Hi, @Maccari Fabio in my opinion, your token is correct and the issue should come from your api validation. According to this section, after enabling bearer token validation in your api program, aud claim will be validated at first. Hence we need to set Audience in appsettings.json. Here I set up a asp.net core mvc program to test it. It worked well and please refer to my code snippet below:
appsettings.json need to add these:
"AzureAd": {
"Instance": "https://login.microsoftonline.com/",
"ClientId": "2c0e06_xxxxxxx_df157",
"Domain": "tenant_name.onmicrosoft.com",
"TenantId": "common",
"Audience": "client_id_that_expose_api"//you can get it by decoding access token and the aud claim
}
StartUp.cs need to modify ConfigurationServices and Configure
public void ConfigureServices(IServiceCollection services)
{
services.AddMicrosoftIdentityWebApiAuthentication(Configuration);
services.AddControllersWithViews();
}
app.UseRouting();
// adding next 2 lines in Configure method
app.UseAuthentication();
app.UseAuthorization();
app.UseEndpoints(endpoints =>
{
endpoints.MapControllerRoute(
name: "default",
pattern: "{controller=Home}/{action=Index}/{id?}");
});
And this is my controller:
using Microsoft.AspNetCore.Authorization;
using Microsoft.AspNetCore.Mvc;
using Microsoft.Identity.Web.Resource;
using WebApplication1.Models;
namespace WebApplication1.Controllers
{
[Authorize]
public class HelloController : Controller
{
public IActionResult Index()
{
HttpContext.ValidateAppRole("Tiny.Read");
Student stu = new Student();
stu.age = 18;
return Json(stu) ;
}
}
}
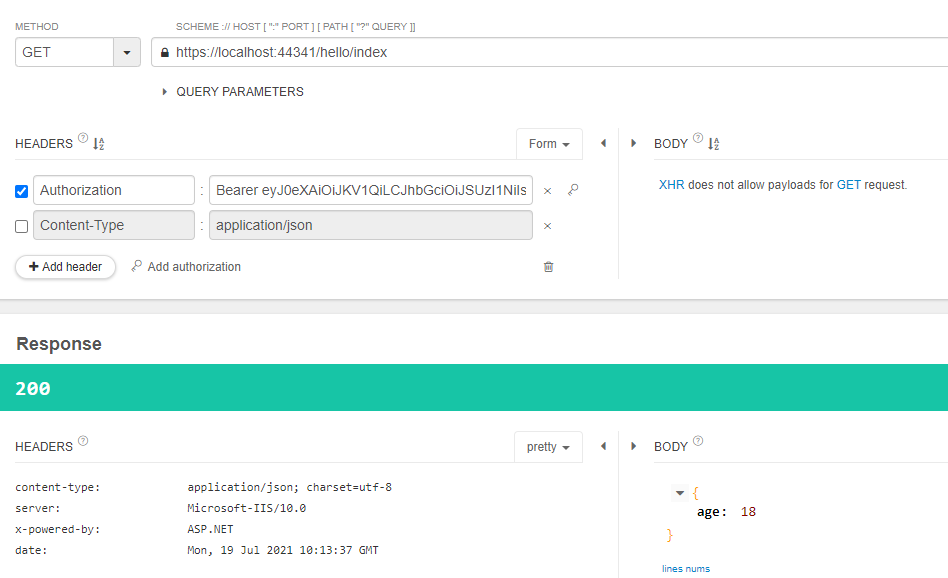
This is my testing result:
If the answer is helpful, please click "Accept Answer" and upvote it.
Note: Please follow the steps in our documentation to enable e-mail notifications if you want to receive the related email notification for this thread.
Best Regards,
TinyWang