Summary: The role assignment records stay alive while the identity does no longer exist. Microsoft states that this isnt a problem here and you can leave them lingering. It however is a problem when deploying with templates, as that gives an error when the assignment is still there.
Easily reproducable scenario:
In portal
- Create Resource Group
- Create 2 Managed Identities
- Give both contributor role over subscription
- Delete 1 of the identity
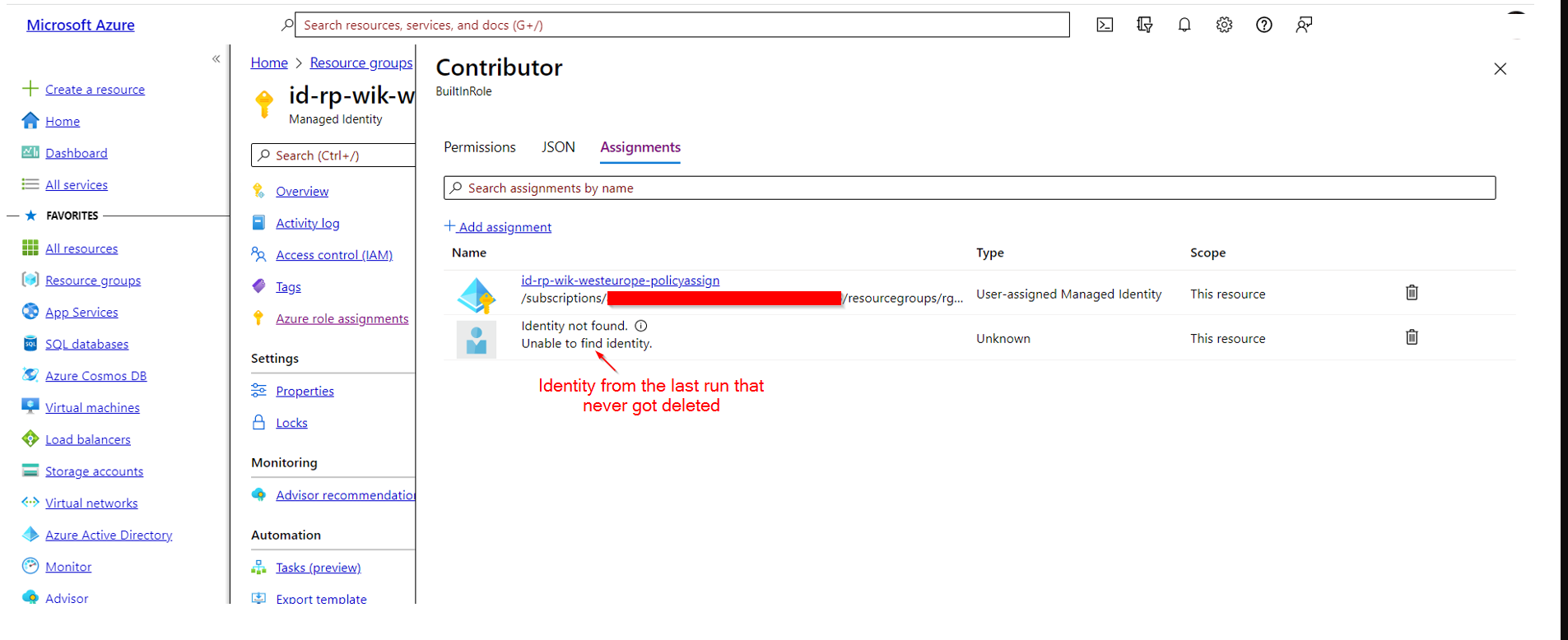
- Inspect Contributor assignments using the remaining identity and see an assignment to a no longer existing identity
Done by: RG=>Identity=>Azure role assignments=>click on the "Contributor" Role that is present=> on the detail view select "Assignments" to view all the assignments of the contributor role=> See an "Identity not found" assignment
Background Story:
I Have a Bicep template that deploys
- A Resource group
- A managed identity
- A role assignment to contributor on subscription level to that identity
When deploying the first time, all is well.
When deleting the resource group (with the identity in it) and deploying that same template again, an error occurs.
"Tenant ID, application ID, principal ID, and scope are not allowed to be updated"
This happens during role assignment. I tried 4 more times using the Bicep template.
When I tried using the portal to assign the role, all went well.
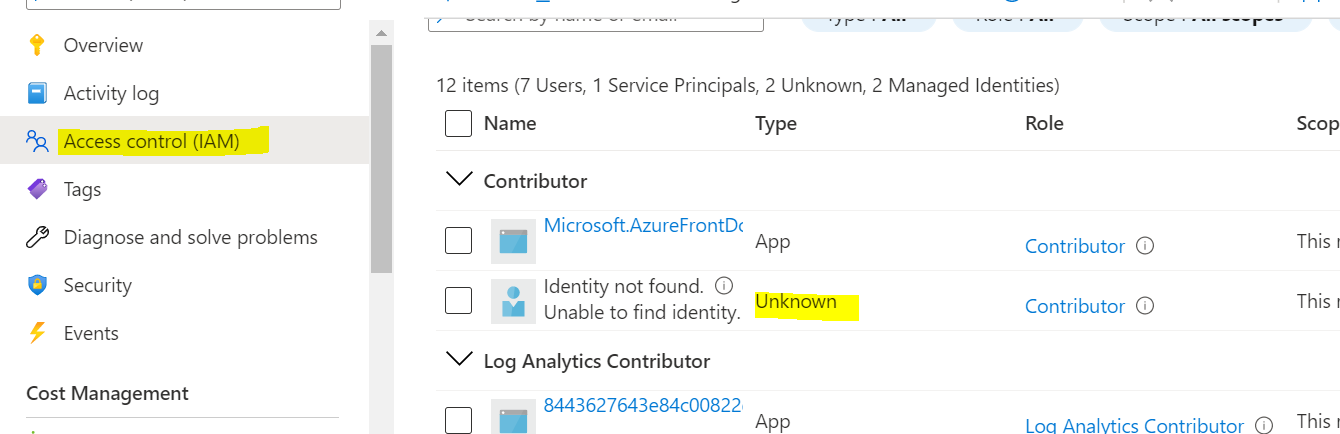
Digging a bit deep further, I found that the role assignment records are not deleted even though the identity is deleted, and those caused the error.
They point to a no longer existing identity. When deleting those records, deploying went well again.
See screenshot for no longer existing identity (at one point I had 4 records pointing to no longer existing identities).