How are we supposed to use private endpoint with key vaults and follow all best practices?
The documentation(1) suggests that overriding DNS zones are created only for private endpoints:
It is not recommended to override a zone that's actively in use to resolve public endpoints.
E.g.
- storage: privatelink.blob.core.windows.net
- key vault: privatelink.vaultcore.azure.net
Azure side
After private endpoint and private DNS zone creation private endpoint connections are working on services deployed into related VNet:
- storage endpoint DNS request to xx.blob.core.windows.net has CNAME for xx.privatelink.blob.core.windows.net and finally resolves to PE IP
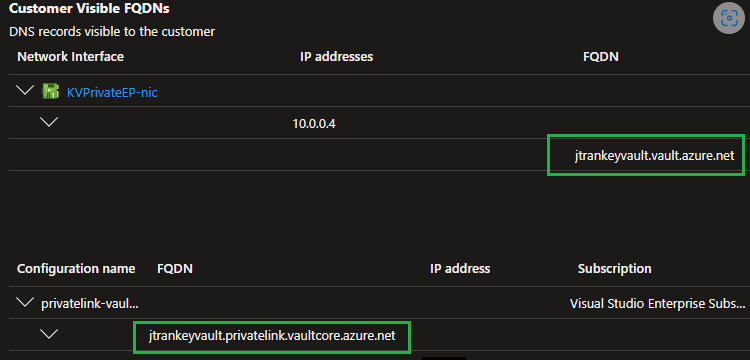
- keyvault endpoint DNS request to xx.vault.azure.net has CNAME for xx.privatelink.vaultcore.azure.net and finally resolves to PE IP
VPN clients with hosts
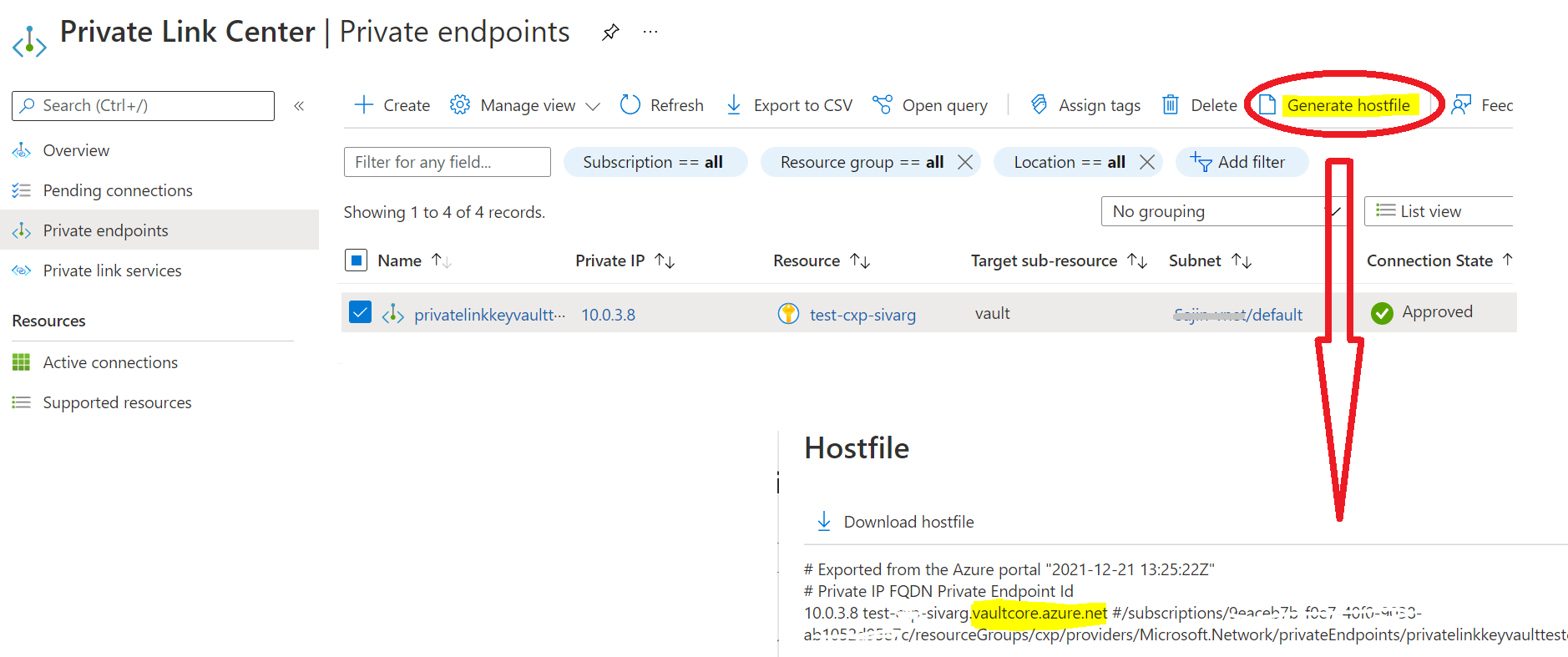
hosts file generation feature(2) on portal generates following entries
- 10.0.0.6 xx.vaultcore.azure.net # notice word
core here
- 10.0.0.5 xx.blob.core.windows.net
Portal and other tools are still e.g. querying secrets from keyvault using address https://x.vault.azure.net/secrets?api-version=7.0 and that is not available on generated hosts file and therefore all requests will fail because IP is resolved by public DNS.
Related template as example
https://github.com/Azure/azure-quickstart-templates/tree/master/quickstarts/microsoft.keyvault/key-vault-private-endpoint
This template can be used to reproduce private endpoint configuration that generated non-working hosts file
The question number 1
How can I create automatically hosts file with correct entries?
I already tried following:
- Using customDnsConfigs property on Microsoft.Network/privateEndpoints
- Using private DNS zone for
vault.azure.net + PE with Microsoft.Network/privateEndpoints/privateDnsZoneGroups without linking it with VNet.
Those did not work.
The question number 2
ARM/Bicep deployment has following property while running deployment environment().suffixes keyvaultDns(3).
- Is it supposed to be suffix for public DNS?
- Should there be environment-specific suffix for privatelink DNS?
Linked template has some solution for this but using extra code is not optimal and it is still hardcoding values that should come from the deployment engine.
(1) https://learn.microsoft.com/en-us/azure/private-link/private-endpoint-dns
(2) https://portal.azure.com/#blade/Microsoft_Azure_Network/PrivateLinkCenterBlade/privateendpoints
(3) https://learn.microsoft.com/en-us/azure/azure-resource-manager/bicep/bicep-functions-deployment