Thank you for reaching out to Microsoft Q&A. I understand that you are trying to connect Azure Route Based VPN to Cisco ASA which is using a Policy based VPN and with this setup you are only able to connect to one of the subnets and not the other.
In order to work around this, configure Azure route-based VPN gateways to use prefix-based traffic selectors with option "PolicyBasedTrafficSelectors", to connect to on-premises policy-based VPN devices. This capability allows you to connect from an Azure virtual network and VPN gateway to multiple on-premises policy-based VPN/firewall devices, removing the single connection limit from the current Azure policy-based VPN gateways.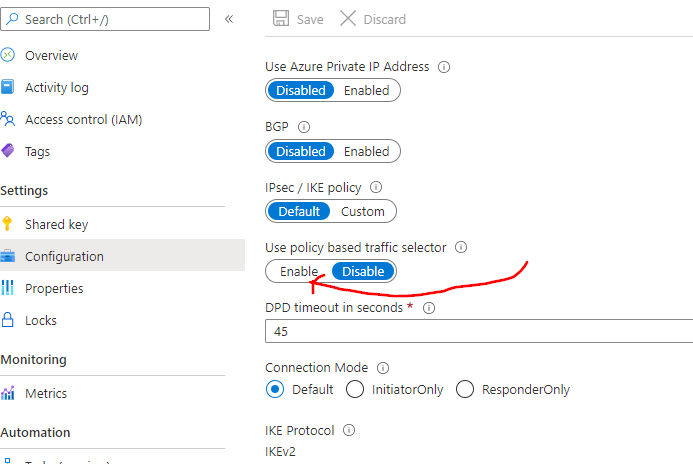
Hope this helps. Please let us know if you have any further questions and we will be glad to assist you further. Thank you!
Remember:
Please accept an answer if correct. Original posters help the community find answers faster by identifying the correct answer. Here is how.
Want a reminder to come back and check responses? Here is how to subscribe to a notification.