@VD That functionality is not built into Microsoft.Data.SqlClient today.
But I get your point and see that it would be a useful feature to have. I would request you to create a feature request here
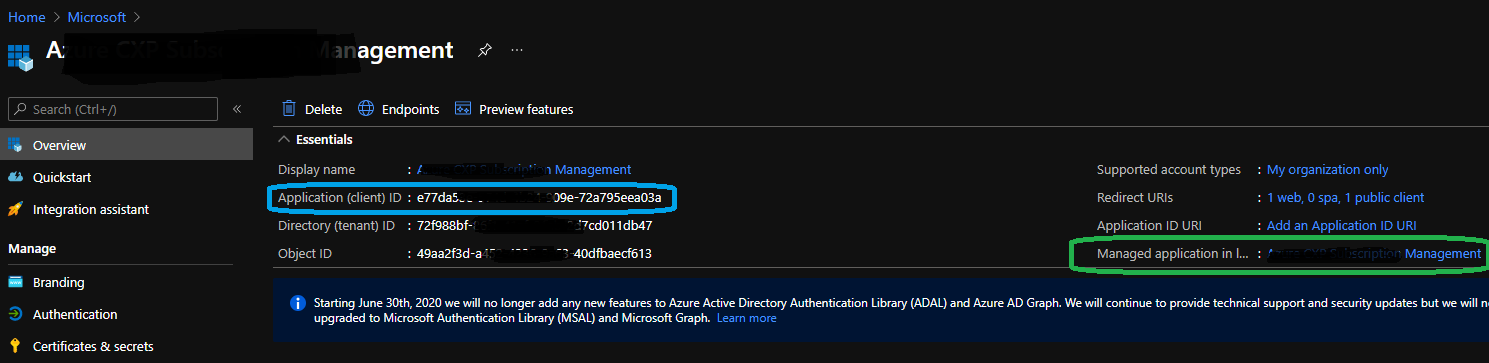
Regarding acquiring access token using ClientSecret or AuthenticationContext, specifying the TenantId is optional in case of single tenant application.
This is because the SDK can determine the service principal (highlighted in Green) and tenant based on the clientId (highlighted in blue) you provide.
You can check this relationship from the Azure portal on the Overview blade of your AD Application.
Do let me know if you have further questions.
----------
If an answer is helpful, please "Accept answer" or "Up-Vote" for the same which might be beneficial to other community members reading this thread.