Hi @Deepaklal-FT ,
Regarding follow up query, I investigated in to Logs of log analytics and observed how these logs are getting captured. Please check below findings.
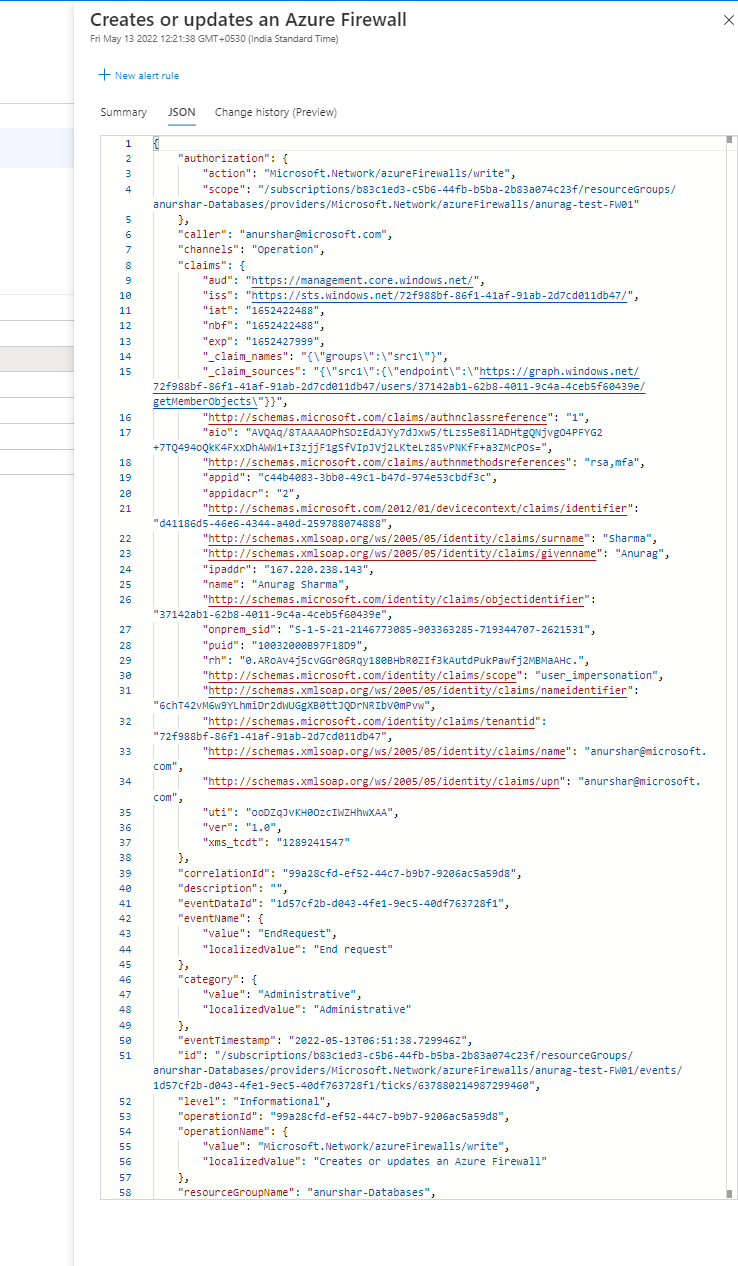
When ever we add or edit or delete rule and save settings, then behind the scenes an API request is getting send with request body. In that request body we will only have rules which will be live after save and then they get recreated or updated.
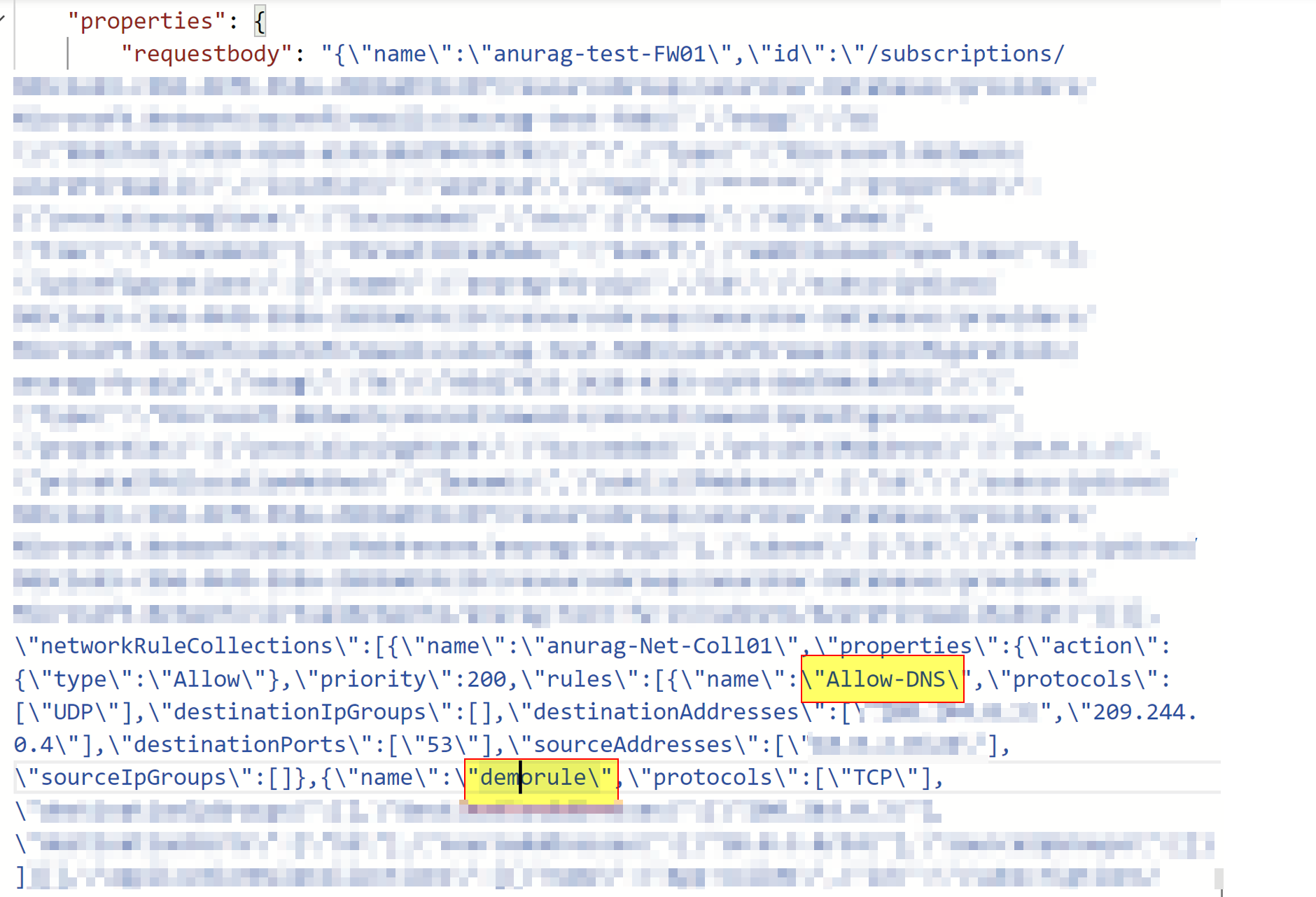
To elaborate more, kindly check below example, lets say I have one rule already called Allow-DNS. Now I added another rule called demorule. So in that case a request body will be sent with both rule names in it as below. That means, here Allow-DNS is getting recreated or updated on demorule getting create.
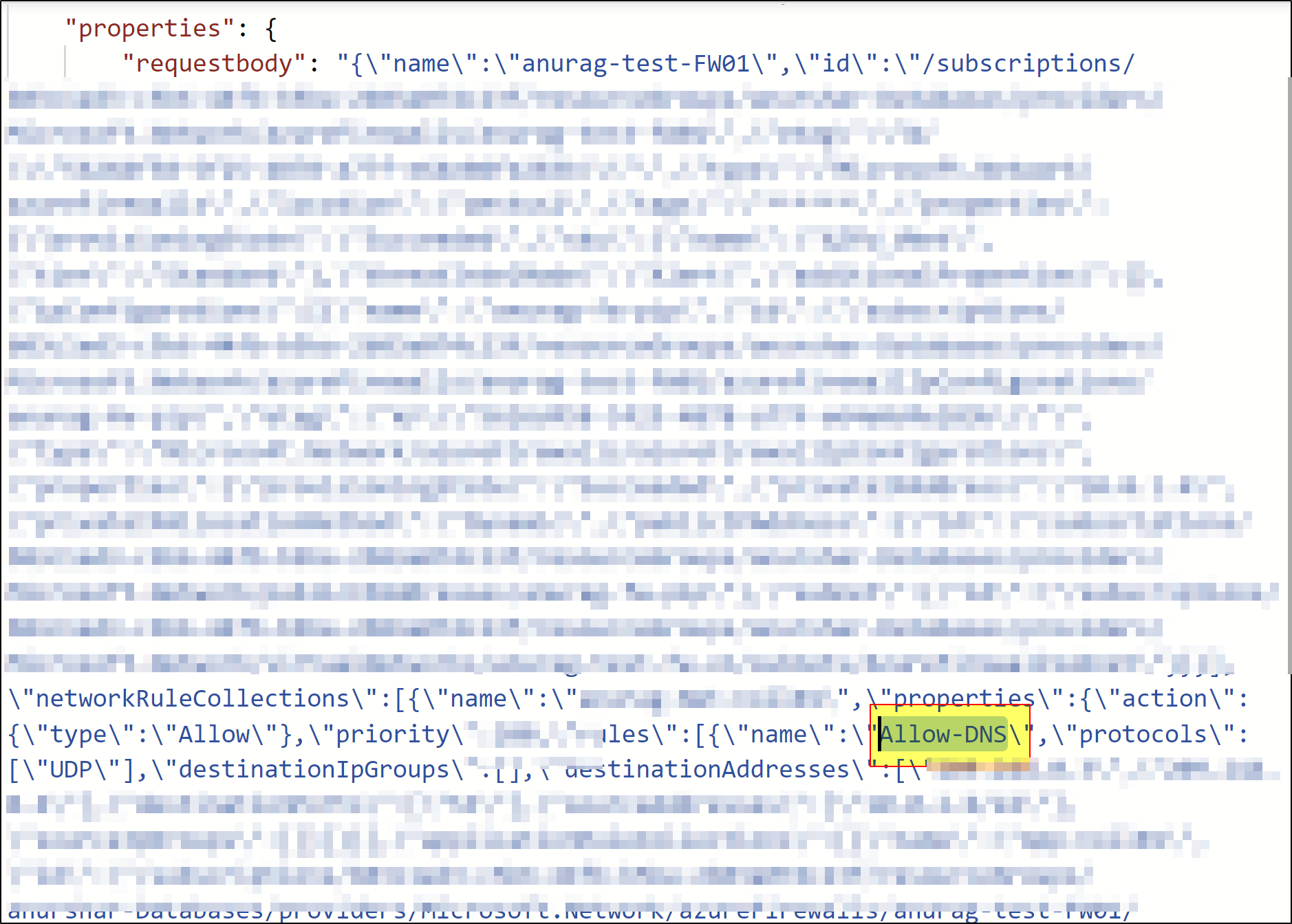
now, lets say I deleted demorule from above two rules. In this case request body will be sent with Allow-DNS rule name. That means logs will only contain Allow-DNS info in request body to convey to service that only have this rule. Please check below request body.
Hence, there is no direct way to find exactly what rule is deleted or what rule is updated. We can always get what rules are currently live and other details.
If we really want to get exactly what rules deleted or created or updated. Then kindly check below work-around option which came to my mind. Consider having some config table in SQL or any other storage and load that table with info a live rules and then in periodic fashion from log analytics get the present live rules info and cross compare with data in that configuration table and take a call which rule created or which rule deleted.
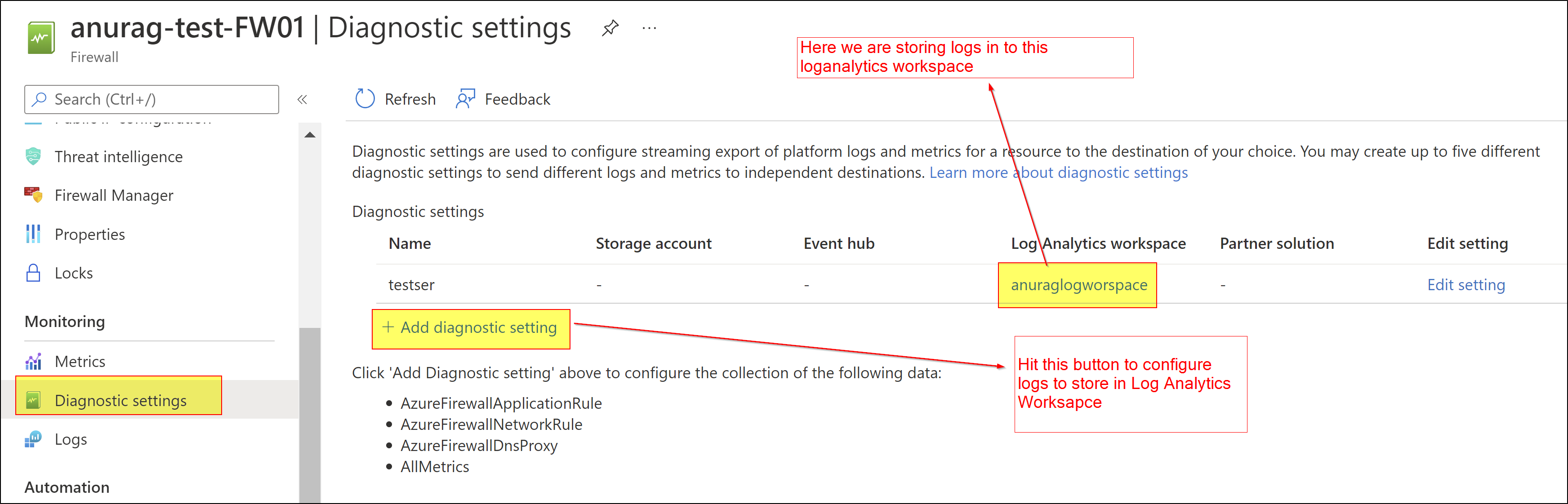
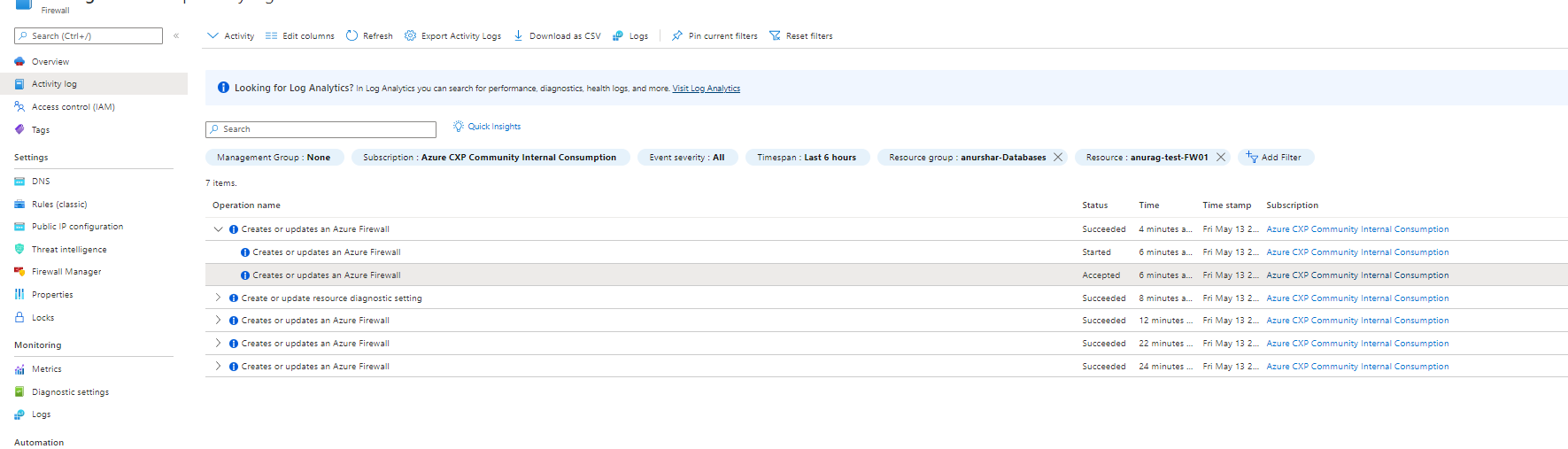
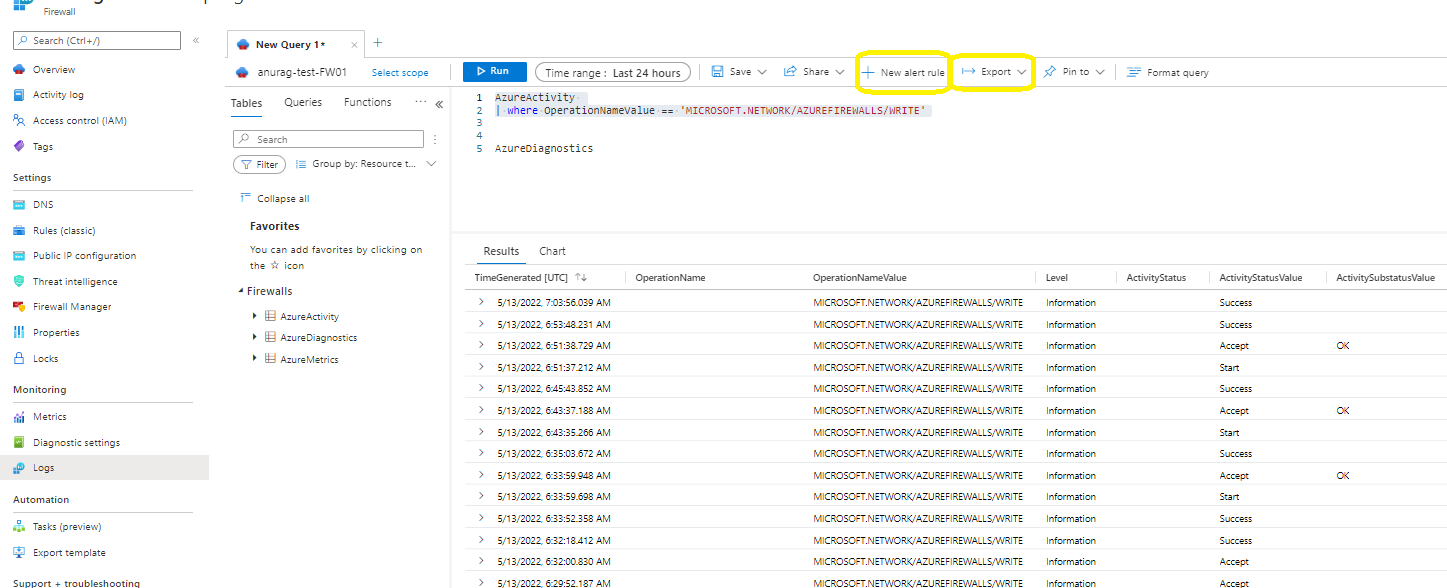
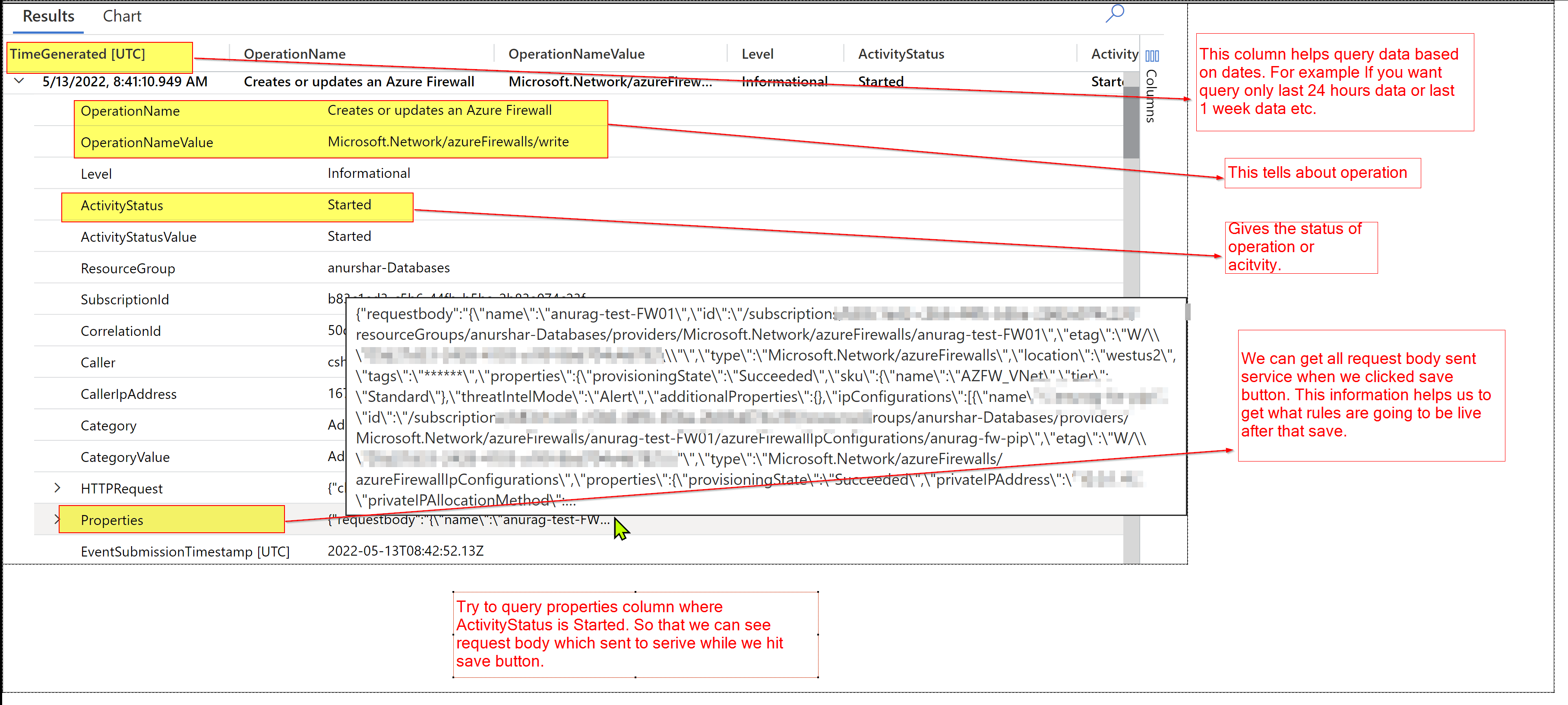
From log analytics AzureActivity log table will get the above information. Try to query data where OperationName column value is Creates or updates an Azure Firewall or OperationNameValue column value is Microsoft.Network/azureFirewalls/write.
Below are few important columns which will useful for you to query data from log analytics as per needs.
Hope this helps. Please let us know if any queries.
Please consider hitting Accept Answer button. Accepted answers help community as well.