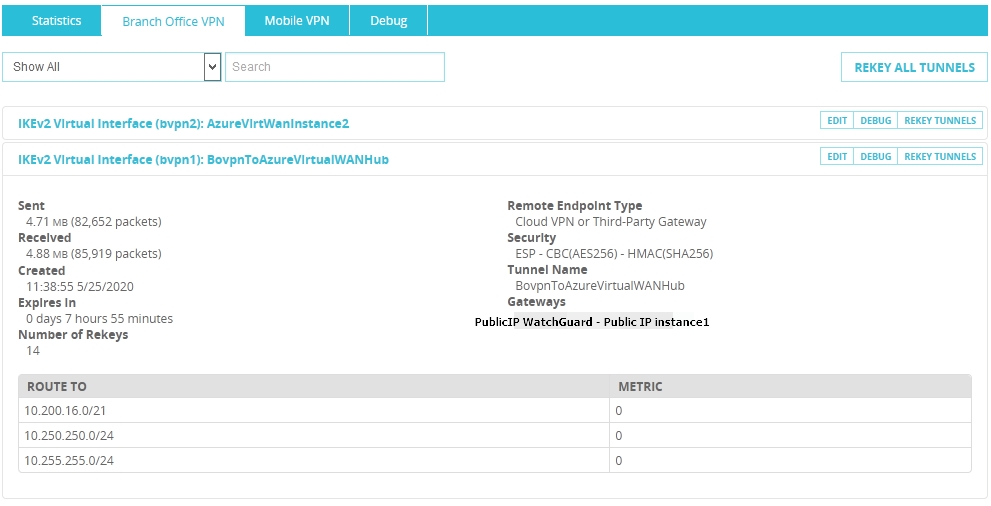
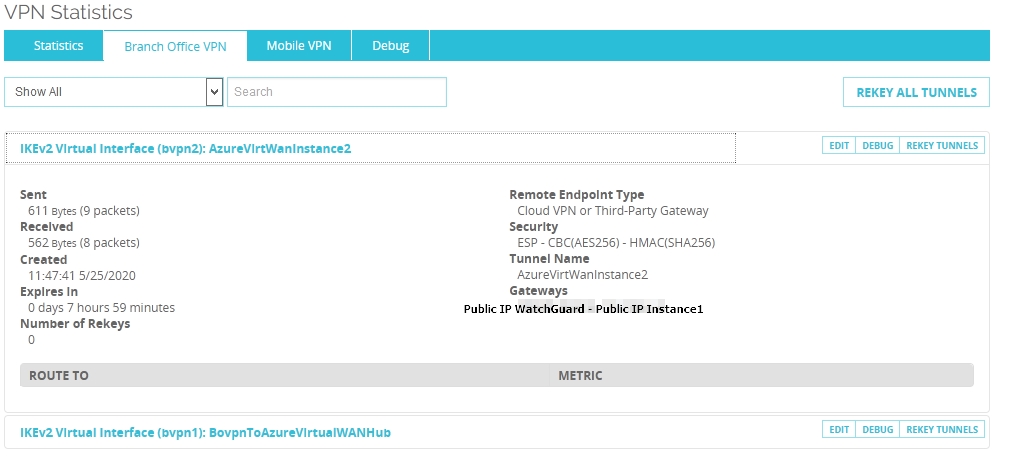
To your last question, whether WatchGuard is supported or not, looking at the standalone VPN docs (https://learn.microsoft.com/azure/vpn-gateway/vpn-gateway-about-vpn-devices) it looks like WatchGuard is supported for RouteBased configurations starting at OS version 11.12x.
I am not sure I understand the problem you are having though: if you have two instances on Azure (instance0 and instance1) and one WatchGuard on-prem (let's call it watchguard0), you should have 2 IPsec tunnels up and running: instance0<->watchguard0 and instance1<->watchguard0. I am assuming that both IPsec tunnels are up.
If the IPsec tunnels are up, the next configuration is about routing: you should have 2 BGP adjacencies up: instance0<->watchguard0, and instance1<->watchguard0. You say that only one instance (instance0? instance1?) receives BGP routes, but not the other. How do you see this? Are both BGP adjacencies up, as seen from the WatchGuard appliance? I would guess from your problem description that you only see one BGP adjacency up.
The fact that when you shutdown one tunnel, then everything works on the other one is interesting: could it be that the WatchGuard sends a different BGP router ID depending on the tunnel? From a Virtual WAN perspective, we expect the remote device (the WatchGuard in your case) to show the same public IP address and the same BGP IP address on both tunnels. Interestingly enough in the WatchGuard config example (https://www.watchguard.com/help/docs/help-center/en-US/Content/en-US/Fireware/bovpn/manual/bovpn_vif_dynamic_routing_azure.html) they do not have a line in their config to have a fixed BGP router ID, with other vendors you would have that (you can see an example for the Cisco CSR here (note line #62): https://github.com/erjosito/azure-wan-lab/blob/master/csr_config_2tunnels_tokenized.txt).