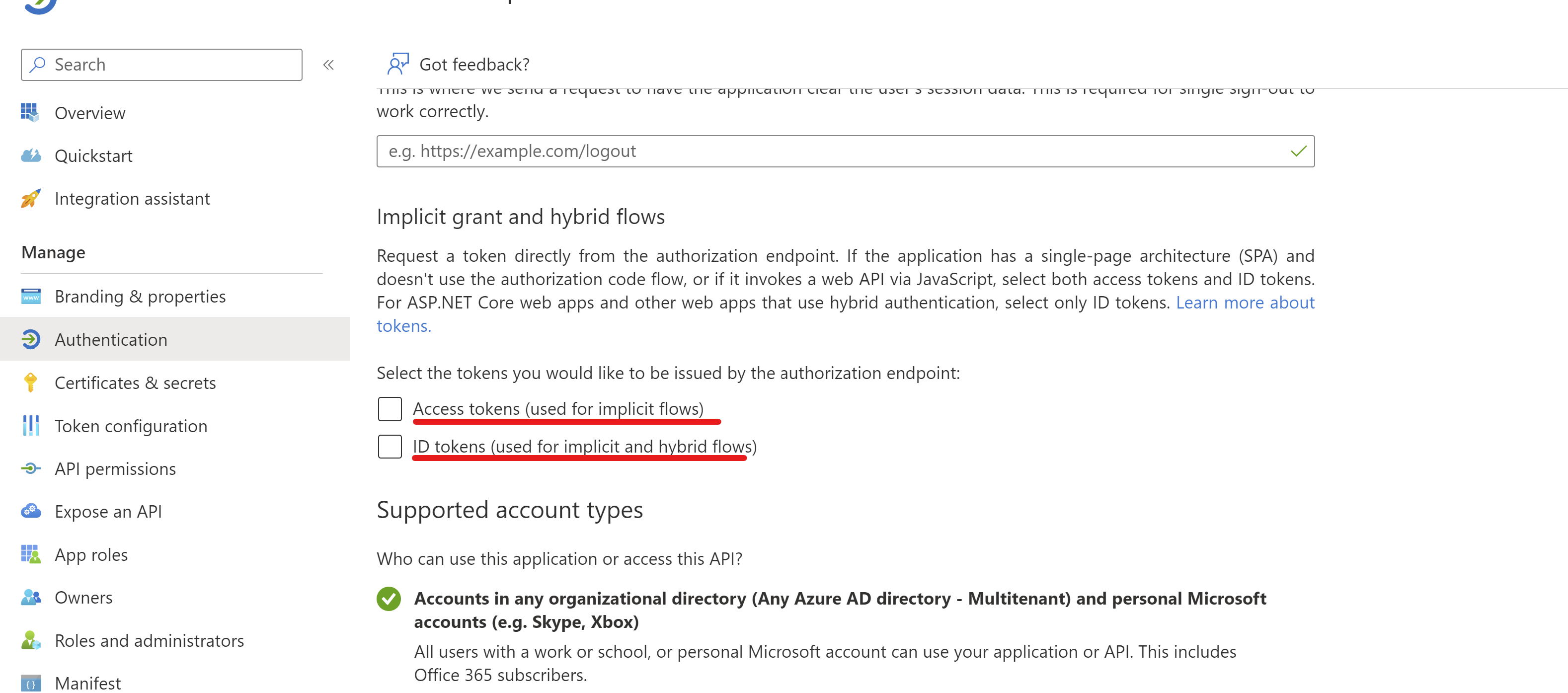
- Also ensure that implicit grant is not enabled. MSAL.js 2.0 does not support implicit grant. Enable implicit grant settings only if your app is using MSAL.js 1.0
Please "Accept the answer" if the information helped you. This will help us and others in the community as well.
Thanks,
Akshay Kaushik
