Hi @Mohammed Sohail ,
Thanks for reaching out.
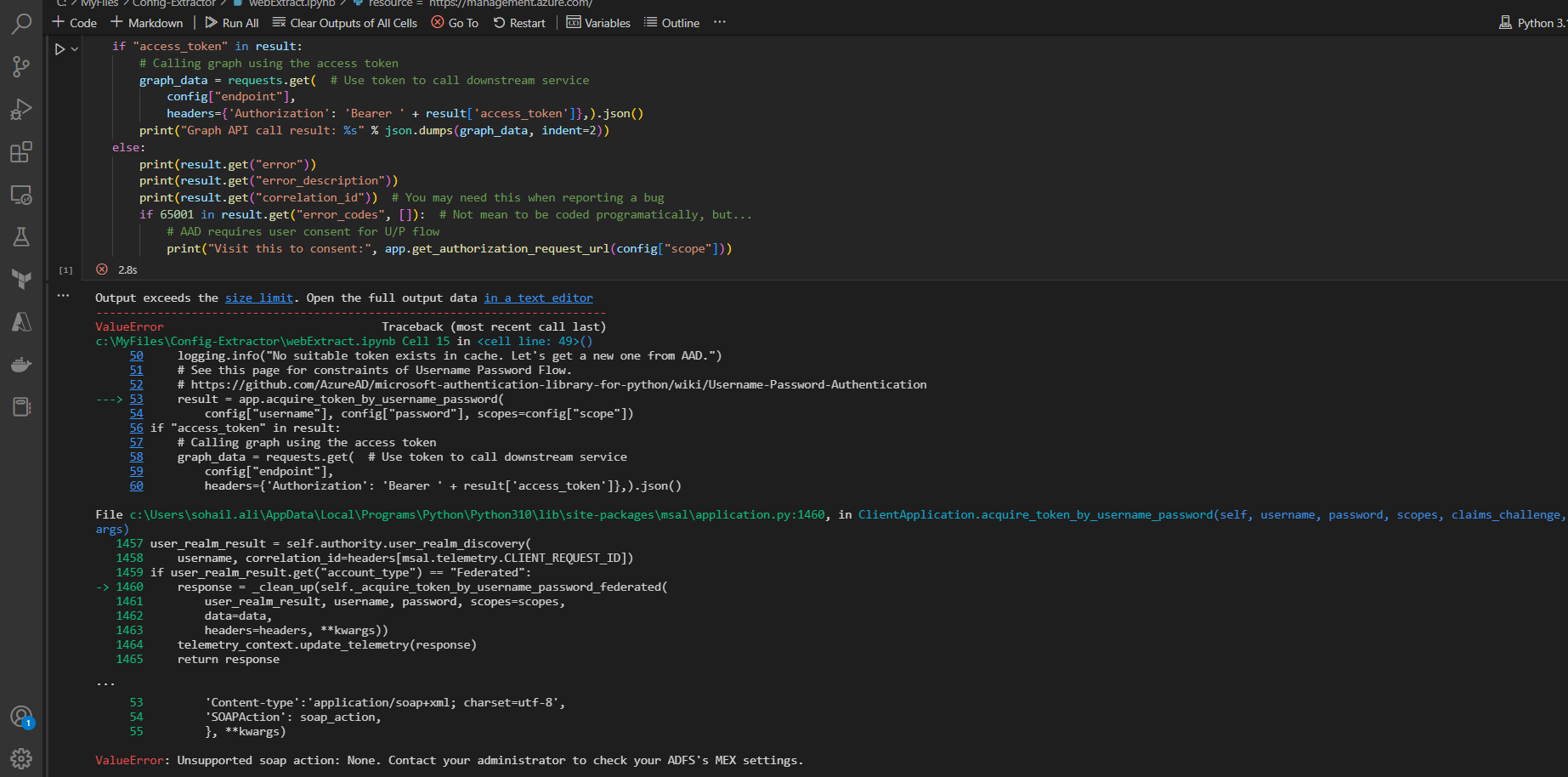
I understand you are trying to get access token through Resource Owner Password Credential (ROPC) flow using Confidential client application class but getting the error.
I have never come across this error before. Are you migrating your application from ADAL to MSAL?
But based on the snippet you mentioned, you are using confident client with ROPC flow which is technically supported but not by any of the official SDK's.
If you wish to use the confidential client, then it must be included the client_secret which is missing in above snippet and scope should be passed as space separated list of permissions.
Sample code using public client application with ROPC flow: https://github.com/Azure-Samples/ms-identity-python-desktop/blob/master/1-Call-MsGraph-WithUsernamePassword/username_password_sample.py
ROPC flow with required parameters: https://learn.microsoft.com/en-us/azure/active-directory/develop/v2-oauth-ropc#authorization-request
Hope this will help.
Thanks,
Shweta
-----------------------------------
Please remember to "Accept Answer" if answer helped you.