I have implemented JWT bearer tokens and it is working for my APIs. However, with the code implemented I have a slight issue. When I implement the code below it does not seem that my user is authenticating.
services.AddAuthentication(JwtBearerDefaults.AuthenticationScheme)
.AddJwtBearer(options =>
{
options.TokenValidationParameters = new TokenValidationParameters
{
ValidateIssuer = true,
ValidateAudience = true,
ValidateLifetime = true,
ValidateIssuerSigningKey = true,
ValidIssuer = Configuration["Jwt:Issuer"],
ValidAudience = Configuration["Jwt:Issuer"],
IssuerSigningKey = new SymmetricSecurityKey(Encoding.UTF8.GetBytes(Configuration["Jwt:Key"]))
};
});
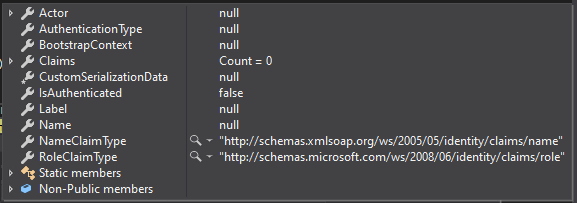
This is what happens with the code in my startup.cs

This is what happens if I uncomment that section.
Any idea where the issue might be?