@JamesTran-MSFT He is following acticle https://learn.microsoft.com/en-us/windows-server/identity/ad-fs/operations/configure-authentication-policies
Look under "To configure MFA per-relying party trust that is based on a user's group membership data", if you copy and paste the code there is a formatting issue.
configuring ADFS for MFA windonws 2019
Hi Team,
I was trying configure MFA per-relying party trust that is based on a user's group membership data
$MfaClaimRule = "c:[Type == '"https://schemas.microsoft.com/ws/2008/06/identity/claims/groupsid'", Value =~ '"^(?i) <group_SID>$'"] => issue(Type = '"https://schemas.microsoft.com/ws/2008/06/identity/claims/authenticationmethod'", Value '"https://schemas.microsoft.com/claims/multipleauthn'");"
above command is not working. 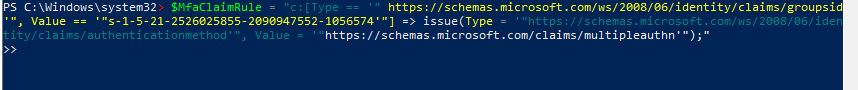
2 answers
Sort by: Most helpful
-
Geoff 6 Reputation points
2021-03-29T16:37:55.983+00:00 -
Geoff 6 Reputation points
2021-03-29T19:54:10.983+00:00 Here is the proper format that should work for you
$MfaClaimRule = 'c:[Type == "https://schemas.microsoft.com/ws/2008/06/identity/claims/groupsid", Value == "S-1-5-21-2526025855-2090947552-105674"] => issue(Type = "https://schemas.microsoft.com/ws/2008/06/identity/claims/authenticationmethod", Value = "https://schemas.microsoft.com/claims/multipleauthn");'
Set-AdfsAdditionalAuthenticationRule $MfaClaimRule
