I have a big problem that I need some help, please.
I have a Windows domain with AD and it has 10 DC in different networks. I have one specific user that after he changed it's password he is getting locked out (password expiration due date).
Looking at the logs I found 2 machines he was "disconnected" in the RDP and I logged him out from there. Logs were saying explicitly the machine name so it was easy and the domain controller for that region let's call DC4. I just logged him out and not more logs saying about those 2 machines.
But he is still getting locked out in the DC5 and the logs say just the computer name of the domain controller and of course he is not logged in there.
We have many integrations with others applications, using LDAP protocol to authenticate users, etc... we basically use the AD users/groups for everything.
I tried using wireshark to see some logs but wasn't lucky, maybe I just used a bad filter search, but for some integrations I have LDAPS...
We reverted his password back to the one before all of this started and he is fine of course, but we need to figure this out.
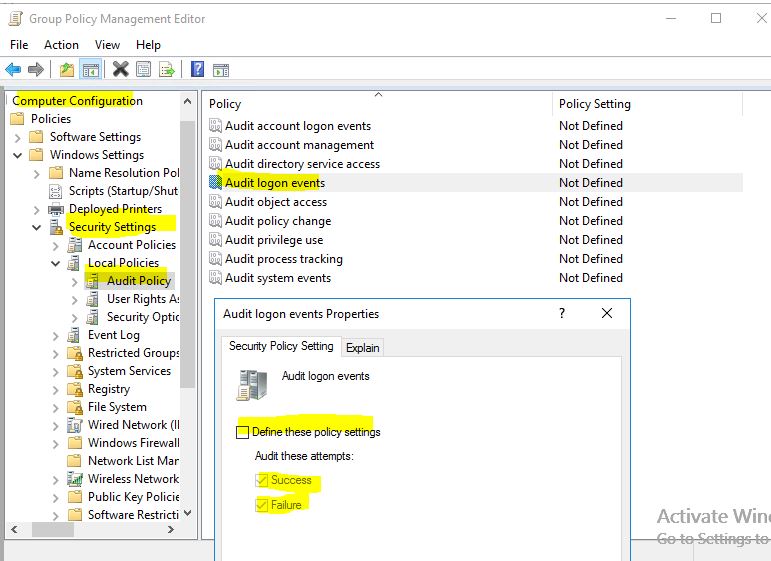
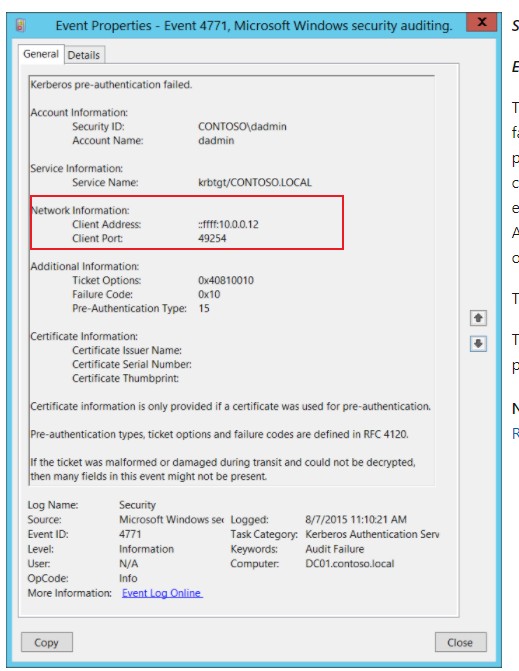
So, is there another way to check the real source of blocking an account? In the Windows Logs I was looking for event ID 4740 and 4771. For the DC4 it has only the 4740 what just says the DC4 itself. I asked him to check for any script or something he has using his account but he said nothing he remembers.
Any recommendation you guys have? I've tried different tools, like Account Lockout Status
A user account was locked out.
Subject:
Security ID: SYSTEM
Account Name: DC4$
Account Domain: DOMAIN
Logon ID: 0x3E7
Account That Was Locked Out:
Security ID: DOMAIN\user_here
Account Name: user_here
Additional Information:
Caller Computer Name: DC4
Thank you!