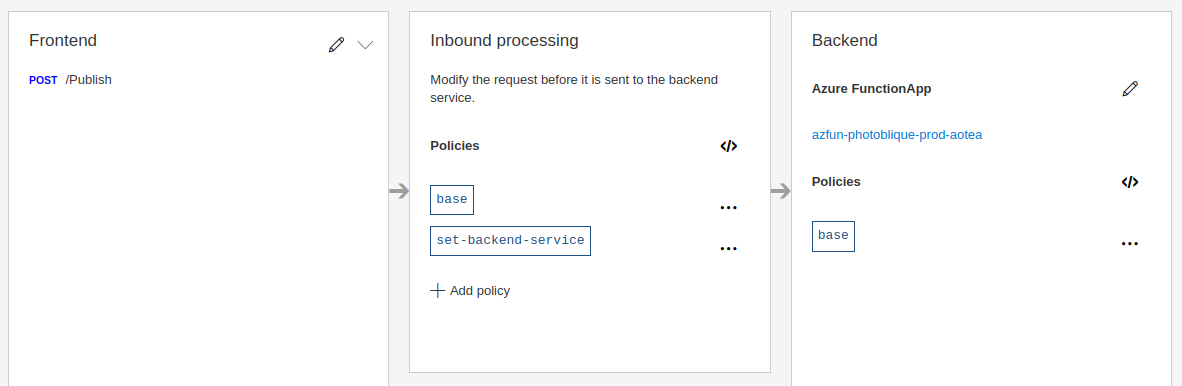
When you import a function into API management (APIM) you are, in effect, moving the point of authentication for the down-stream consumer (in this case your Powershell) to APIM. APIM acts as a facade (or proxy) for the functions behind it. And can apply authentication as well as many other policy-based elements to the traffic in additon to acting as a central 'switch-board' for all the back-end services behind it.
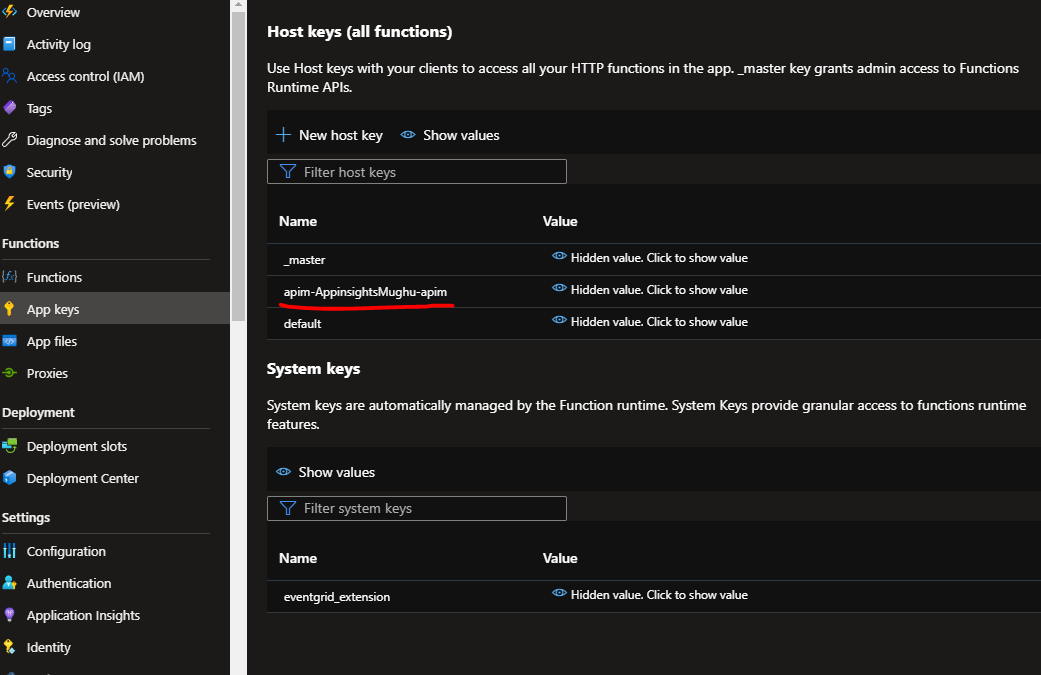
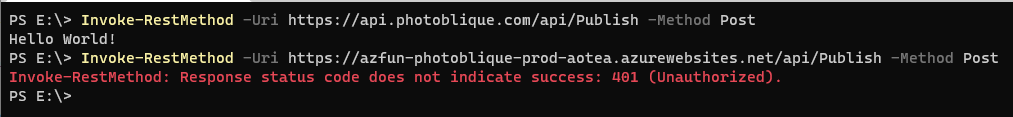
An import of a function app sets up a host-key in the function, a named value in APIM and appropriate policies which means that it is APIM that is authenticating with your function, not the calling user or service. The default config and policy for an imported policy may no 'end-user' authentication configured. Thus, if you can reach the APIM API endpoint then your call will pass through to the backend function without the need to provide any function key in the 'client'
Whilst you can configure an API to require a dedicated subscription key at the API level, APIM has the concept of Products and Subscriptions. A product is a collection of APIs, and a subscription provides access to one or more products (Thus a collection of APIs). If you want to use a 'pre-shared key' method of authentication, via APIM then review this. However, using API management you can enforce OAUTH2, mutual certificate authentication and pretty much anything else (including bespoke authentication providers) using advanced policies.
You could always change the API config and policy to just 'pass through' the function key, but then I would be interested in your use case for APIM (if you have one of course - you could just be learning :))
Hope that helps.