Scan for Containers and dormant VMs On Windows 10 ?
"Hello how can I enable a scan for invasive containers and or dormant VMs on a Windows 10 machine?"
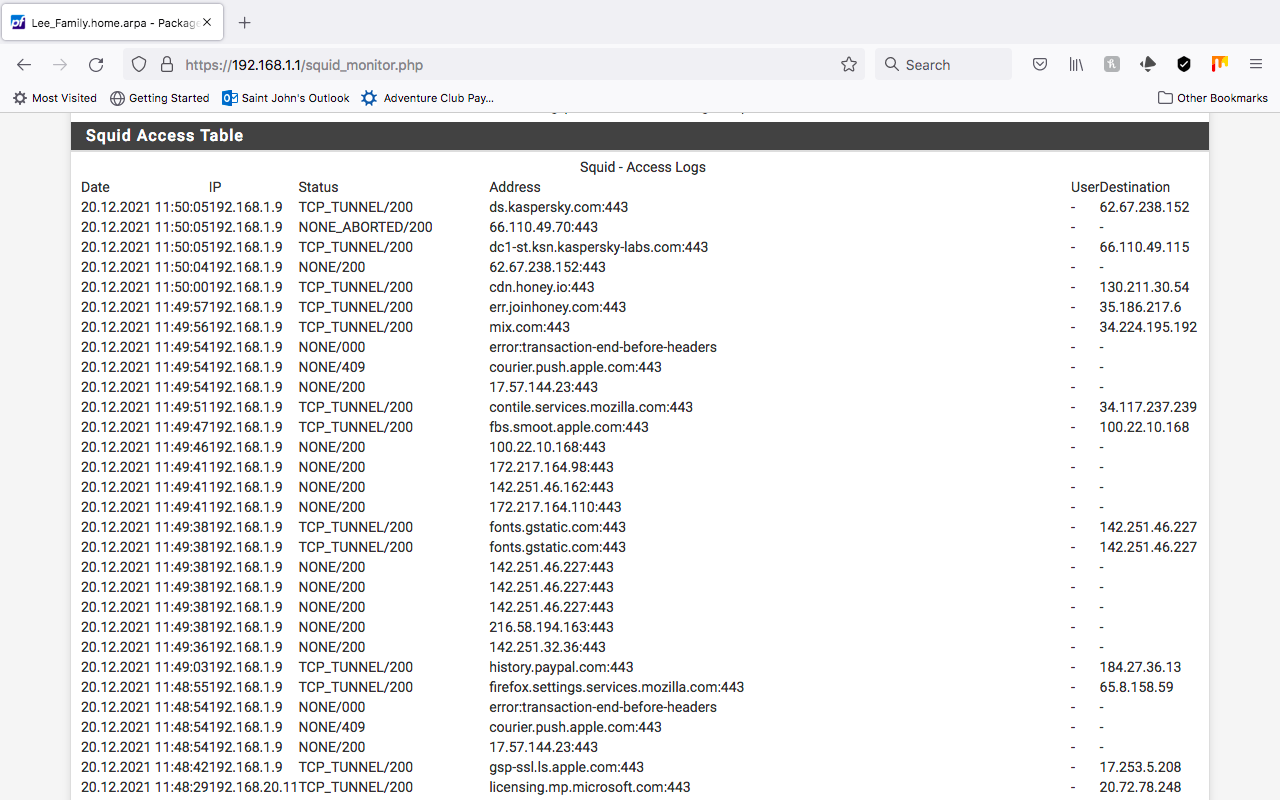
If we use a proxy "content accelerator" we can figuratively catch the container and take it "the proxy caught container" off line with transparent mode and dual use container duplication and air gap tha container to test for container purity with a virus scan after or use a DLP systems while its running in transparent mode. Now how can we scan that Machine we caught it on for instances of that invasive container on non small office, company, and corporate non approved containers. I want to learn how to block out any reverse binds or egress use that are bypassing the acls with outgoing connections that are data marshaling the NIC. Keep in mind anything that will alert the container manager will trigger a sandboxed event of that container. We want hard evidence for cybersecurity GDPR, and California Privacy laws being broken with invasive use.
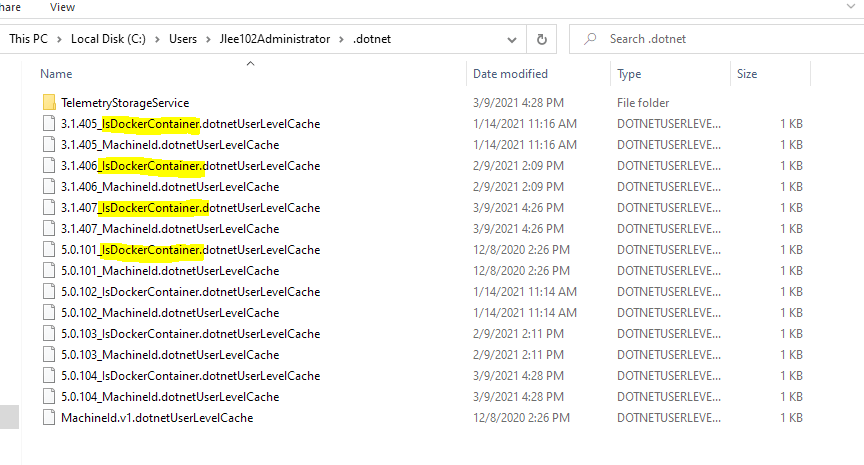
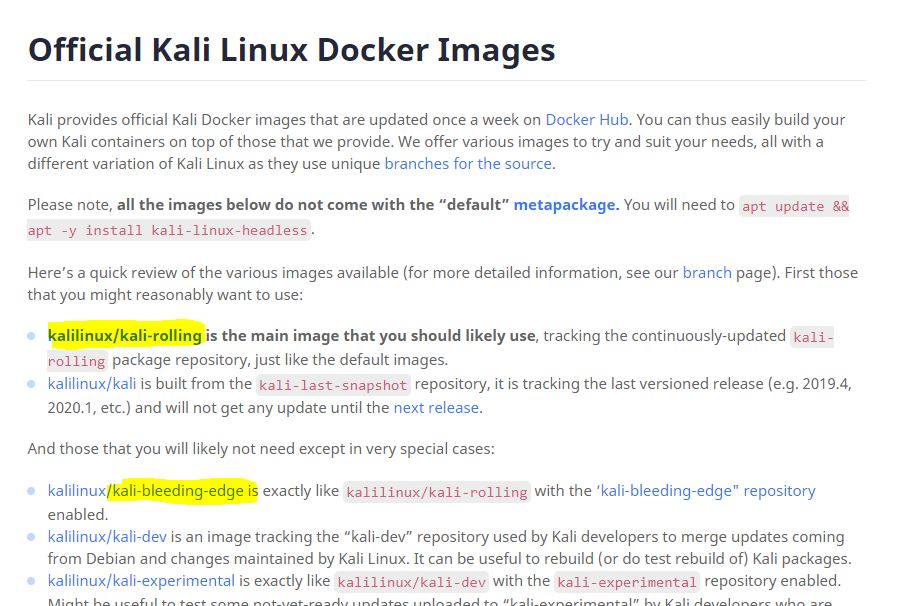
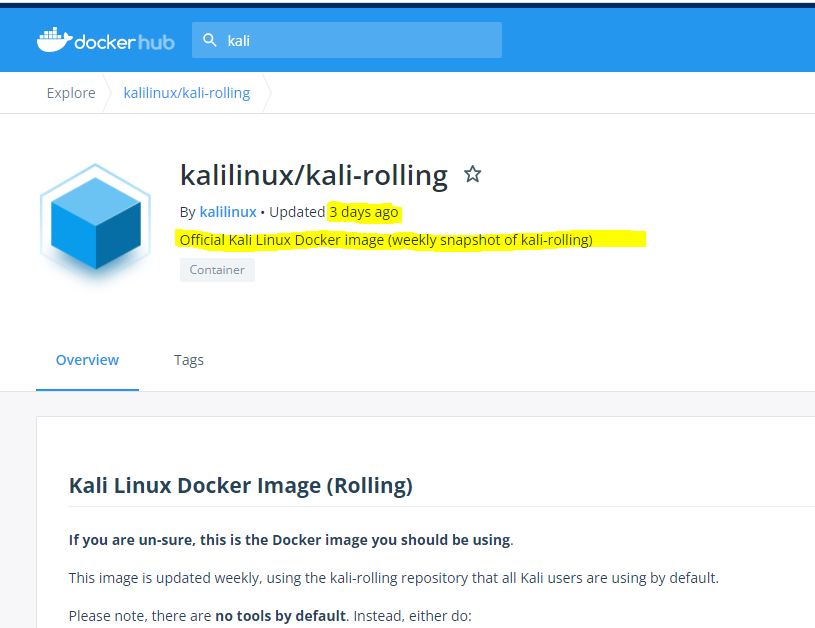
What Windows security tool can we use to scan for any and all Docker containers without installing Docker, or other container managers? Or what firewall rules can you put in place for new virtual sandbox container based issues.
Keep in mind any and all fresh installs will come from the Windows servers and push that same invasive non approved container down. It is no longer a DVD or CD one size fits all image that is downloaded. They are Ip and use based for systems with use of auto deployment and vendor drivers that are pushed on reimage. So if you wipe the system that same container is fault tolerant based on the system you are using and will eventually restore itself. How can we scan for them?
Example: Hypothetically can a old job you left that has a disgruntled manager still access and still push containers to a private home system that you used for access with Office 365 only or had linked to a personal Gmail account. Even after you left that job this manager wanted to do something invasive because he did not like that you put your three weeks in, and tries to break your personal system.
This is all hypothetical however you can see the reasons for a need to scan for any and all instances of containers in a small office setting to a large corporate environment. NIST SP800-190 states a major container issue and I quote
"1. Compromise of an image or container. This risk was evaluated using the data-centric 696 system threat modeling approach described in NIST SP 800-154 [17]. The primary “data” 697 to protect is the images and containers, which may hold application files, data files, etc. 698 The secondary data to protect is container data within shared host resources such as 699 memory, storage, and network interfaces.
- Misuse of a container to attack other containers, the host OS, other hosts, etc."
With that being said what protections and compartmentalization is there for the end user in a personal setting and or small business that would utilize proxy duplication for virus scan and testing of what is being data marshaled within the shielded containers, as well as protections for the good known instances containers that are currently used for Cybersecurity.
When we have our phones linked with software like Microsoft's phone companion issues such as invasive unapproved illegal containers could cause issues, even blocking cell phone based messages. This is smartphone system with messages to my father last couple days. Everything says message expired or not available. Could a invasive container even take control of the "Your Phone application?"
Ref:
Final Publication: https://doi.org/10.6028/NIST.SP.800-190 (direct link: http://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-190.pdf).