Hello Team,
I want to ingest SQL logs into sentinel to monitor CRUD operations of database.
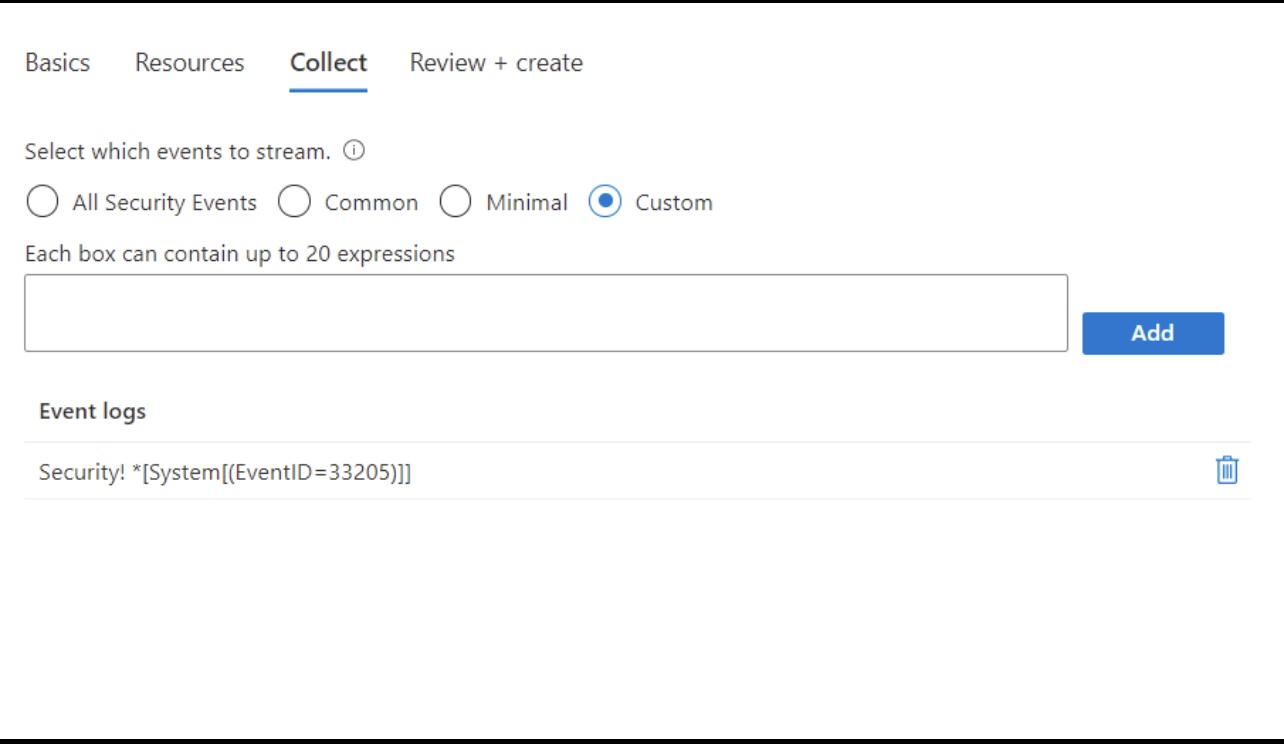
After bit of research I figured out that crud operations fall under event id 33205. The ingestion was done previously, but no one has verified if we have received crud operation related logs. And later this rule was disabled in sentinel.
A custom DCR (data collection rule) has been created using windows security events connector. And the rule screenshot is attached below. But later DCR rule has been disabled.
Now I have below queries:
- I have checked logs and using KQL queries I was able to find out event ID 33025. However, this does not contain any CRUD based operations. If the DCR rule is disabled, then how am I able to see logs with event ID 33025?
- I have seen a reference article by Microsoft which states about ingesting SQL logs to sentinel and monitoring CRUD operations, however that process is no longer possible as the connector he used was windows event logs which is no longer available now. We instead have windows security event connector. Can you please share the latest document to cover this process?. Below is the link I'm referring to :
https://techcommunity.microsoft.com/t5/microsoft-sentinel-blog/monitoring-sql-server-with-azure-sentinel/ba-p/1502960
- While ingesting SQL logs into sentinel, do we require to configure each sql server to send logs to sentinel? Or is there
any way where all the sql logs are sent to one central sql repo and we can push these logs directly into sentinel?