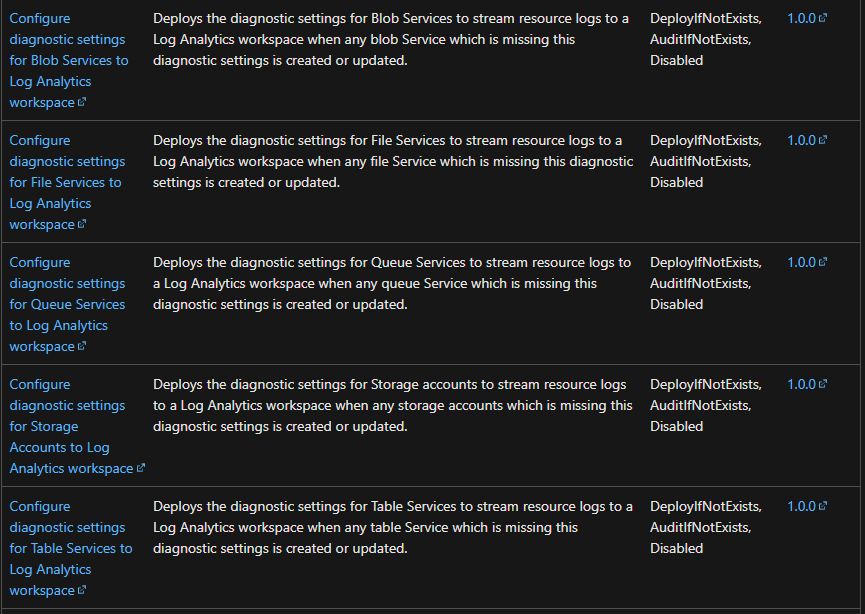
Yes I ended up creating custom policy with each different service type (blob, table, file, queue) to make it more manageable. The main change from the built-in policy is that the parameter "resourcename" in the deployment needs to be changed to refer to the full name "<storageAccountName>/default"
Azure Policy Storage Account Diagnostic Logging

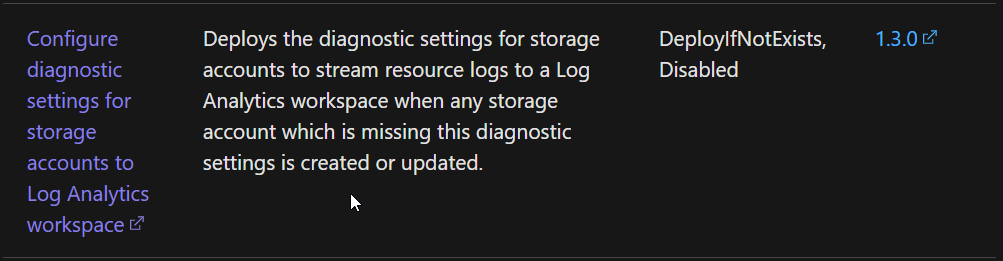
I have been struggling to get this policy to fully check that blob, file, Queue, and Table services are properly configured with diagnostic settings. The end result would be to ensure each storage service has diagnostic logging being sent to a log analytics workspace for StorageRead, StorageWrite, and StorageDelete categories. To note this is using the newer method described in [https://learn.microsoft.com/en-us/azure/storage/blobs/monitor-blob-storage?tabs=azure-porta][1]l Also this could be an issue on the azure side, however it is unclear to me from this article if that is true or not. [https://github.com/azure/azure-policy#resource-type-not-correctly-published-by-resource-provider][2] The main issue I have been trying to solve is the logic to detect this across all blob services. The deployment logic works fine, its just the compliance check part to ensure blob, file, Queue, and Table services are enabled. Currently the below returns: (full policy attached as well) No related resources match the effect details in the policy definition. (Error code: Not Found) ["policyRule": { "if": { "field": "type", "equals": "Microsoft.Storage/storageAccounts" }, "then": { "effect": "[parameters('effect')]", "details": { "type": "Microsoft.Insights/diagnosticSettings", "existenceCondition": { "allOf": [ { "count": { "field": "Microsoft.Insights/diagnosticSettings/logs[]", "where": { "allOf": [ { "field": "Microsoft.Insights/diagnosticSettings/logs[].category", "in": [ "StorageRead", "StorageWrite", "StorageDelete" ] }, { "field": "Microsoft.Insights/diagnosticSettings/logs[*].enabled", "equals": "[parameters('logsEnabled')]" } ] } }, "greater": 0 }, { "field": "Microsoft.Insights/diagnosticSettings/workspaceId", "equals": "[parameters('logAnalytics')]" } ] },][3] [1]: https://learn.microsoft.com/en-us/azure/storage/blobs/monitor-blob-storage?tabs=azure-porta [2]: https://github.com/azure/azure-policy#resource-type-not-correctly-published-by-resource-provider [3]: /api/attachments/85864-storage-logging-policy.txt?platform=QnA
2 answers
Sort by: Most helpful
-
-
Varun Sharma 81 Reputation points
2022-05-09T17:22:38.093+00:00 Yes the deployment needs to be updated to fullname (<storageAccountName>/default) rather than the service name (default)
"resourceName": {
"value": "[field('fullname')]"
}and update the name in the deployment from
"name": "[concat(parameters('resourceName'), '/default/', 'Microsoft.Insights/', parameters('diagnosticsSettingNameToUse'))]",
to
"name": "[concat(parameters('resourceName'),'/', 'Microsoft.Insights/', parameters('diagnosticsSettingNameToUse'))]",
here is an e.g. for blob and you can modify it to use for others
{
"properties": {
"displayName": "Configure diagnostic settings for blob services",
"policyType": "Custom",
"mode": "All",
"description": "Deploys the diagnostic settings for storage account blob services to stream resource logs to a Log Analytics workspace when any storage account blob service which is missing these diagnostic settings is created or updated.",
"metadata": {
"category": "Storage"
},
"parameters": {
"logAnalytics": {
"type": "String",
"metadata": {
"displayName": "Log Analytics workspace",
"description": "Specify the Log Analytics workspace the storage account should be connected to.",
"strongType": "omsWorkspace",
"assignPermissions": true
}
},
"diagnosticsSettingNameToUse": {
"type": "String",
"metadata": {
"displayName": "Setting name",
"description": "Name of the diagnostic settings."
},
"defaultValue": "storageAccountsDiagnosticsLogsToWorkspace"
},
"effect": {
"type": "String",
"metadata": {
"displayName": "Effect",
"description": "Enable or disable the execution of the policy"
},
"allowedValues": [
"DeployIfNotExists",
"Disabled"
],
"defaultValue": "DeployIfNotExists"
},
"StorageDelete": {
"type": "String",
"metadata": {
"displayName": "StorageDelete - Enabled",
"description": "Whether to stream StorageDelete logs to the Log Analytics workspace - True or False"
},
"allowedValues": [
"True",
"False"
],
"defaultValue": "True"
},
"StorageWrite": {
"type": "String",
"metadata": {
"displayName": "StorageWrite - Enabled",
"description": "Whether to stream StorageWrite logs to the Log Analytics workspace - True or False"
},
"allowedValues": [
"True",
"False"
],
"defaultValue": "True"
},
"StorageRead": {
"type": "String",
"metadata": {
"displayName": "StorageRead - Enabled",
"description": "Whether to stream StorageRead logs to the Log Analytics workspace - True or False"
},
"allowedValues": [
"True",
"False"
],
"defaultValue": "True"
},
"Transaction": {
"type": "String",
"metadata": {
"displayName": "Transaction - Enabled",
"description": "Whether to stream Transaction logs to the Log Analytics workspace - True or False"
},
"allowedValues": [
"True",
"False"
],
"defaultValue": "True"
}
},
"policyRule": {
"if": {
"field": "type",
"equals": "Microsoft.Storage/storageAccounts/blobServices"
},
"then": {
"effect": "[parameters('effect')]",
"details": {
"type": "Microsoft.Insights/diagnosticSettings",
"roleDefinitionIds": [
"/providers/microsoft.authorization/roleDefinitions/749f88d5-cbae-40b8-bcfc-e573ddc772fa",
"/providers/microsoft.authorization/roleDefinitions/92aaf0da-9dab-42b6-94a3-d43ce8d16293"
],
"existenceCondition": {
"allOf": [{
"anyOf": [{
"field": "Microsoft.Insights/diagnosticSettings/metrics.enabled",
"equals": "True"
},
{
"field": "Microsoft.Insights/diagnosticSettings/logs.enabled",
"equals": "True"
}
]
},
{
"field": "Microsoft.Insights/diagnosticSettings/workspaceId",
"equals": "[parameters('logAnalytics')]"
}
]
},
"deployment": {
"properties": {
"mode": "incremental",
"template": {
"$schema": "http://schema.management.azure.com/schemas/2015-01-01/deploymentTemplate.json#",
"contentVersion": "1.0.0.0",
"parameters": {
"diagnosticsSettingNameToUse": {
"type": "string"
},
"resourceName": {
"type": "string"
},
"logAnalytics": {
"type": "string"
},
"location": {
"type": "string"
},
"Transaction": {
"type": "string"
},
"StorageRead": {
"type": "string"
},
"StorageWrite": {
"type": "string"
},
"StorageDelete": {
"type": "string"
}
},
"variables": {},
"resources": [{
"type": "Microsoft.Storage/storageAccounts/blobServices/providers/diagnosticSettings",
"apiVersion": "2017-05-01-preview",
"name": "[concat(parameters('resourceName'),'/', 'Microsoft.Insights/', parameters('diagnosticsSettingNameToUse'))]",
"location": "[parameters('location')]",
"dependsOn": [],
"properties": {
"workspaceId": "[parameters('logAnalytics')]",
"metrics": [{
"category": "Transaction",
"enabled": "[parameters('Transaction')]",
"retentionPolicy": {
"days": 0,
"enabled": false
},
"timeGrain": null
}],
"logs": [{
"category": "StorageRead",
"enabled": "[parameters('StorageRead')]"
},
{
"category": "StorageWrite",
"enabled": "[parameters('StorageWrite')]"
},
{
"category": "StorageDelete",
"enabled": "[parameters('StorageDelete')]"
}
]
}
}],
"outputs": {}
},
"parameters": {
"diagnosticsSettingNameToUse": {
"value": "[parameters('diagnosticsSettingNameToUse')]"
},
"logAnalytics": {
"value": "[parameters('logAnalytics')]"
},
"location": {
"value": "[field('location')]"
},
"resourceName": {
"value": "[field('fullname')]"
},
"Transaction": {
"value": "[parameters('Transaction')]"
},
"StorageDelete": {
"value": "[parameters('StorageDelete')]"
},
"StorageWrite": {
"value": "[parameters('StorageWrite')]"
},
"StorageRead": {
"value": "[parameters('StorageRead')]"
}
}
}
}
}
}
}
}
}