Dear @ChaitanyaNaykodi-MSFT , thanks for your reply.
First question:
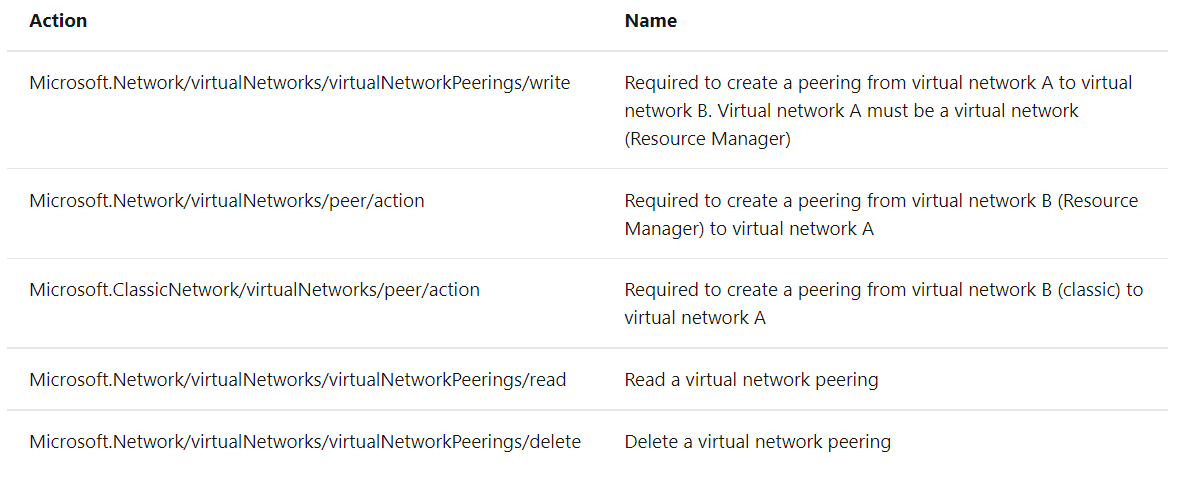
Unless I'm mistaken, my role as a "Contributor" (the default one, not customized) includes the roles that you have requested (Network contributor and Classis Network Contributor), no?
Moreover, it doesn't seem to complain about my vnet in my resourcegroup, but instead about a required "peer/action" on Databricks' resource group.
It seems impossible though to make me contributor on the Databricks resources (which might be normal since it is a SaaS).
When we tried to assign me "Contributor" rights on the Databricks instance, we got a "Sytem Deny" error.
Failed to add Role assignment
Failed to add Johan Van Noten as Contributor for databricks-rg-adb... : The client 'ourAdmin@...' with object id '7138d...' has permission
to perform action 'Microsoft.Authorization/roleAssignments/write'
on scope '/subscriptions/da52c3f.../resourceGroups/databricks-rg-adb.../providers/Microsoft.Authorization/roleAssignments/27c4f3...';
however, the access is denied because of the deny assignment with name 'System deny assignment
created by Azure Databricks /subscriptions/da52c3../resourceGroups/rgA/providers/Microsoft.Databricks/workspaces/adb...'
and Id 'e0a282ee...' at scope '/subscriptions/da52c3.../resourceGroups/databricks-rg-adb...
Should we try to assign me "lower" rights on the Databricks that are sufficient to perform the operation but are not refused by Databricks' configuration?
It feels strange to see this issue occurring, because I would expect everyone would then experience this issue when trying to peer Databricks, no?
Concerning the second question:
> Is this a fundamental issue? I had a similar message when trying to do it with the double pairing from the Azure portal.
I am not sure what you meant by double pairing but the issue will occur if you role does not have actions mentioned above.
I meant that the normal vnet peering functionality in the portal always wants to create two peerings:
- one from A to B
- one from B to A
In my case that is not desired, since the latter one is already established (from Databricks to my own vnet, following the prescribed solution).
The portal does not allow me to just create the one "missing" peering from my vnet to Databrick.
Johan