We had the same issue, until we found this:
https://community.spiceworks.com/topic/277019-printer-deployment-via-group-policy-not-working
Windows failed to apply the Deployed Printer Connections settings.
I am experiencing an issue with Deployment of Printers from GPO. This just started last week after I replaced existing 2012r2 DC and 2012R2 Print Server with New 2019 DC and Print Server If a user had already gotten their printers from GPO they are present and work. If a user needs printers to load from GPO they will not. When we run gpupdate /force we get this "Windows failed to apply the Deployed Printer Connections settings. Deployed Printer Connections settings might have its own log file. Please click on the "More information" link."
All other GPOs are processing and working properly.
I have 4 other DCs (3 - 2012r2 and 1 -2019) and 3 other Print Servers (2 - 2012R2 and 1 - 2019) Workstations are all Win10 assorted flavors (1908 through 21H2)
Since I list all printers in the Directory. I can still install the printers manually from the Printer Servers through "Add Printer" and they install without issue even for none admin users.
Microsoft has really made a mess with this recent security update. Did they ever test this with GPO deployment of printers before dumping it out there?
Anyone else seeing this behavior? Has anyone fixed this behavior?
18 answers
Sort by: Most helpful
-
dn 11 Reputation points
2021-12-03T12:49:01.927+00:00 -
Vilius Šumskas 6 Reputation points
2021-12-22T23:36:55.657+00:00 We experience exactly the same behaviour. I've spent one full day and I think this is a bug in how Microsoft fixed PrintNightmare vulnerability and printer deployment via Deployed Printer Connection GPO.
I'm dumping all test information here in case someone needs it. The tests where performed on Windows Server 2019 print server and Windows 10 clients with latest 2021-12 CU installed, though I don't think OS version matters that much.
First thing you need to understand is that the behaviour and how GPO settings described in this MS article https://support.microsoft.com/en-us/topic/kb5005652-manage-new-point-and-print-default-driver-installation-behavior-cve-2021-34481-873642bf-2634-49c5-a23b-6d8e9a302872 work depends on the type of the driver.
If you are using only V4 drivers there are three possible solutions (choose only one of them):
Solution 1
a) Set Computer Configuration -> Policies -> Administrative Templates -> Printers -> Only use Package Point and Print to Enabled.
b) Set Computer Configuration -> Policies -> Administrative Templates -> Printers -> Package Point and Print - Approved Servers to Enabled and specify FQDN of your print server.
c) Set Computer Configuration -> Policies -> Administrative Templates -> Printers -> Limit print driver installation to Administrators to Disabled.This will allow to deploy printers via Deployed Printer Connection GPO targeting User Scope. I didn't find any information if this also enables PrintNightmare vulnerability. Here https://support.microsoft.com/en-us/topic/kb5005010-restricting-installation-of-new-printer-drivers-after-applying-the-july-6-2021-updates-31b91c02-05bc-4ada-a7ea-183b129578a7 Microsoft says that CVE-2021-34527 is only present if Point and Print Restrictions GPO is used and nothing about Package Point and Print. Even if it is, the vulnerability should be limited only to the attack vector coming from the FQDN specified earlier. Also, vulnerability should only be exploitable when attacker uses V3 packaged drivers, and not package-unaware drivers.
Solution 2
Use GPP instead of Deployed Printer Connection GPO to deploy printers. This will allow to deploy V4 printers without any other GPO/registry changes.
Solution 3
Change your Deployed Printer Connection GPO to use Computer Configuration instead of User Configuration and apply it to Computers OU instead of Users OU. This again will allow you to deploy V4 printers without any other GPO/registry changes.
If you are using V3 packaged drivers there is only one solution:
Solution 1
a) Set Computer Configuration -> Policies -> Administrative Templates -> Printers -> Only use Package Point and Print to Enabled.
b) Set Computer Configuration -> Policies -> Administrative Templates -> Printers -> Package Point and Print - Approved Servers to Enabled and specify FQDN of your print server.
c) Set Computer Configuration -> Policies -> Administrative Templates -> Printers -> Limit print driver installation to Administrators to Disabled.This will allow to deploy printers via Deployed Printer Connection GPO targeting User Scope. Again, it is unclear if this enables PrintNightmare vulnerability, but even if it's so, the vulnerability should be limited only to the attack vector coming from the FQDN specified earlier. Also, vulnerability should only be exploitable when attacker uses V3 packaged drivers, and not package-unaware drivers.
If you are using very old V3 package-unaware drivers the solution is a little bit different:
Solution 1
a) Set Computer Configuration -> Policies -> Administrative Templates -> Printers -> Package Point and Print - Approved Servers to Enabled and specify FQDN of your print server.
b) Set Computer Configuration -> Policies -> Administrative Templates -> Printers -> Point and Print Restrictions to Enabled, enable User can only point and print from these servers and specify FQDN of your print server. Also, don't forget set Security Prompts to your liking.
c) Set Computer Configuration -> Policies -> Administrative Templates -> Printers -> Limit print driver installation to Administrators to Disabled.This will allow to deploy printers via Deployed Printer Connection GPO targeting User Scope, but if you choose to disable Security Prompts in step b) it also enables PrintNightmare vulnerability. Vulnerability can be exploited when using both V3 packaged and package-unaware drivers. It is limited to the attack vector coming from the FQDN specified earlier though. If Security Prompts are enabled vulnerability cannot be exploited.
Since I'm using only V4 drivers and I think it's a bug, I went with first Solution 1 and will wait until MS hopefully comes up with another fix.
Hope this helps.
P.S. I encourage everyone to have Feedback Hub ticket filled regarding this issue. Maybe our voices will be heard at some point.
-
Gary Longstaff 6 Reputation points
2022-04-14T11:32:32.227+00:00 Okay so Microsoft as usual 'passed the buck' to others. We have all had to look at creating a Reg policy for Point and Print
HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows NT\Printers\PointAndPrint
value name="RestrictDriverInstallationToAdministrators"
type=REG_DWORD
value=0After the most recent updates MS forced the restriction and this still impacts older printer drivers even after the reg hack. After plenty of head scratching and investigations: 1.You must have Type 3 drivers 2. If you have older packages NOT classed as packaged it appears MS still doesn't allow them without issues: using kix script-even if you have disabled the Point and Print registry, the user is still prompted with the 'Trust this printer and install option', to which you need to supply and admin account . Once installed all fine the next time around. IF using GPO Targeting the printer configured in GPO doesn't appear in the printer options list when trying to print. Found the following in the event log of the client machine [even though the driver does exist on the server]
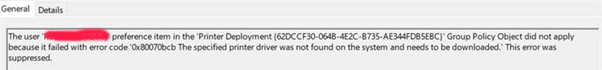
1The column where the Package column have 'false' against them will likely be issues:
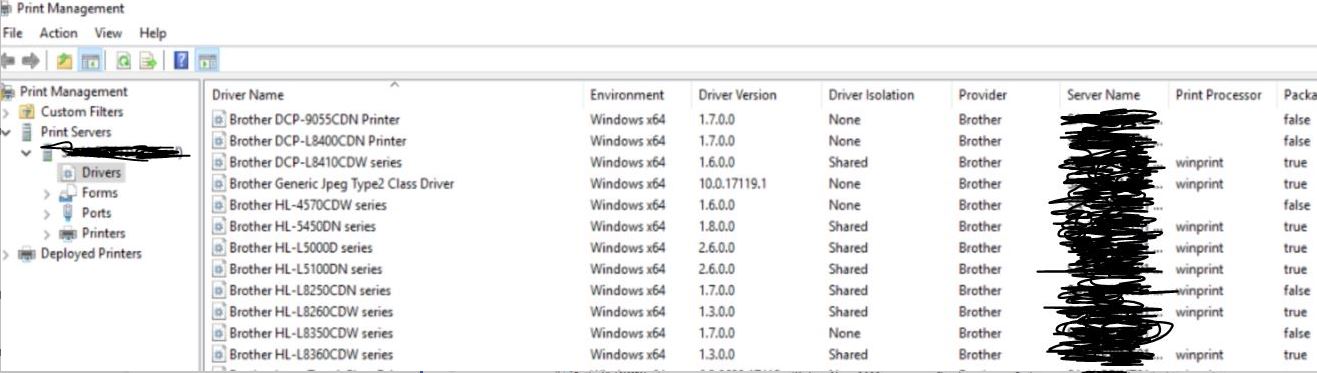
I had been scratching my head for days testing and wondering why the Brother HL-5450DN worked but not the Brother HL-L8250CDN as there just didn't appear to be a reason for it, well there is thanks to MS. :( So, to sum up: 1. You will require new drivers from the manufacturer’s website. 2. look at ways to possibly build a 'package' to be deployed by systems like SCCM.Just another shambles!
-
DanHoffa 46 Reputation points
2022-10-20T11:44:00.943+00:00 It has now be over a year since I first posted this issue. In that time I have probably tried a dozen different fixes.
The BEST FIX I Have Found is TYPE 4 drivers.
Since Microsoft basically broke printer deployment via GPO most printer manufacturers have finally been forced to release Type 4 printer drivers. Since I have converted all my print servers to using Type 4 drivers I have had almost zero issues with printers deploying via GPO. The issues I have had are on the workstation end and will always happen on occasion.
Hope this helps.
-
 Limitless Technology 39,351 Reputation points
Limitless Technology 39,351 Reputation points2021-09-28T15:00:27.29+00:00 Hello @DanHoffa ,
Thank you for your question.
Based on the description of your problem, I recommend that you take a look at the topic below, which has a problem similar to yours and may help you fix the problem:
------------------------------------------------------------------------------------------------------------------------
If the answer is helpful, please vote positively and accept as an answer.


