@Dan
Thank you for the quick follow up on this and I apologize for the delayed response!
- When removing any existing IP addresses from your Policy, can you share a screenshot of the error message that you're receiving?
- When your list of IP addresses are blank, you mentioned that you're still denied. Are you denied access to your vault? Or are you denied from deploying the policy?
- When adding an IP address to your list, is everything working as expected on the Azure Key Vault side?
I created a JSON template on my end, and noticed that if you want to keep the allowed list of IP addresses blank, you should be able to remove the networkAcls section from your policy in order to allow all networks.
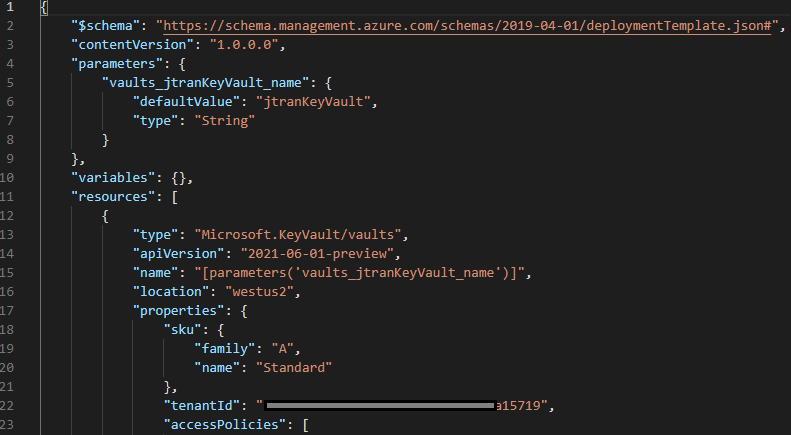
Allow all networks into your AKV:
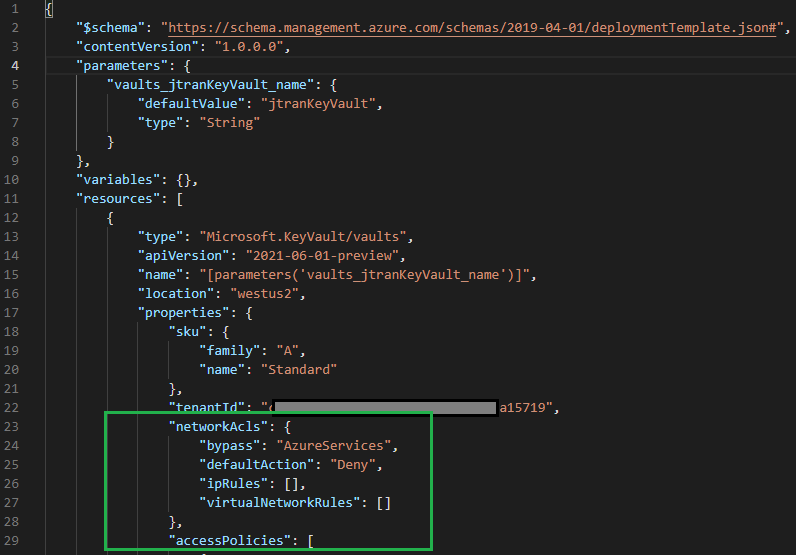
Restricting access to private endpoint and selected networks:
I hope this helps and if you have any other questions, please let me know.
Thank you for your time and patience throughout this issue!
----------
Please remember to "Accept Answer" if any answer/reply helped, so that others in the community facing similar issues can easily find the solution.
