Hello @Kenny Parsons ,
I understand that you would like to log or capture Thumbprints of successful Azure P2S VPN connections for auditing purpose.
I discussed this requirement with the Azure VPN Product Group team and below are the steps provided by them to see the thumbprints used in auth flows:
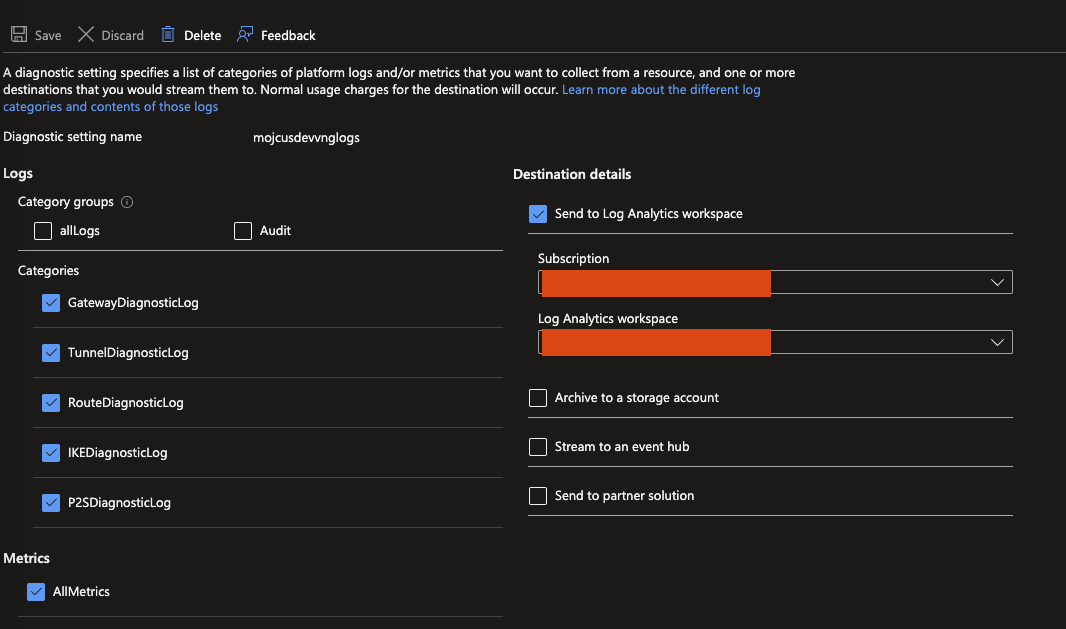
You can check the P2SDiagnosticLog to see the thumbprints used in auth flows. You can perform log analysis by following the first 6 steps in the below doc:
https://learn.microsoft.com/en-us/azure/vpn-gateway/vpn-gateway-howto-setup-alerts-virtual-network-gateway-log
Once you have enabled Diagnostics and configured the Log Analytics, follow the steps below:
1) Navigate to the Log Analytics Workspace you configured in the Azure Portal
2) Click on Logs
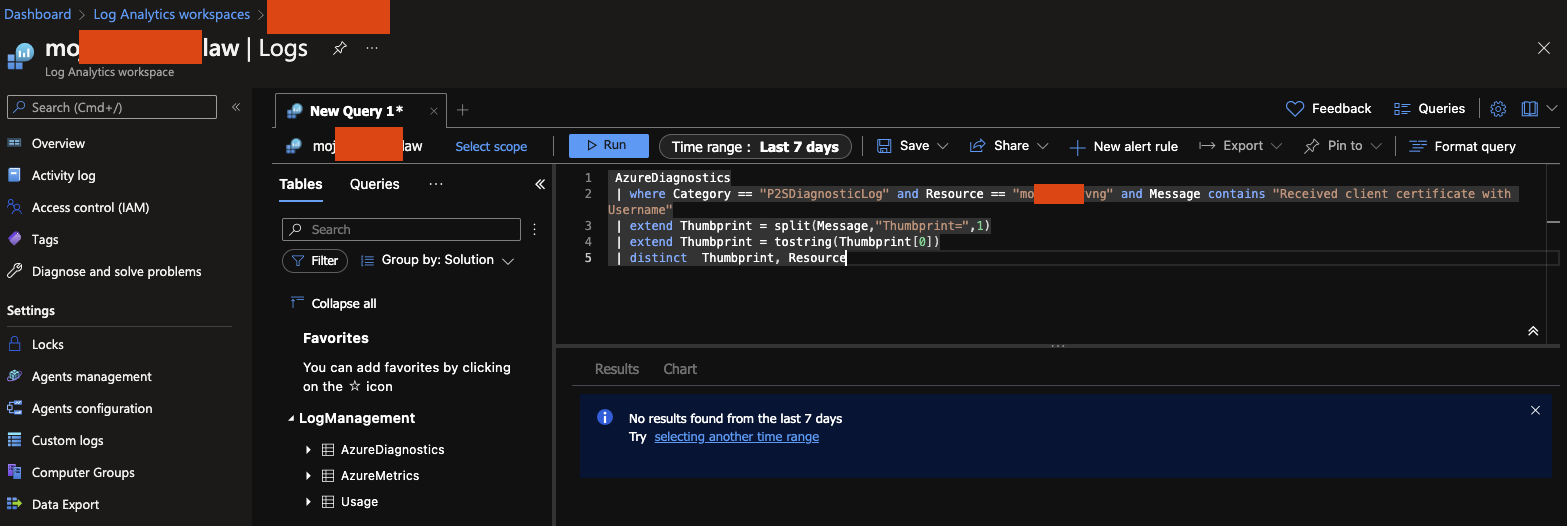
3) Paste the following replacing NameOfGateway with the name of your gateway in the Query window and click run
AzureDiagnostics
| where Category == "P2SDiagnosticLog" and Resource == "NameOfGateway" and Message contains "Received client certificate with Username"
| extend Thumbprint = split(Message,"Thumbprint=",1)
| extend Thumbprint = tostring(Thumbprint[0])
| distinct Thumbprint, Resource
4) Compare the certificate chain for the certificates with the thumbprints from the logs against your current and previous Root Certificate
Kindly let us know if the above helps or you need further assistance on this issue.
Please "Accept the answer" if the information helped you. This will help us and others in the community as well.