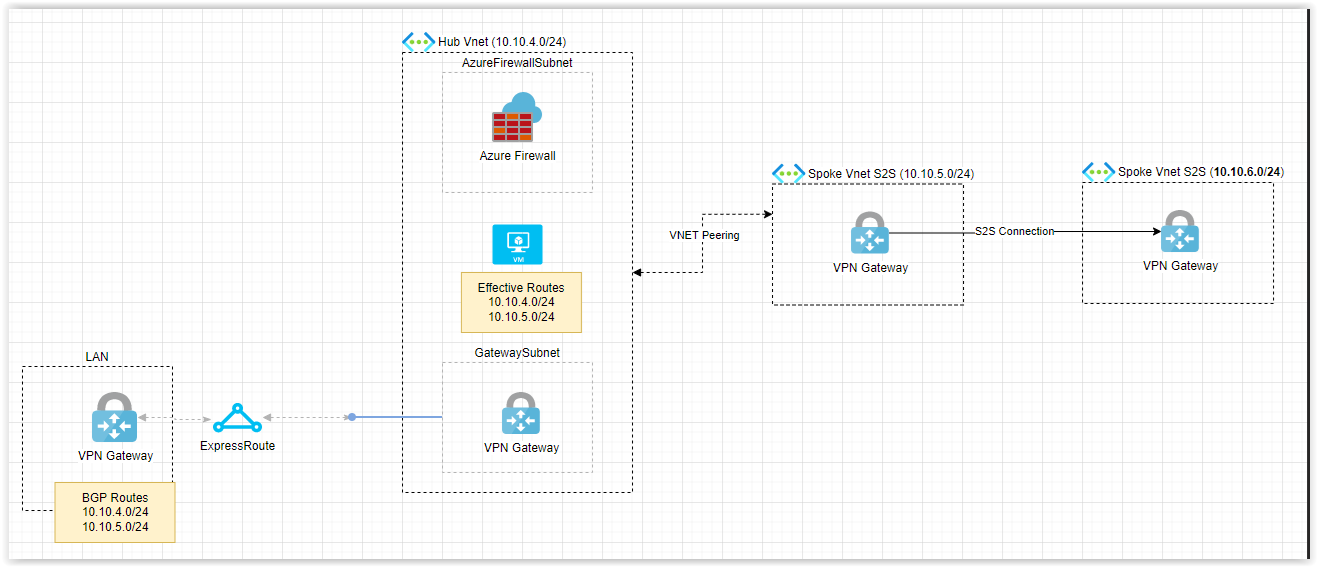
In theory you might be able to add a user defined route to the 10.10.4.0/24 network defining the next hop for the 10.10.6.0/24 network to be the IP address of the VPN Gateway in the 10.10.5.0/24 network. Whether this would then automatically be propagated over BGP to the LAN network, I do not know (but I sincerely doubt that). You night need to add extra custom routes to your LAN network to make this work.
you could start with adding this UDR and then test from the VM in the 10.10.4.0/24 network and see if that VM can connect. I bet that in your current set-up this VM also cannot connect to the 10.10.6.0/24 network. You first need to fix that step. Then you can look into propagating that communication to the LAN network.
I do agree with @Joe Carlyle that your set-up is not according to best practices.