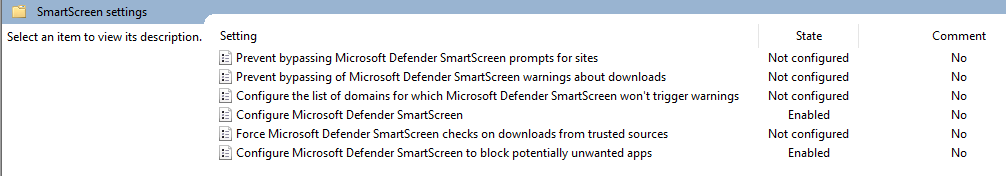
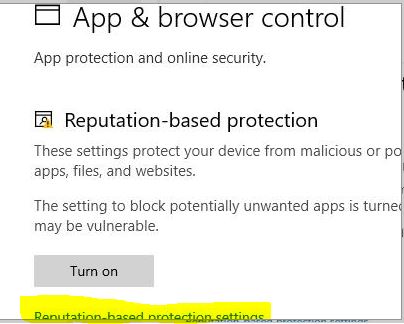
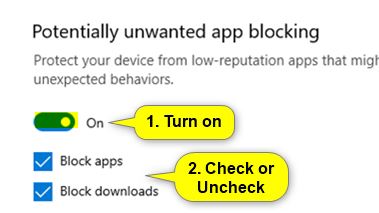
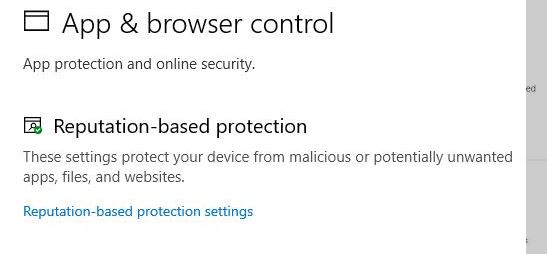
Ok so I tried adding the Edge admin templates and it made no difference. I decided to spend (waste) my time finding this and after much trial and error, I found that it is in fact this: Computer > Policy > Admin > Windows Components > Windows Defender Smartscreen > Explorer > Configure Windows defender Smartscreen Turning this on, enables this setting. I will note that I had to install May and October 2020 admin templates in. May 2020 https://www.microsoft.com/en-us/download/101445 October 2020 https://www.microsoft.com/en-us/download/details.aspx?id=102157 You may have to restart the PC for this to apply - GPUPDATE /FORCE does not apply it ![43716-screenshot-2020-11-30-170204.jpg][1] [1]: /api/attachments/43716-screenshot-2020-11-30-170204.jpg?platform=QnA