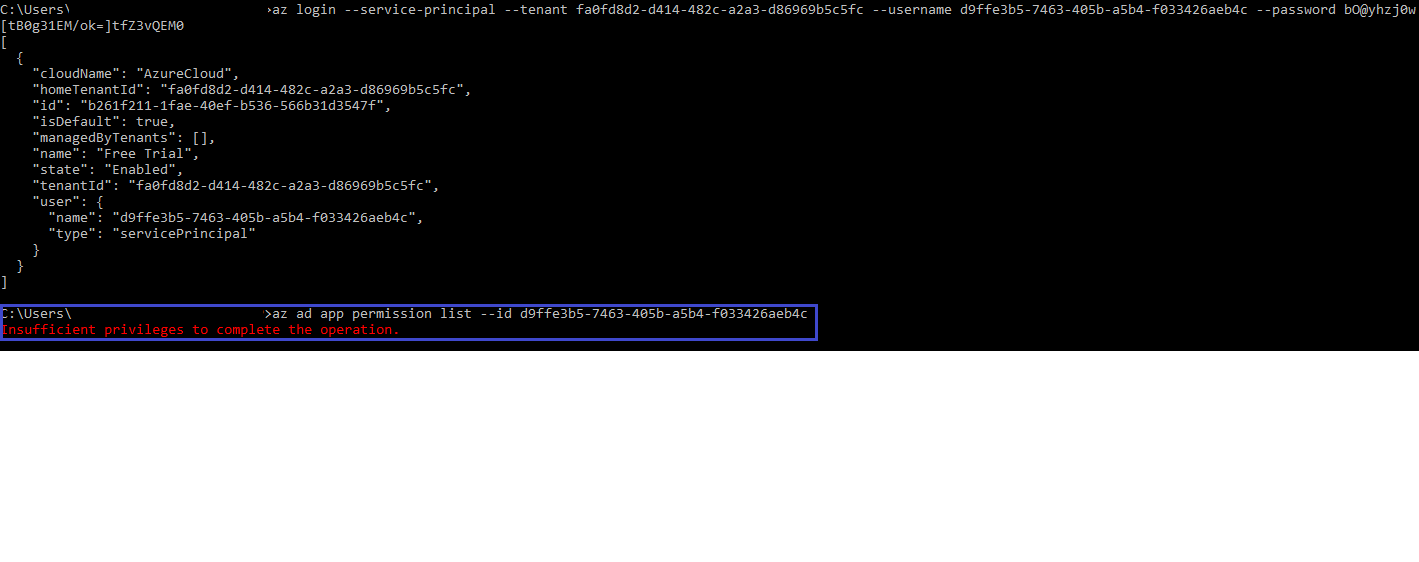
Hello @Anchal Madankar ,
when you registered the service principal an app would have been registered there in your azure AD tenant . You require to logon to Azure Portal with Global admin account so that you can make this modification . In case you are not the global admin , you will need to contact your internal IT team who would have global administrator rights within your tenant . With the app registrations section , you will need to go to API permissions to provide the application API permissions it needs to list the information. Please take a look at the screenshots below.
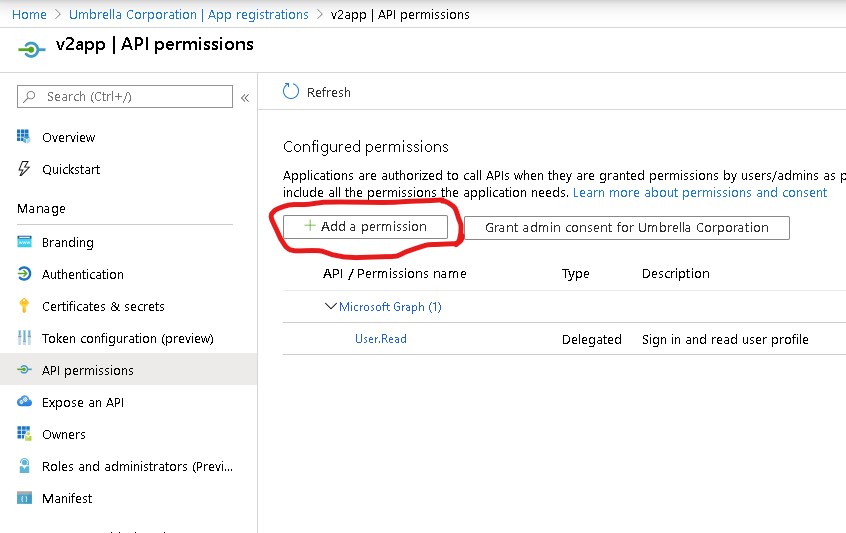
This will open a left pane listing all the APIs available along with any APis your organization is using or have created.
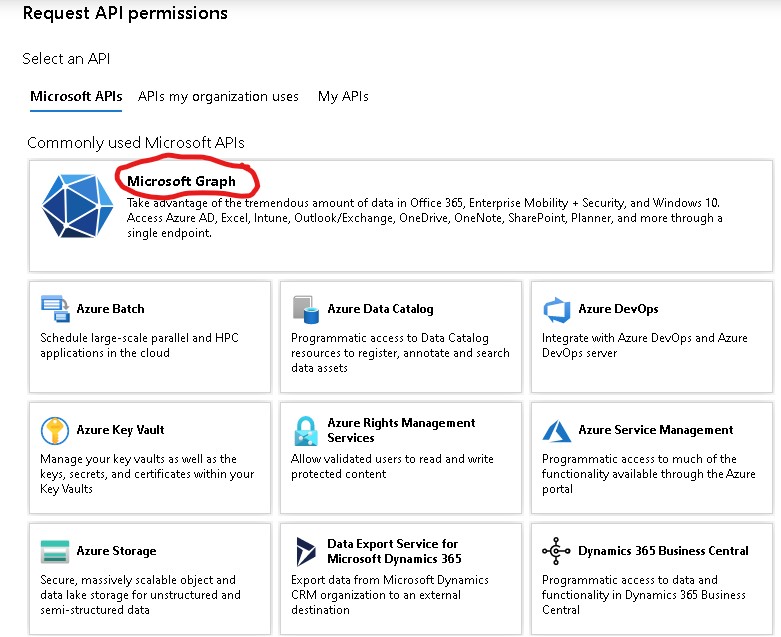
I am not sure which type of application do u have but you can request for delegated permissions for your application/service principal or app permissions depending upon the details as mentioned .
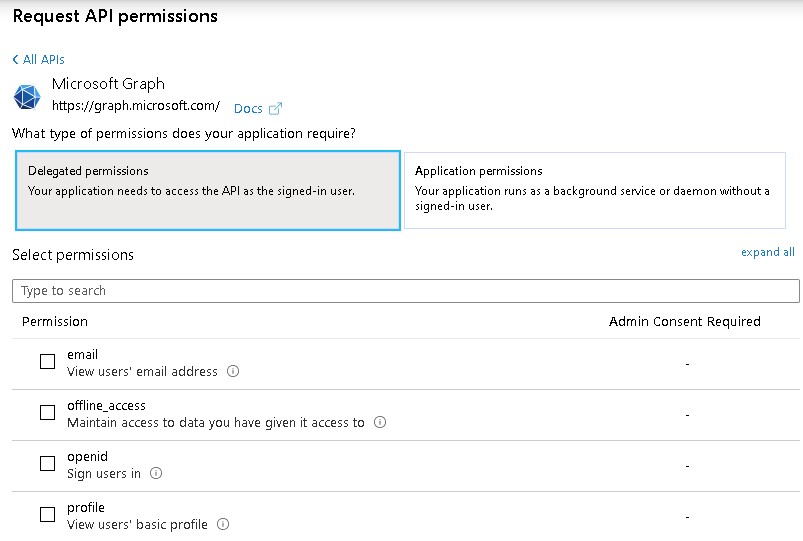
With the details that you have provided in the screenshot , I am assuming you would need application object permissions as below. But I am not sure of your needs so you may have to check the existing permissions on the graph API to find what fits your need.
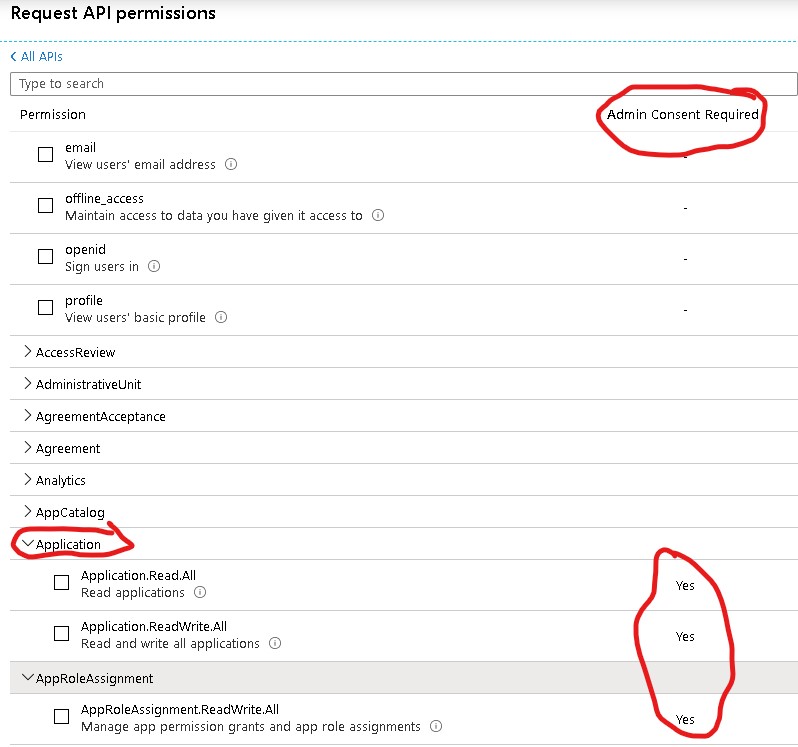
Anything that says Admin consent requires would require you to first set all the permissions and contact global admin for tenant wide consent . The global admin would need to logon to azure portal and go to this app within App registrations blade and provide the admin consent by clicking "**Grant Admin consent to tenant **"as shown in the first image here . You can read more about permissions and consent here.
Hope this helps. In case the information provided in this post helps you , please do accept this as answer so that its helpful for other members of the community searching for similar answers . In case you have any queries , please do let us know.
Thank you.