Hello @Mohsen Akhavan ,
Welcome to Microsoft Q&A Platform. Thank you for reaching out & hope you are doing well.
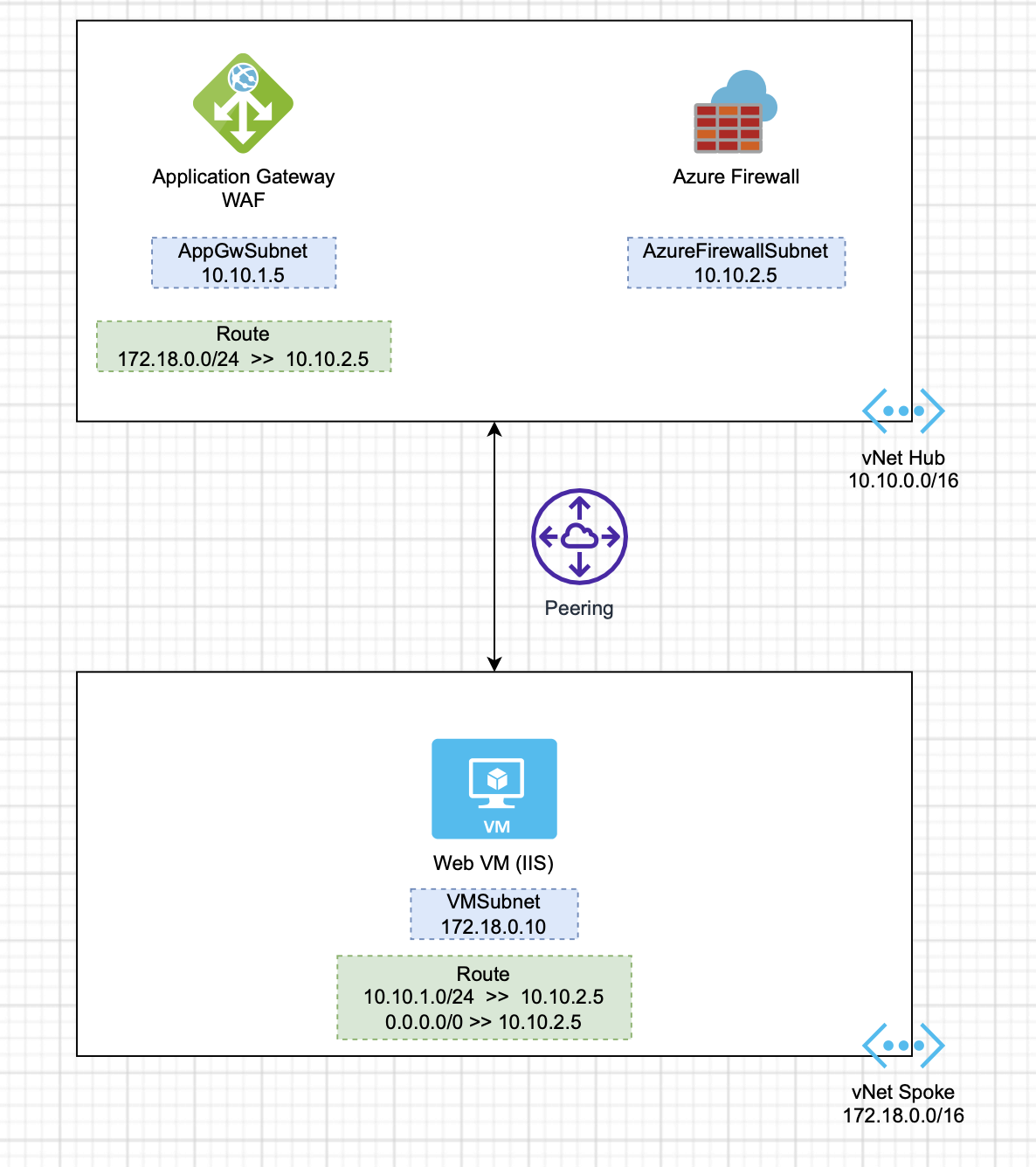
I understand that you would like to use Azure Application Gateway (WAF) and Azure Firewall together in your hub Vnet within your hub and spoke topology.
There are 3 common recommended designs to use Azure Application gateway and Azure Firewall together as mentioned in this doc:
https://learn.microsoft.com/en-us/azure/architecture/example-scenario/gateway/firewall-application-gateway
I believe you are trying to implement the second scenario where Application Gateway is before the Azure Firewall.
This design is implemented when you want Azure Firewall to inspect all traffic, WAF to protect web traffic, and the application to know the client's source IP address. With Azure Firewall Premium and TLS inspection, this design supports the end-to-end SSL scenario as well.
Refer : https://learn.microsoft.com/en-us/azure/architecture/example-scenario/gateway/firewall-application-gateway#application-gateway-before-firewall
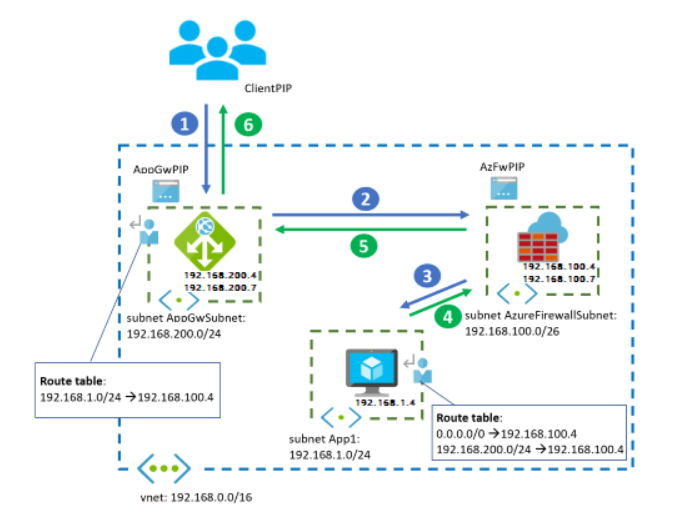
For this scenario, routing will as mentioned below:
- The client starts the connection to the public IP address of the Azure Application Gateway.
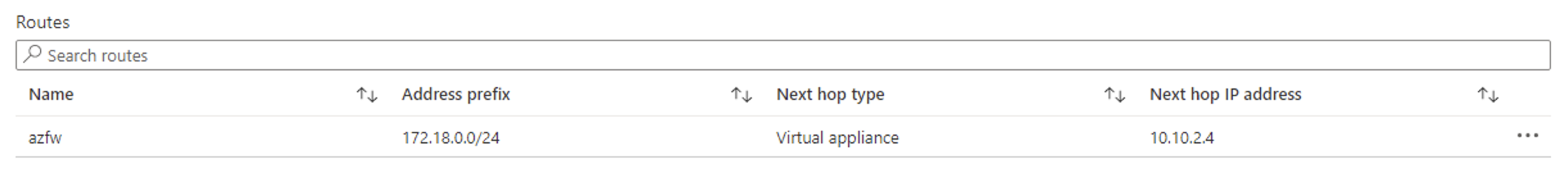
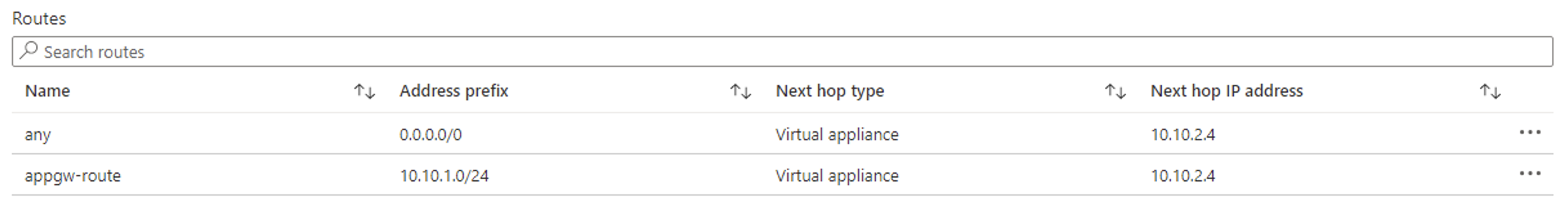
- On your App gateway subnet, there should be a UDR with destination address space of your VM subnets pointing to next hop Azure Firewall.
- The request to the Application Gateway public IP is distributed to a back-end instance of the gateway. The Application Gateway instance stops the connection from the client, and establishes a new connection with one of the back ends. The UDR to the VM subnet in the Application Gateway subnet forwards the packet to the Azure Firewall, while preserving the destination IP to the web application.
- Azure Firewall doesn't SNAT the traffic, because the traffic is going to a private IP address. It forwards the traffic to the respective VM if rules allow it.
- On the VM subnet, there should be a UDR with destination address space of App gateway subnet pointing to next hop Azure Firewall.
- The VM answers the request, reversing source and destination IP addresses. The UDR to App gateway subnet captures the packet sent back to the Application Gateway and redirects it to Azure Firewall, while preserving the destination IP toward the Application Gateway.
- Here again the Azure Firewall doesn't SNAT the traffic, since it's going to a private IP address, and forwards the traffic to the Application Gateway.
- Finally, the Application Gateway instance answers the client.
- Outbound flows from the VMs to the public internet go through Azure Firewall, as defined by the UDR to 0.0.0.0/0.
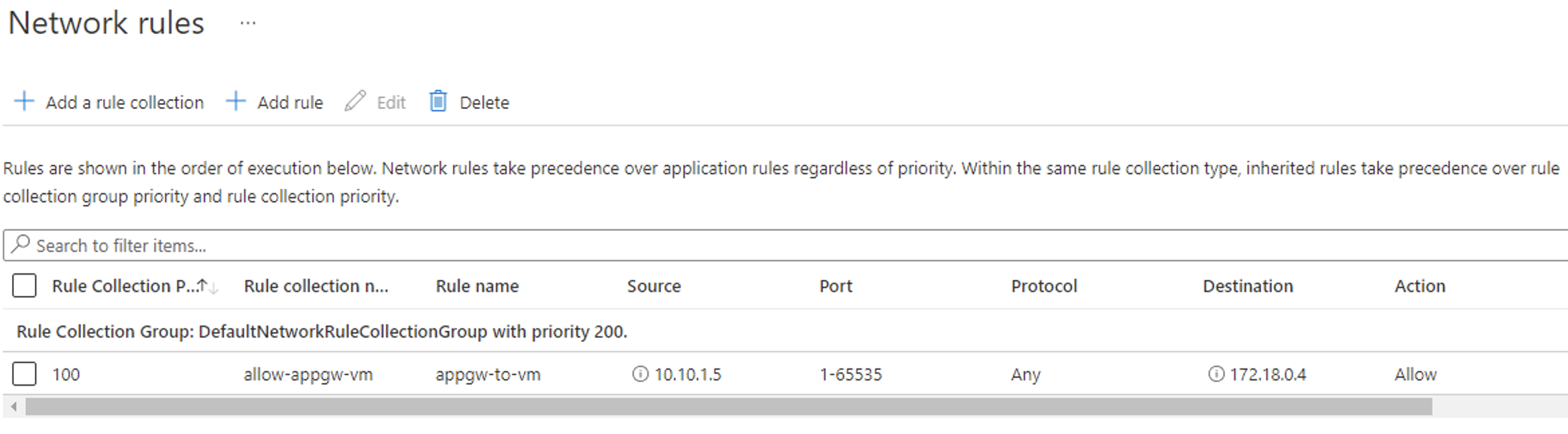
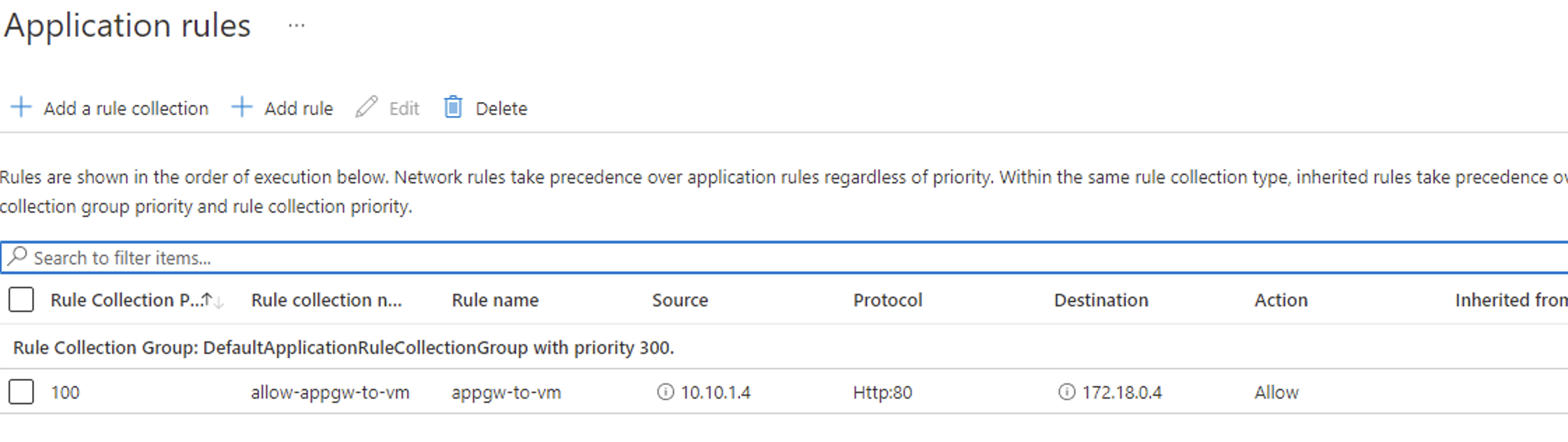
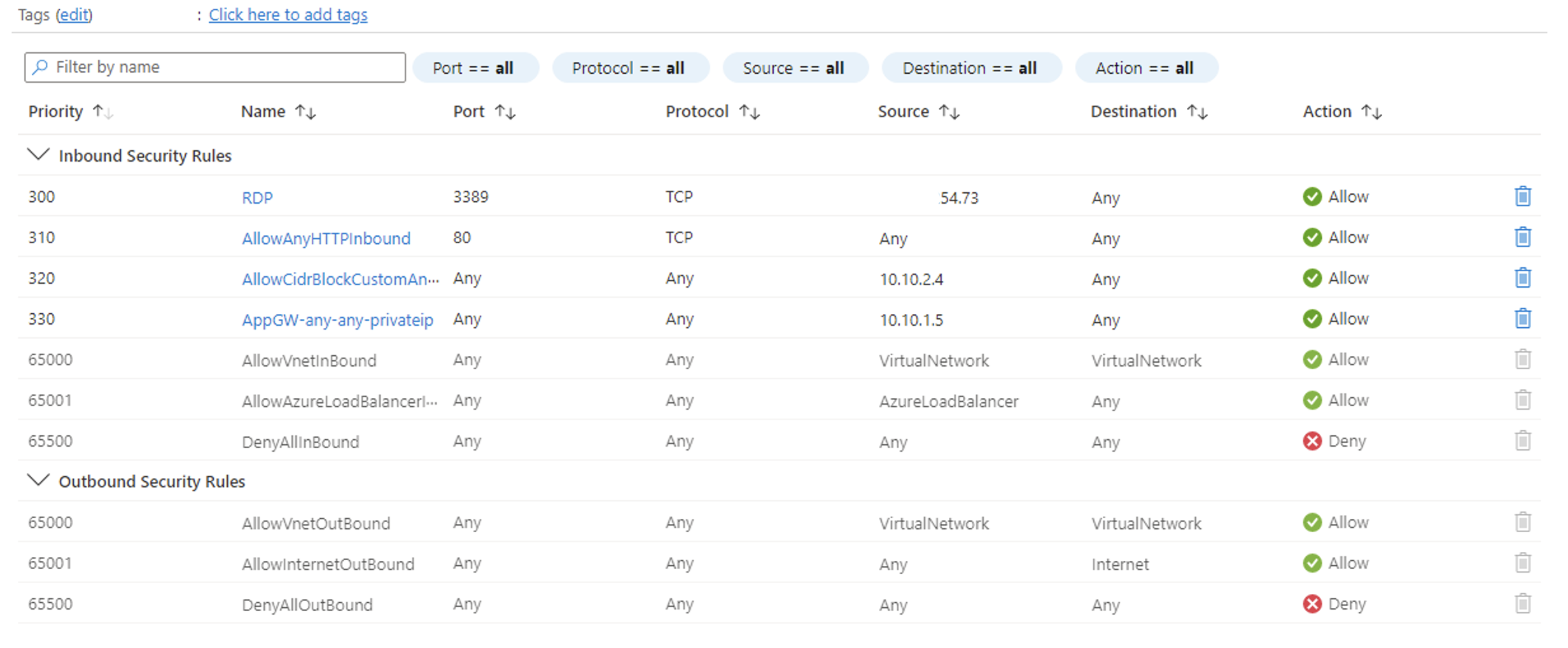
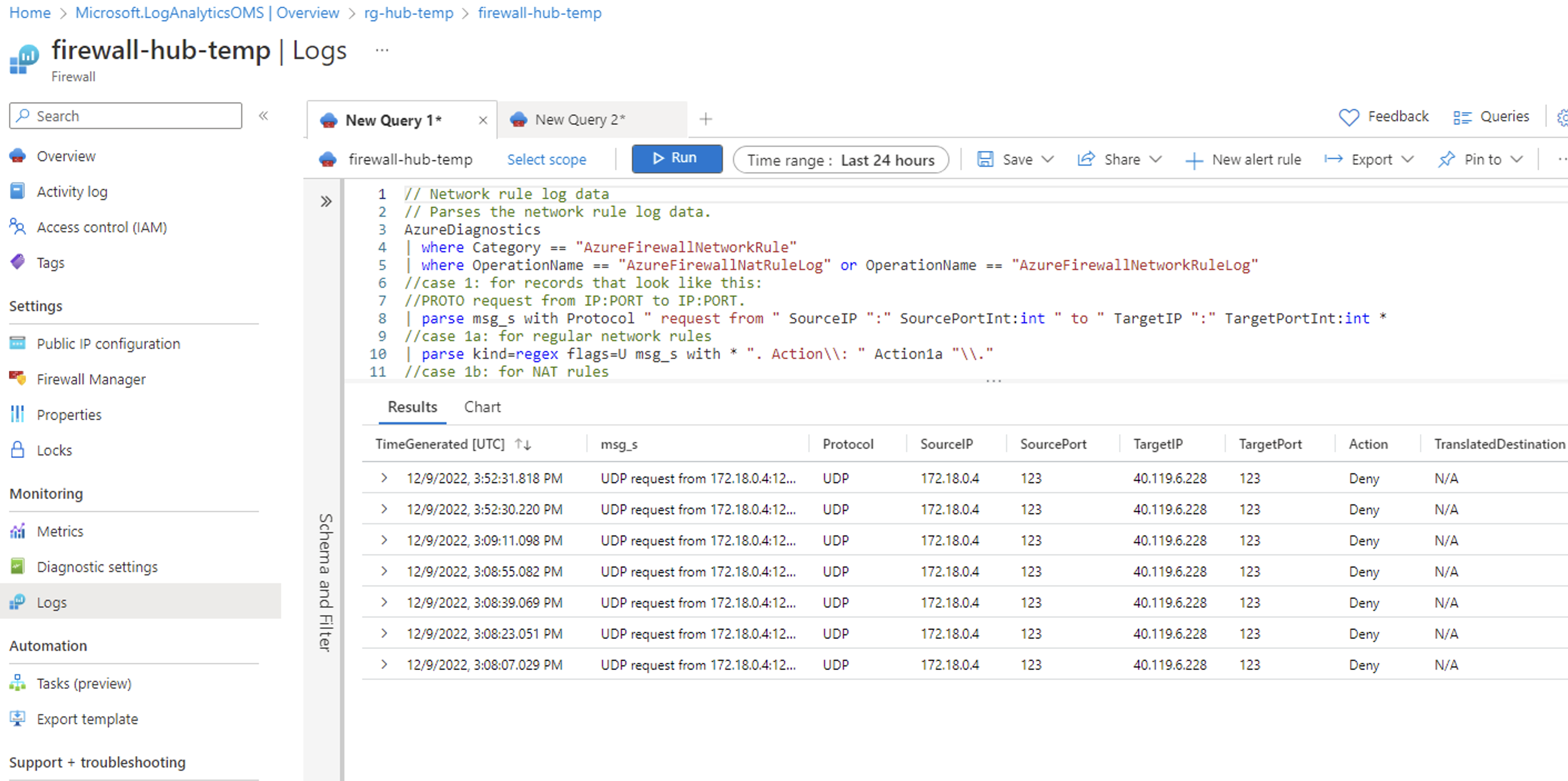
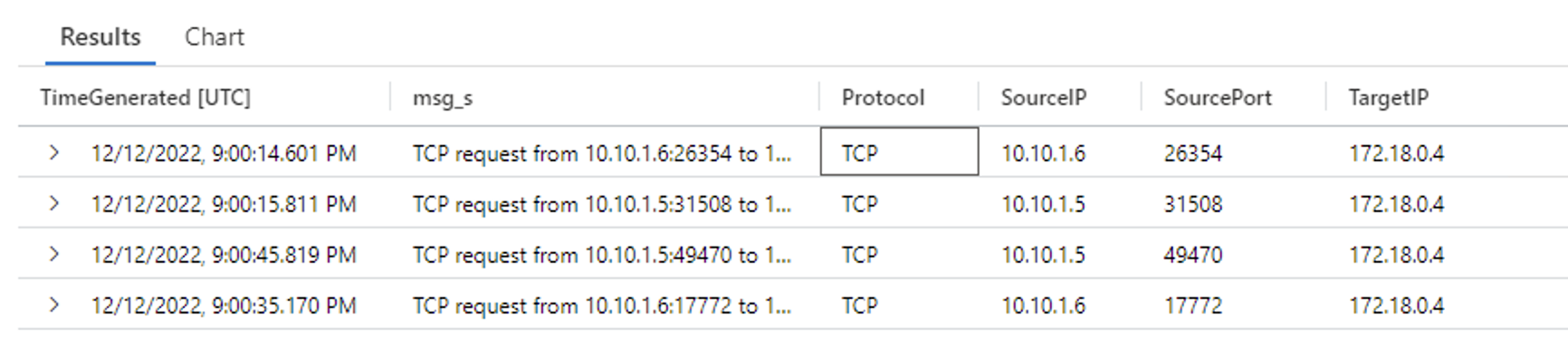
Looking at your setup, it looks like the UDR setup is configured properly but it is not clear if you have configured Network rules within your Azure Firewall to allow traffic from the Application gateway instance.
You need to make sure that the Azure Firewall has the required network and application rules allowing the Source IP address of your Application gateway i.e. 10.10.1.5 to destination IP address of your VM in the peered spoke Vnet i.e. 178.18.0.10.
I would request you to check if this traffic is allowed within your Azure Firewall via a Network rule. If not, please configure it and try again.
Kindly let us know if the above helps or you need further assistance on this issue.
----------------------------------------------------------------------------------------------------------------
Please "Accept the answer" if the information helped you. This will help us and others in the community as well.