Hi @Aditi.Rachna ,
As AgaveJoe said, you could use the SecurityStamp Property and the SecurityStampValidatorOptions.ValidationInterval Property to make the logout user's cookie invalid.
In the Asp.net core Identity Logout.cshtml.cs page (if you can't find this page from the Identity Areas, see Scaffold Identity in ASP.NET Core projects), in the OnPost method, find the current user and update the Security Stamp:
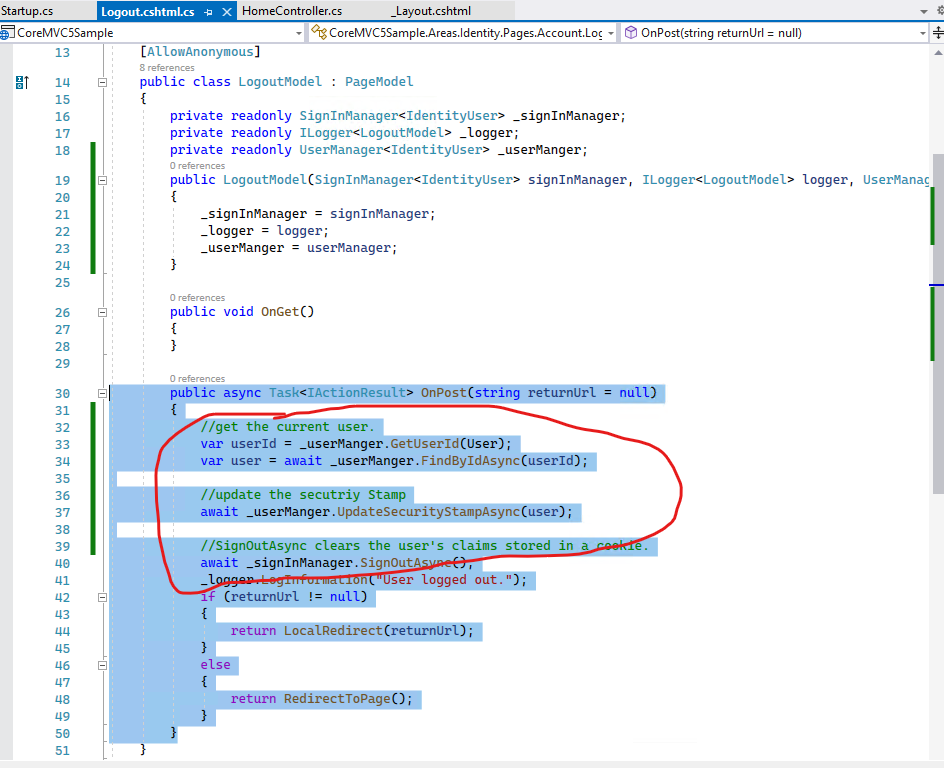
Then, in the Startup.cs file, add the following code in the ConfigureServices method:
services.Configure<SecurityStampValidatorOptions>(options =>
{
options.ValidationInterval = TimeSpan.FromSeconds(10);
});
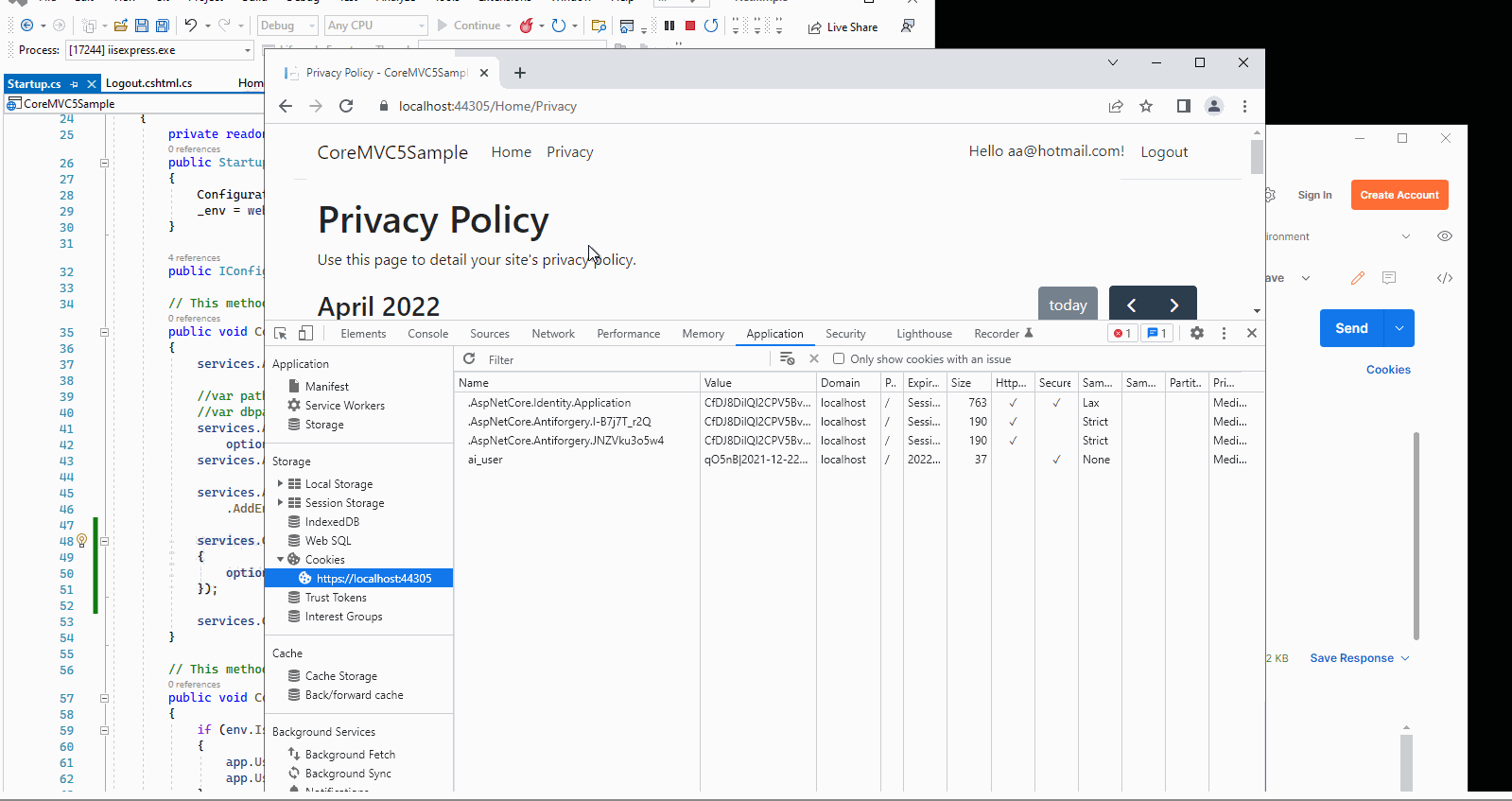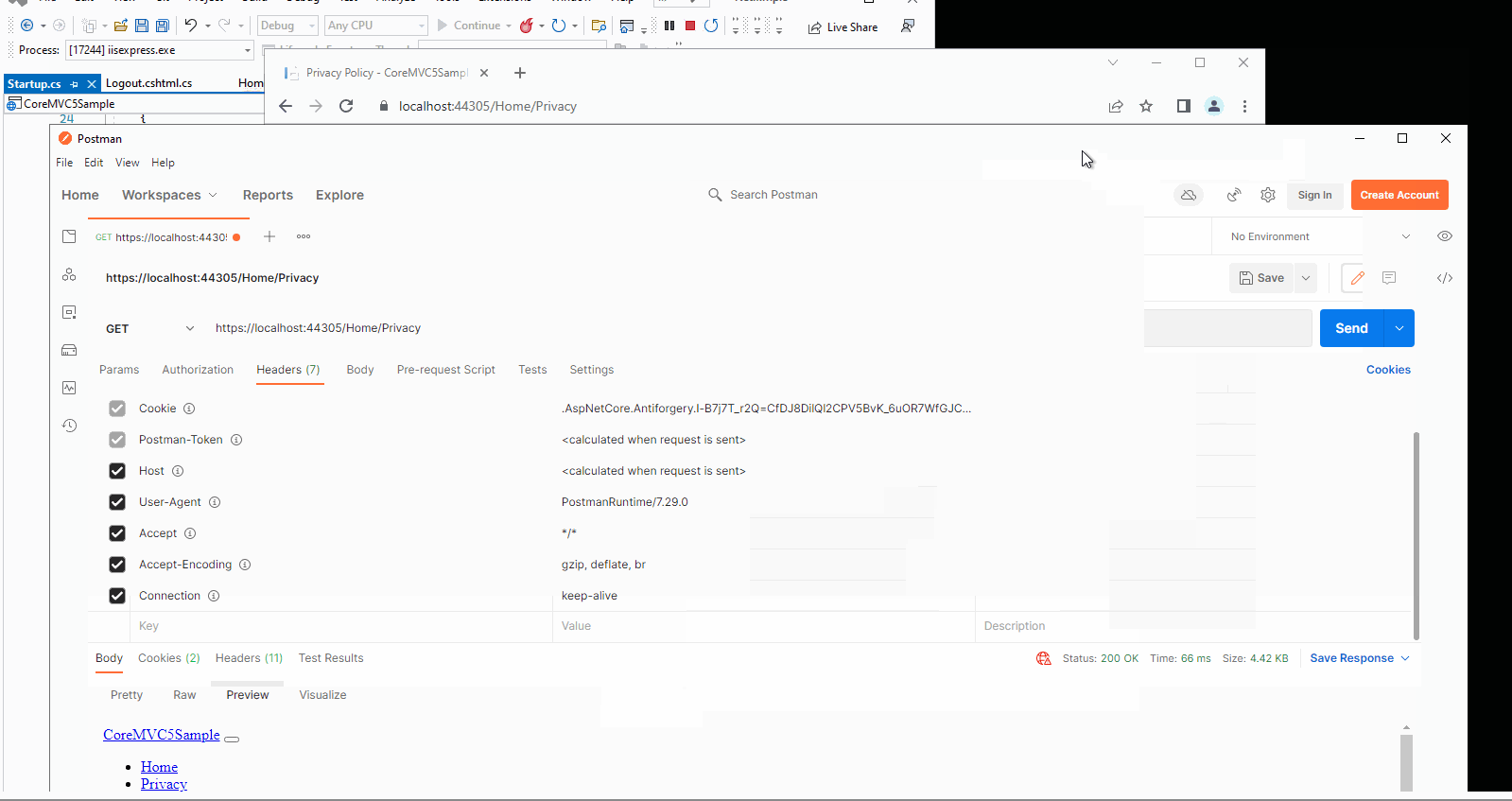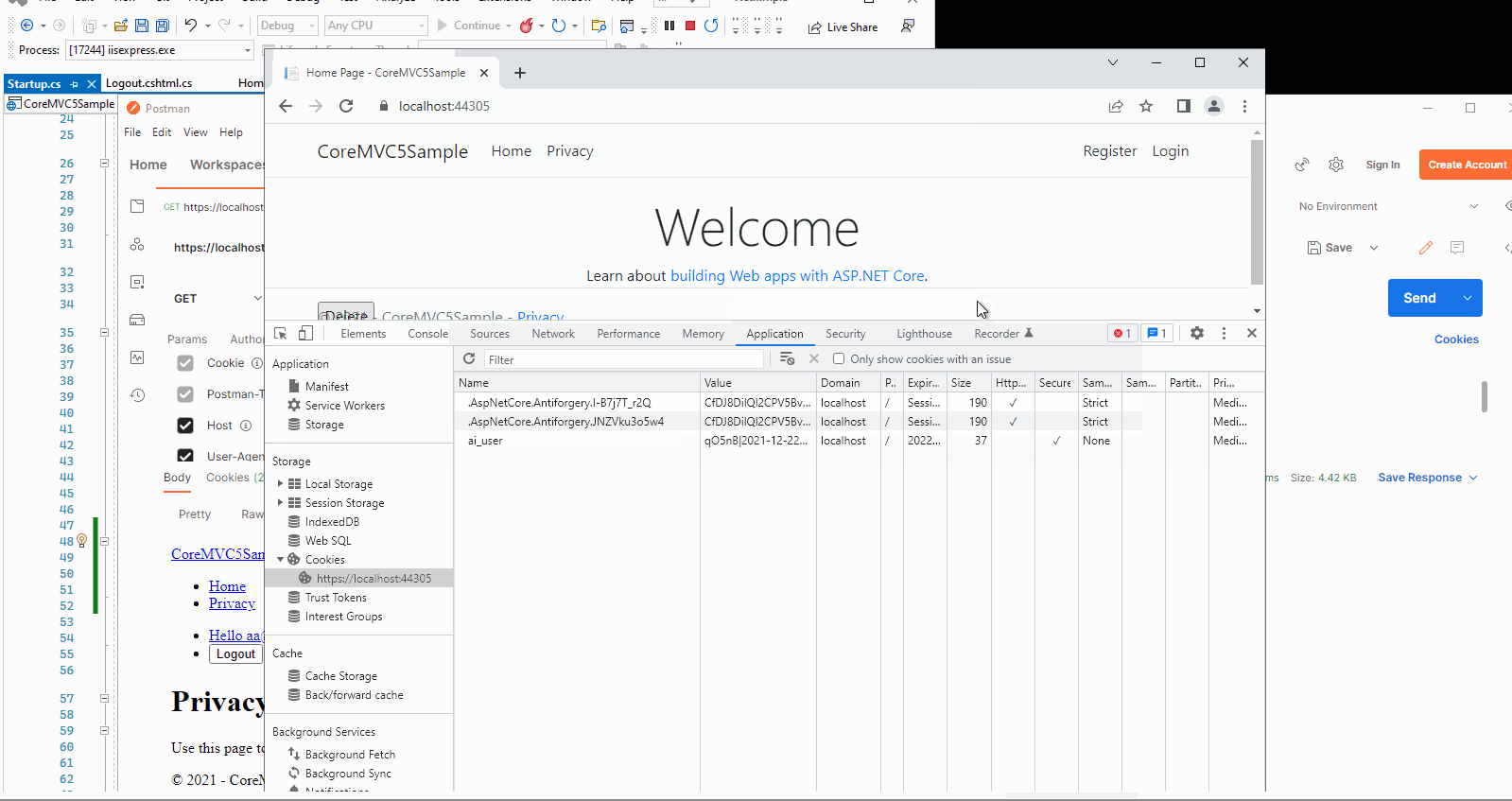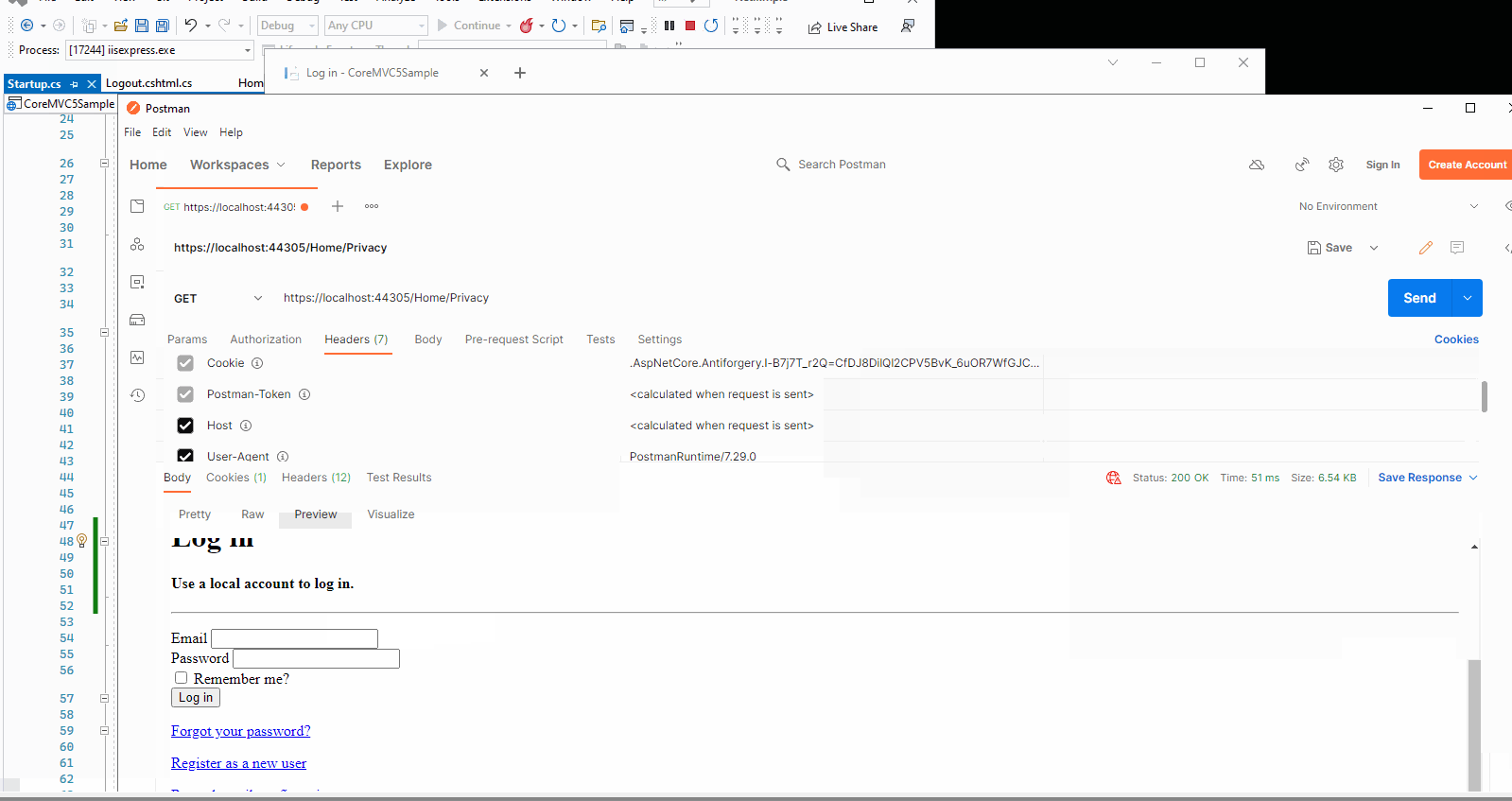
Then, I will use the Postman to check whether the cookie is invalid or not after the user logout. The result like this:
The Privacy action method was add the [Authorize] attribute, so it needs user login, after click the logout button, even through the postman sends the request with previous cookie, it still show the login page.
If the answer is the right solution, please click "Accept Answer" and kindly upvote it. If you have extra questions about this answer, please click "Comment".
Note: Please follow the steps in our documentation to enable e-mail notifications if you want to receive the related email notification for this thread.
Best regards,
Dillion

