Hello @StarGazer ,
By chance, only yesterday I was playing with developing a tool that analyses and verifies Authenticode signatures and hashes (including page hashes, but completely ignoreing certificate chain policies), so I was interested to see your message.
Many thanks for providing such safe examples! A program whose sole code consists of "xor eax,eax" and "ret" meant that I had no objections to running and testing you sample code :-)
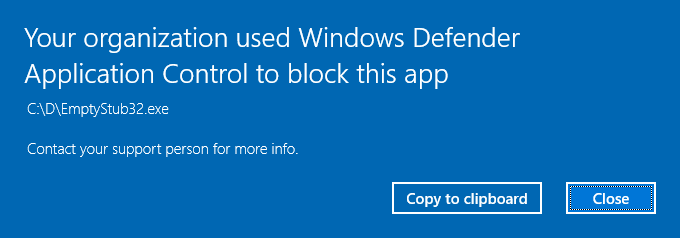
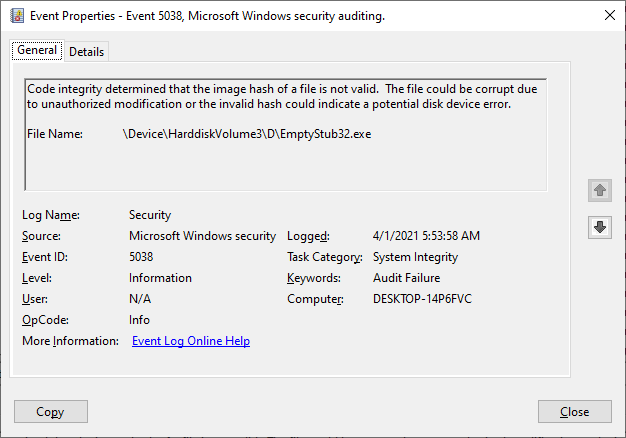
I traced the attempted program activation with the Microsoft-Windows-CodeIntegrity provider and enabled stack traces for the events. The trace shows VerificationError = 7, where 7 means "Invalid root certificate" and did a bit more research (but have not yet tried kernel debugging - it takes a long time for me to set that up at home). I think that you are probably correct that a Windows driver type signature policy must be observed.
I still have a Windows 8.0 test system and the two images with IMAGE_DLLCHARACTERISTICS_FORCE_INTEGRITY fail there too and in the same way.
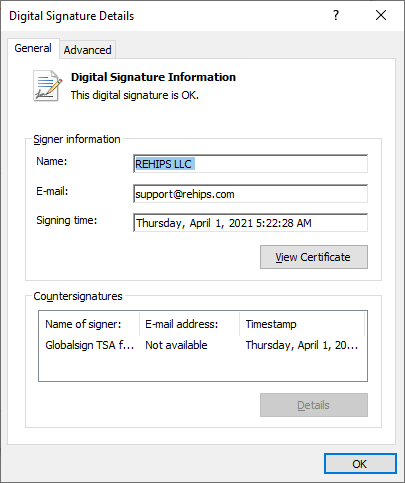
During my search of the web, someone mentioned that bcrypt.dll is a (rare) example of a Windows image that has IMAGE_DLLCHARACTERISTICS_FORCE_INTEGRITY set. Since this is signed with a Microsoft certificate the following observation is probably not useful (or unexpected), but this Authenticode signature does pass kernel-mode driver signing policy checks.
Gary