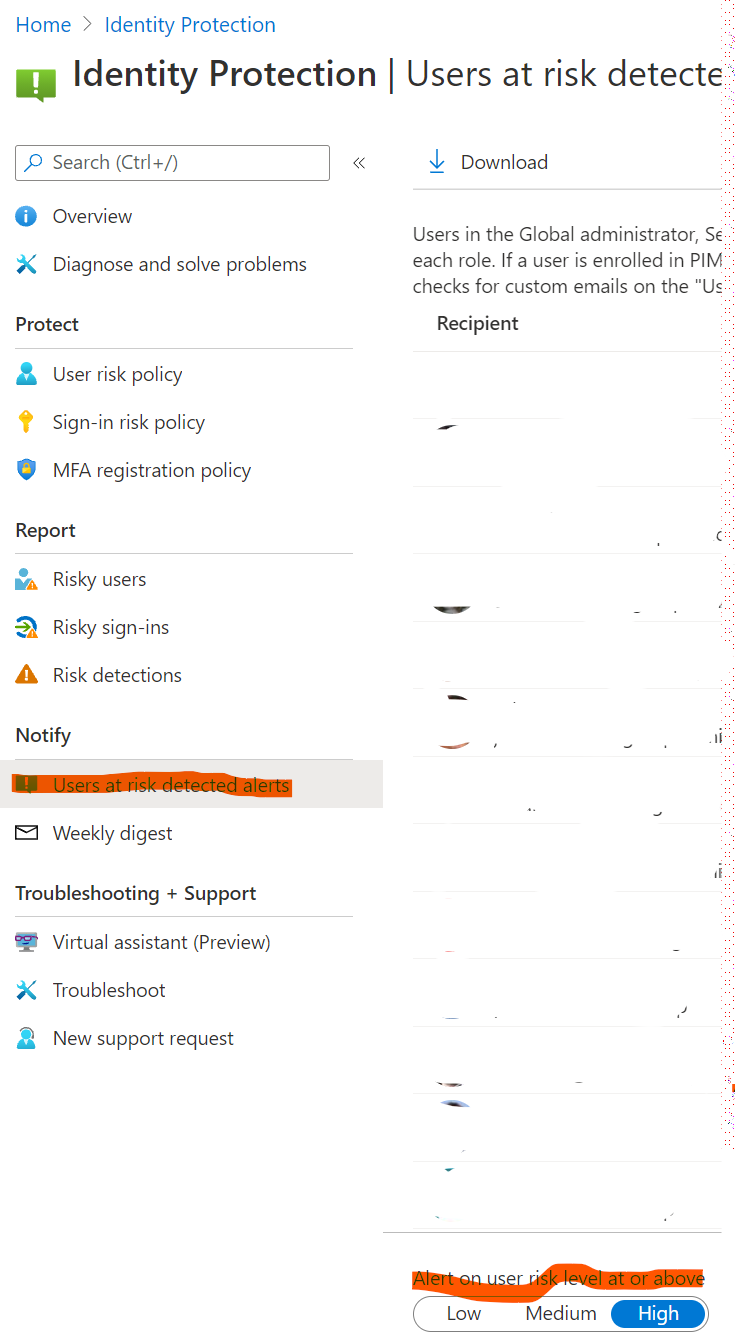
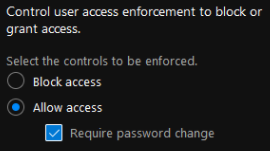
In that case, I would implement the policies to protect your tenant and users:
https://learn.microsoft.com/en-us/azure/active-directory/identity-protection/concept-identity-protection-policies
You can investigate:
https://learn.microsoft.com/en-us/azure/active-directory/identity-protection/howto-identity-protection-investigate-risk
or output:
https://learn.microsoft.com/en-us/azure/active-directory/identity-protection/howto-export-risk-data