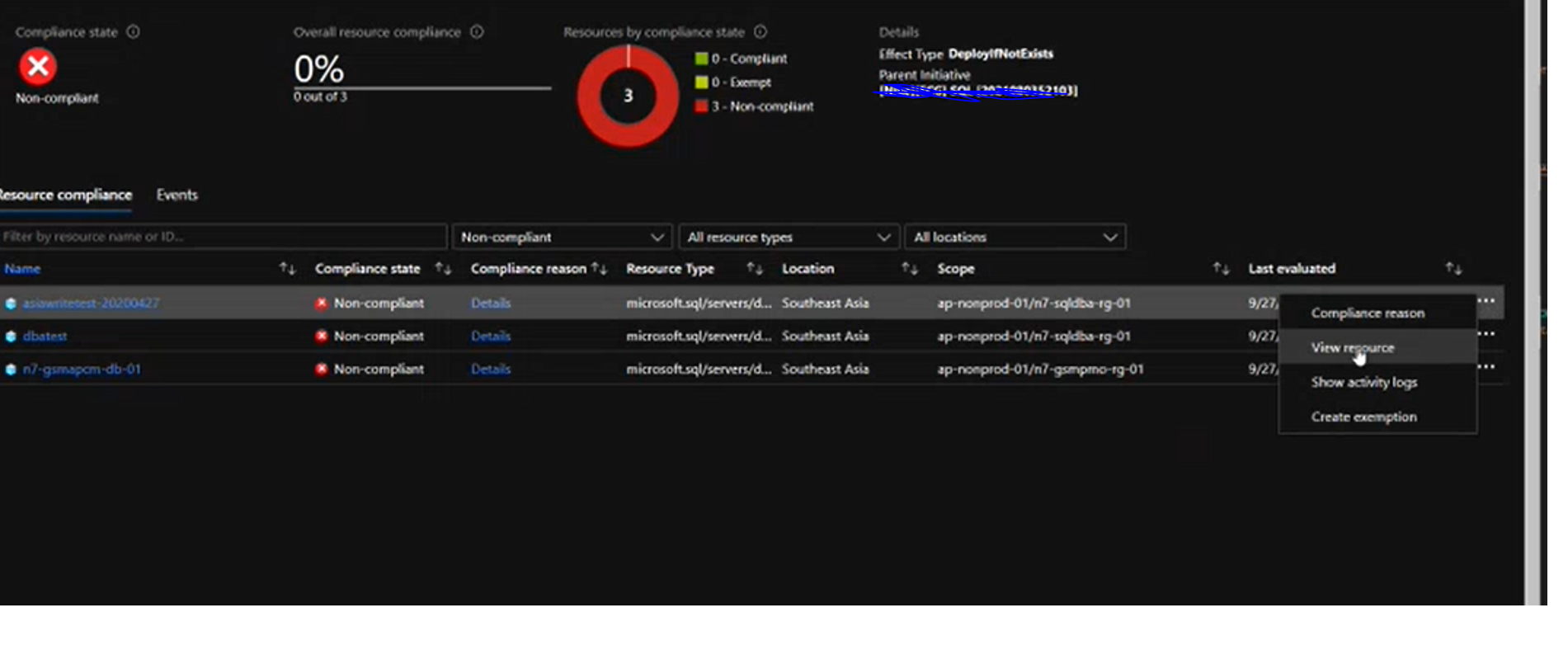
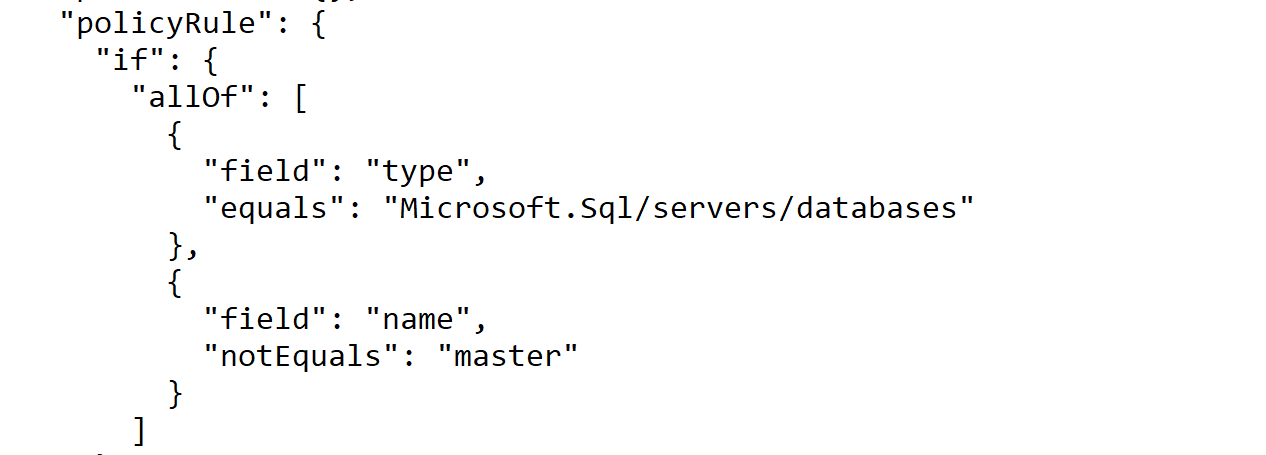
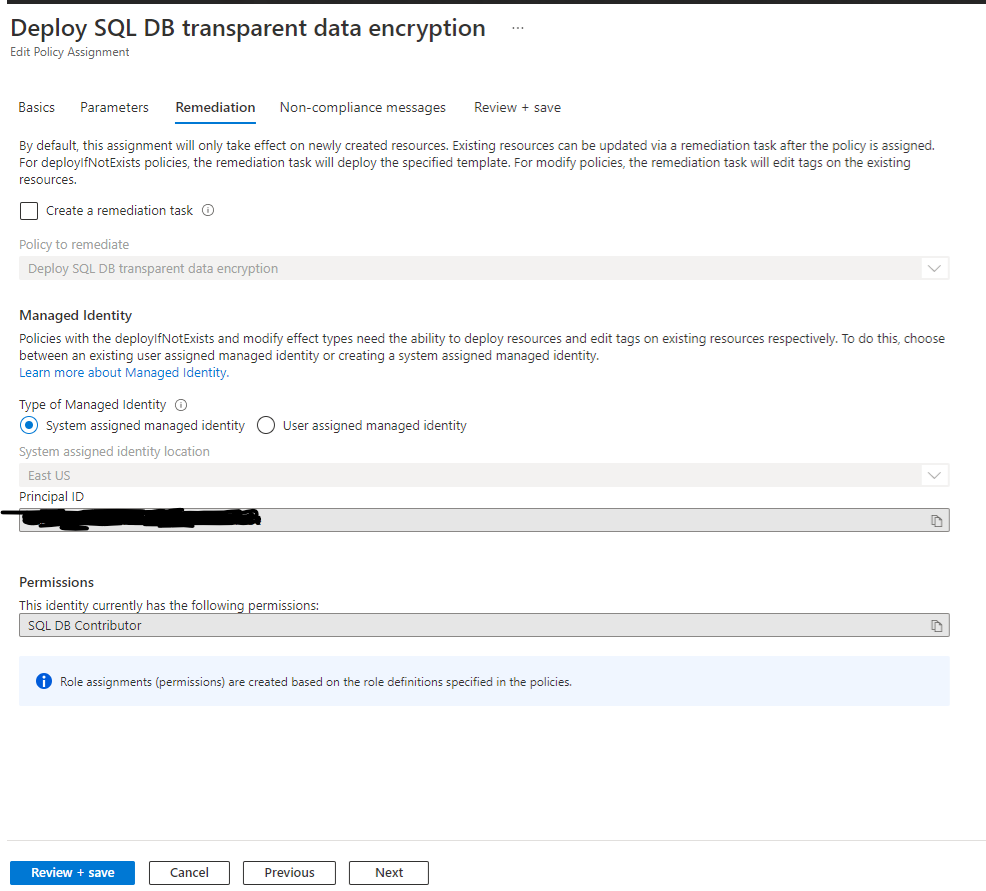
Our team was able to repo this issue and this is happening by design. For this kind of policy with DeployIfNotExists policy effect, by default, this policy assignment only takes effect on newly created databases. Existing databases can be updated via a remediation task after the policy is assigned - this can be done in the Compliance blade.
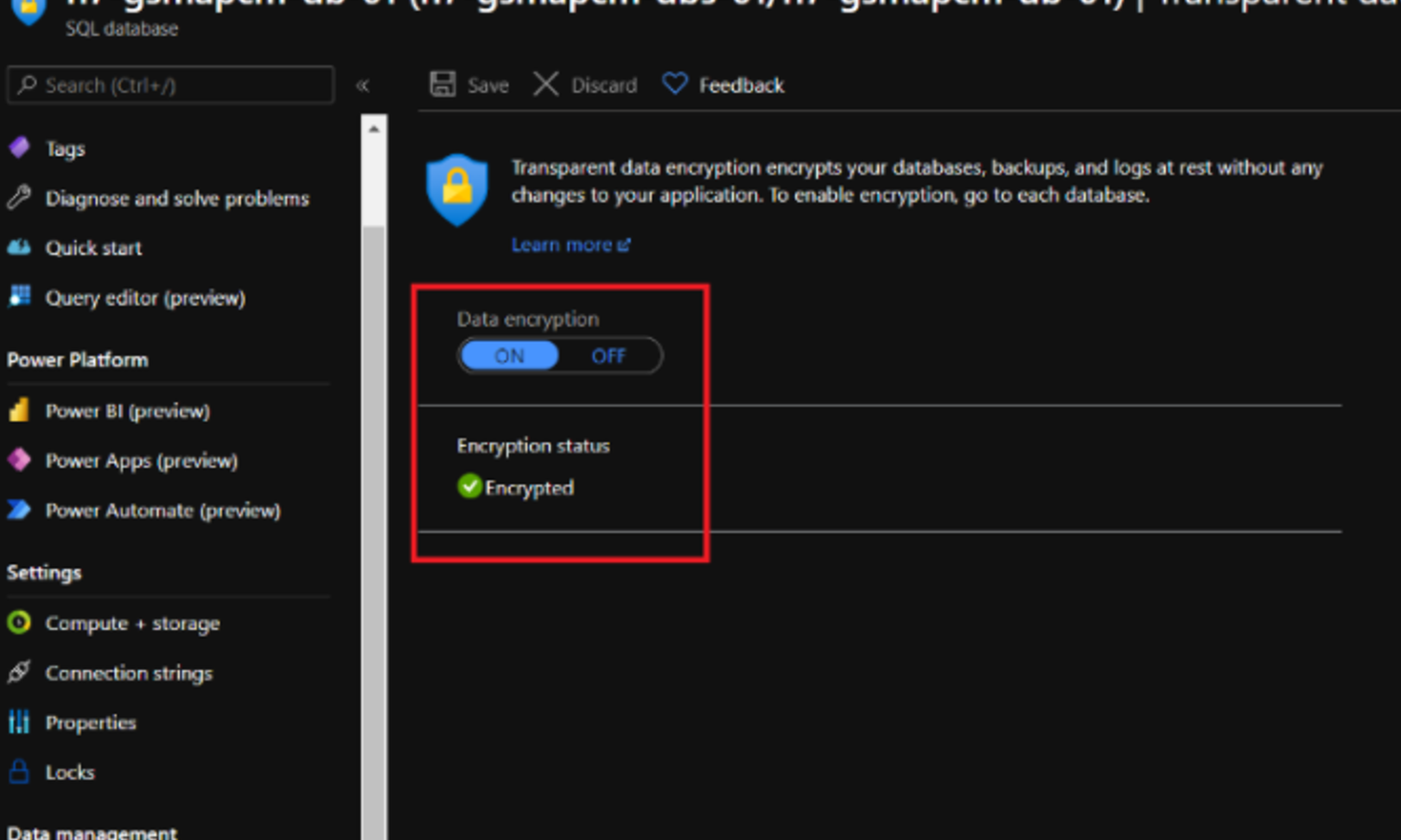
Seeing certain databases as non-compliant even though TDE is enabled due to the fact that these were existing databases when this policy was assigned, so the policy doesn't enable TDE on existing databases and just shows them as non-compliant.
We will check with Azure Policy team - if once TDE is enabled on the databases that were originally marked as non-compliant, why doesn't the Compliance tab refresh with time and remove these databases from non-compliant state
We are assuming this likely is also default behavior for policies using the DeployIfNotExists policy effect
Regards,
Oury