You do not need to send the employeeId attribute as a claim.
You can synchronize it with Azure AD Connect. Run the Azure AD Connect wizard, then pick Customize synchronization options. In Optional Features, check Azure AD app and attribute filtering. Then in the Azure AD Attributes, make sure you export the attribute you want to use in Azure AD.
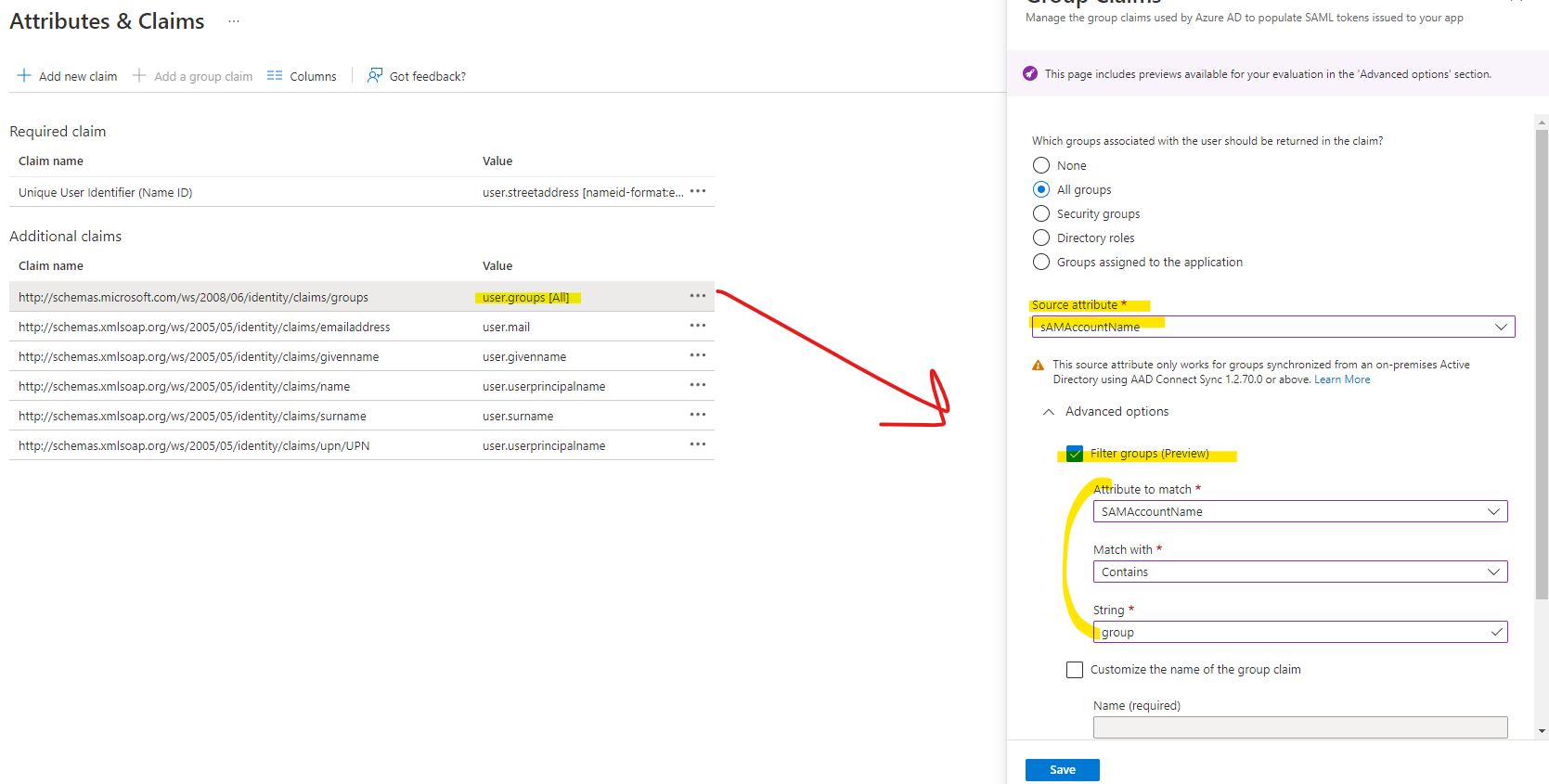
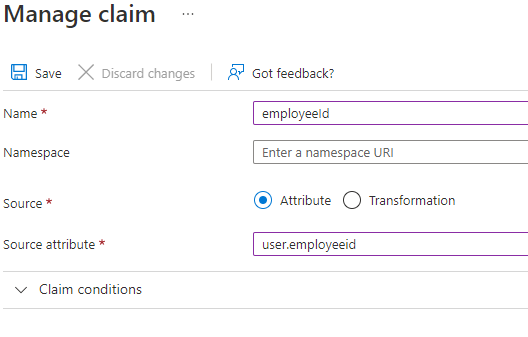
Then in the Azure AD portal, you can go the Enterprise App you want to send the employeeId to. Then select the Single sign-on blade and got to the Attributes and Claims section and click Edit:
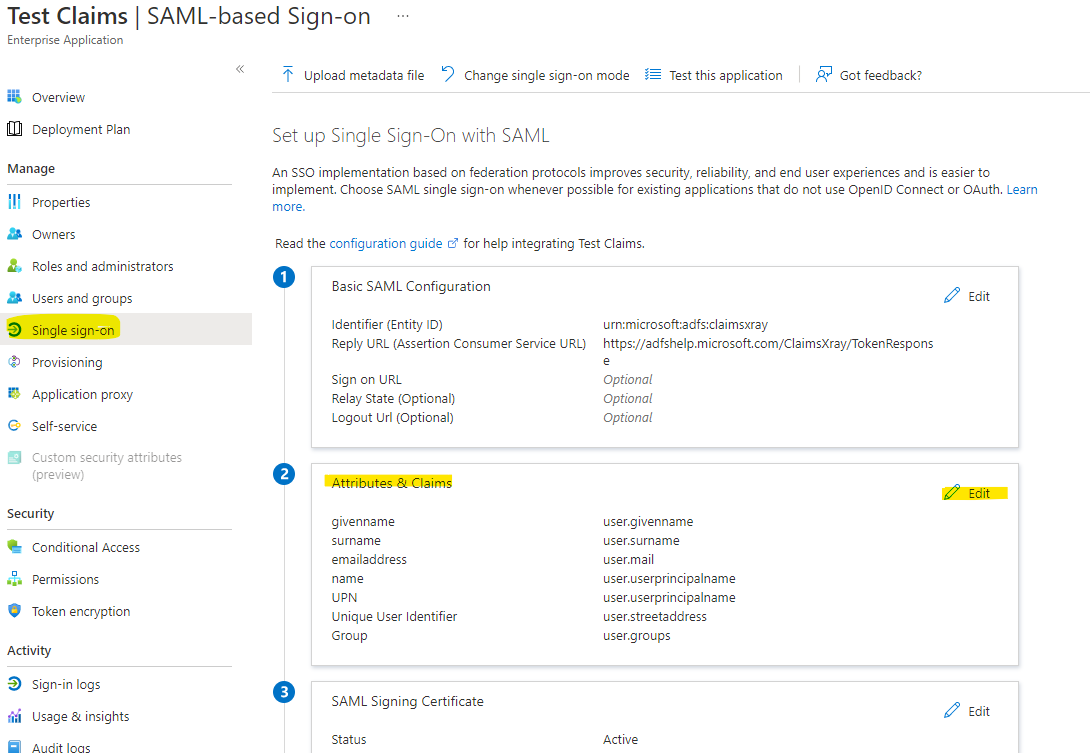
Then click Add new claims, and pick the following:
Does this help?