I got this working. In my VMSS template, I'd set the upgradePolicy to manual. It needs to be Automatic.
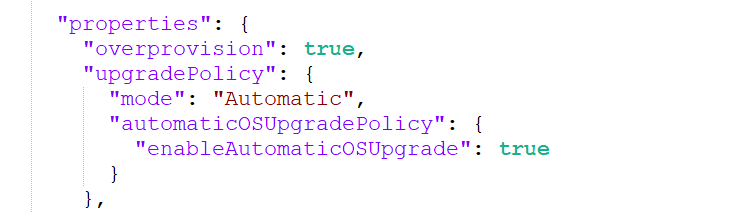
If you're a newbie like me, you'd also want a healthProbe or an healthExtension specified in your properties.vmProfile.networkProfile.
This browser is no longer supported.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support.
I have a VMSS that is deployed using ARM. This VMSS has a systemAssigned identity.
In the same ARM template, the keyvault's accesspolicy is updated to allow the VMSS identity to GET,LIST secrets and certificates.
Then, the VMSS extensions are updated via "Microsoft.Compute/virtualMachineScaleSets/extensions" resource using the same ARM template to pullthe certificate from the keyvault into the VMSS.
"secretsManagementSettings": {
"pollingIntervalInS": "300",
"requireInitialSync": true,
"certificateStoreName": "MY",
"certificateStoreLocation": "LocalMachine",
"observedCertificates": "[parameters('keyVaultObservedCertificates')]"
}
This extension seems to be loaded correctly in the Portal UI. But, upon logging in to the individual VMs in the VMSS, I do not see this certificate in any store.
I got this working. In my VMSS template, I'd set the upgradePolicy to manual. It needs to be Automatic.

If you're a newbie like me, you'd also want a healthProbe or an healthExtension specified in your properties.vmProfile.networkProfile.


@Kimaya Kamat Thank you for your question!!!
Assuming that you might be following this to achieve the above and as you mentioned you have provided the required access and parameters as mentioned in document and assuming that for the parameter observed certificate you might have provided URI for certificate uri as mentioned here as well
When this VM is deployed, Azure will inject the certificate into the VM. On Windows, certificates in PFX file are added with the private key not exportable. The certificate is added to the LocalMachine certificate location, with the certificate store that the user provided. More info here. As mentioned here:
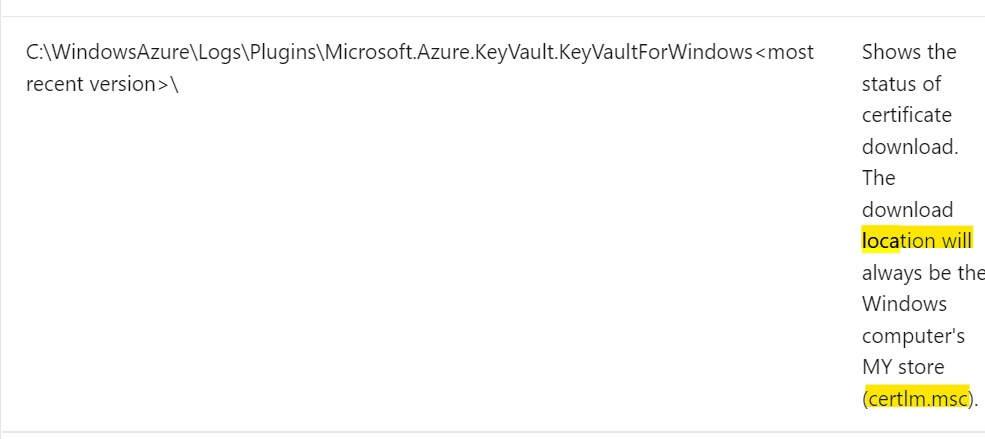
Similarly on Linux, the certificate file is placed under the /var/lib/waagent directory, with the file name <UppercaseThumbprint>.crt for the X509 certificate file and <UppercaseThumbpring>.prv for private key. Both of these files are .pem formatted.
Can you check the above and see if you can find certificate as mentioned or not. If possible cross check documentation once to check if there is any parameter value missing.
If issues till persist let me know will work with you further on this one.
Please "Accept as Answer" if it helped so it can help others in community looking for help on similar topics.