I am seeking clarity as to how Key Vault Managed Storage rotates the keys, as the documentation is rather confusing and I believe to be incorrect.
Key Vault Managed Storage can be enabled using the following commands:
- Azure Powershell: Add-AzKeyVaultManagedStorageAccount
- Azure CLI: az keyvault storage add
Regardless of the command used, you can specify a regeneration period in which the access keys get rotated/regenerated.
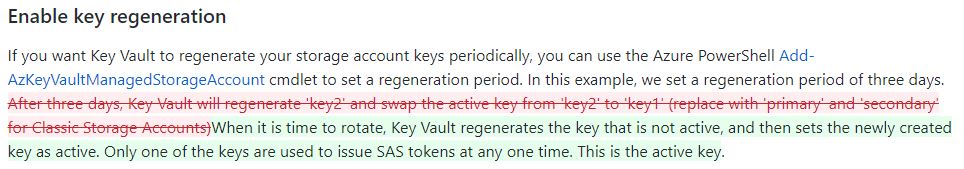
The documentation for the Azure Powershell method is found here - https://learn.microsoft.com/en-us/azure/key-vault/secrets/overview-storage-keys and states:
"Key Vault will regenerate 'key2' and swap the active key from 'key2' to 'key1' (replace with 'primary' and 'secondary' for Classic Storage Accounts)."
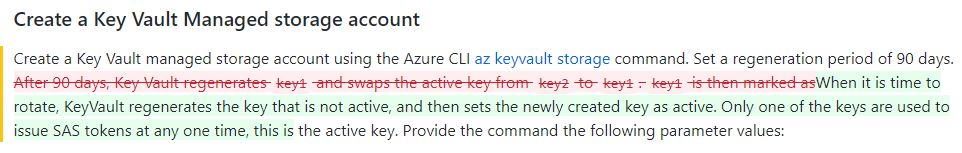
The documentation for the CLI method is found here: https://learn.microsoft.com/en-us/azure/key-vault/secrets/overview-storage-keys and states:
"Key Vault regenerates key1 and swaps the active key from key2 to key1. key1 is then marked as the active key."
My issue is that both methods refer to swapping 'the active key from key2', yet in both of the examples on both pages, key1 is used as the active key. Therefore implying that key2 is always active, even though you appear to set which key is active within both method calls.
Additionally, the methods differ in which key they regenerate. The Powershell method regenerates key2 and the CLI method regenerates key1. I'm curious as to why this is the case or if it even is the case.
I have since found a StackOverflow comment which I think is closer to what is probably happening: https://stackoverflow.com/questions/47776434/azure-managed-storage-account-keys and states:
"Only one of the keys are used to issue SAS tokens at any one time. This is the active key. When it is time to rotate, KeyVault regenerates the key that is not active, and then sets the newly created key as active."
If the above is true, then a random comment from StackOverflow is more clearly describing what is going on and the documentation is wrong. I'm performing my own tests this weekend (the minimum regeneration period is 1 day - this appears to be undocumented too?).
I'm hoping to get some clarity.
Thanks,
Scott