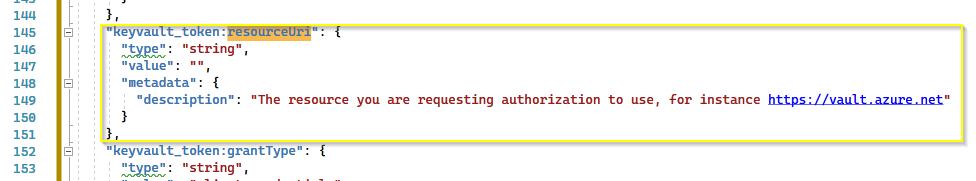
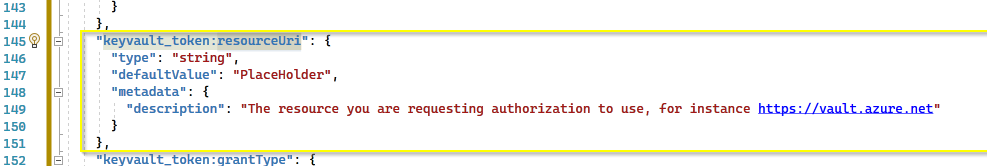
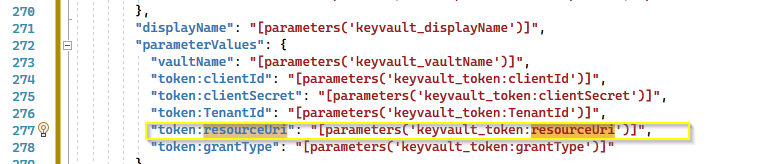
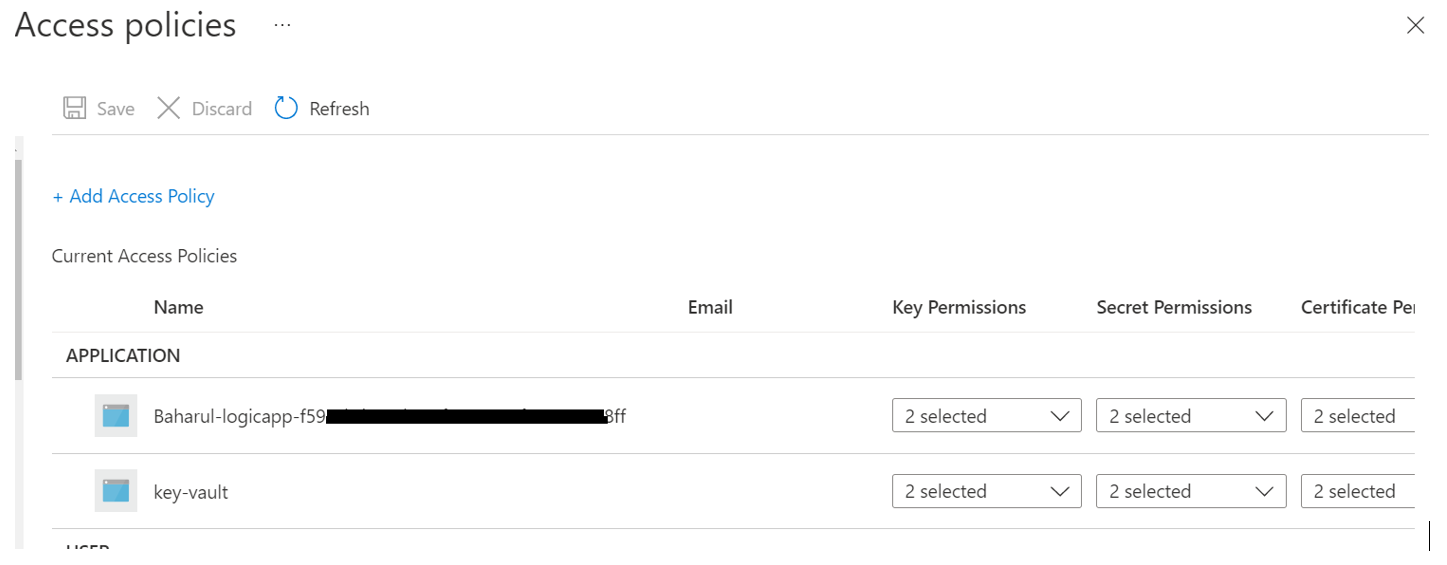
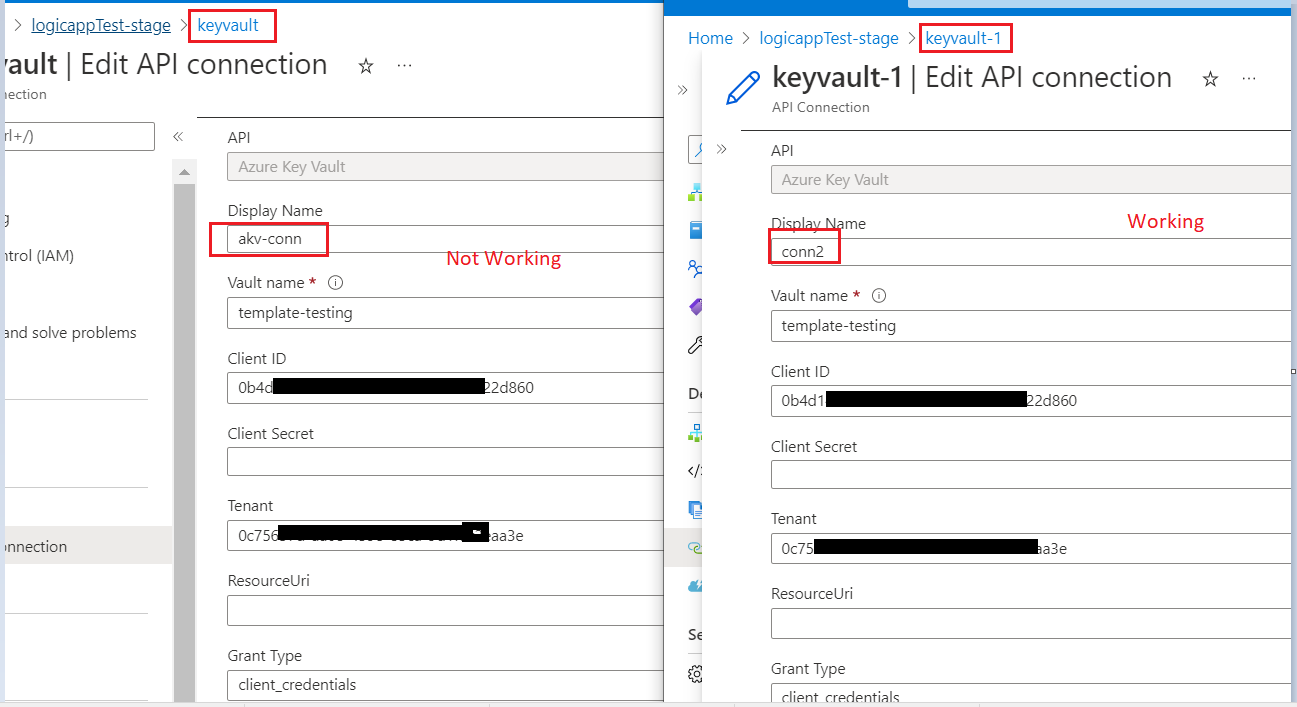
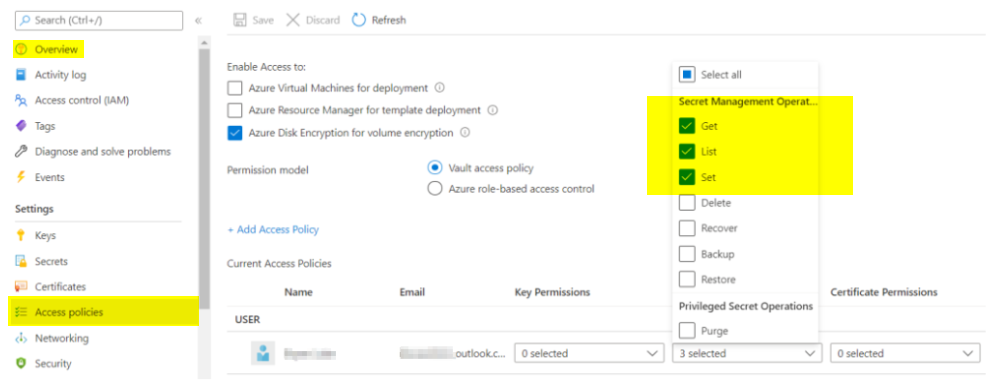
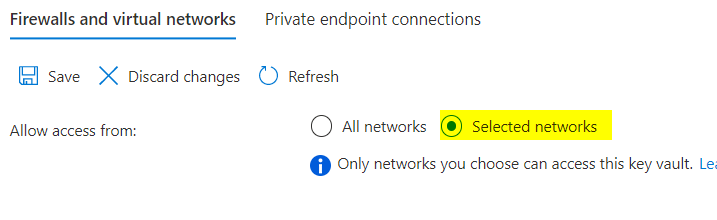
Hi @Baharul Islam , I tried 2 ways to block access to the vault. When I go to the Vault's network and block access to all networks, it throw a similar error but specific to IP blocking
{
"status": 403,
"message": "Operation against key vault 'https://DFD-RTR-YUY.vault.azure.net/' failed as connector IP address is not authorized to call the vault. If you have configured firewall on the vault, please make sure the logic app IP addresses are allowed. Please see https://aka.ms/connectors-ip-addresses\r\nclientRequestId: f4a6f817-df83-484b-82dd-f1d3fc50ab81",
"error": {
"message": "Operation against key vault 'https://DFD-RTR-YUY.vault.azure.net/' failed as connector IP address is not authorized to call the vault. If you have configured firewall on the vault, please make sure the logic app IP addresses are allowed. Please see https://aka.ms/connectors-ip-addresses"
},
"source": "keyvault-cus.azconn-cus-001.p.azurewebsites.net"
}
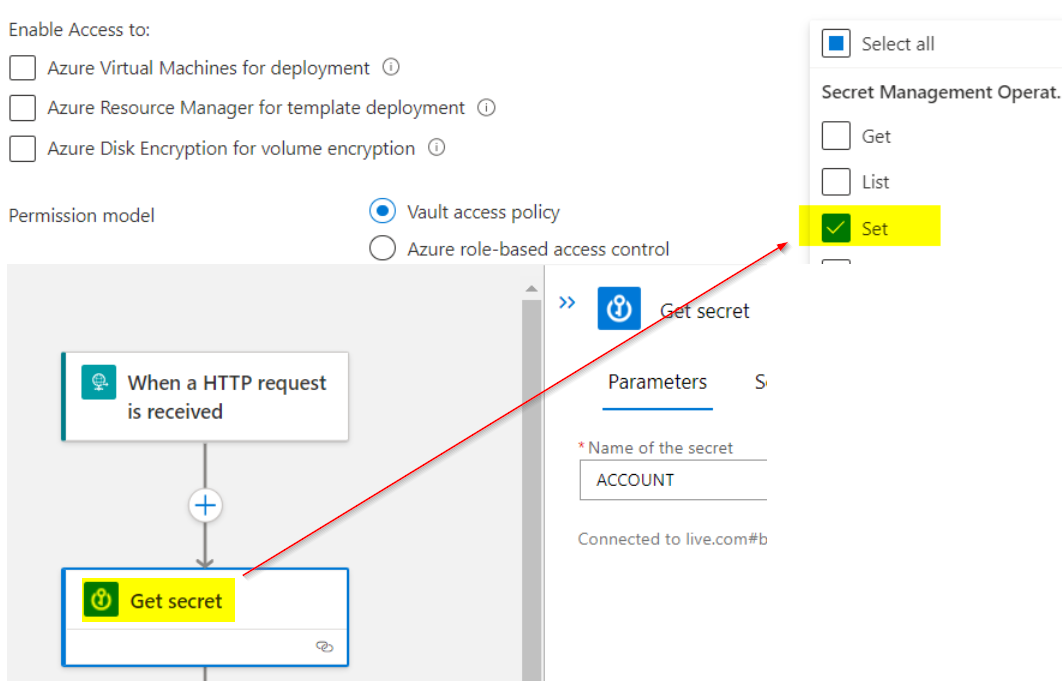
But if I go the vault and give no access or wrong permission to the policy, I get the same error message. what type of operation are you trying to perform? what permissions do you have? if seems correct, maybe the arm template has switched something to the wrong place? try switch the original and problematic logic apps to code view and look for anything it could be wrong
{
"status": 403,
"message": "Operation failed because client does not have permission to perform the operation on the key vault. Please check your permissions in the key vault access policies https://learn.microsoft.com/en-us/azure/key-vault/general/assign-access-policy-portal.\r\nclientRequestId: b55f36bf-d3de-47bd-b277-4b3dbaf18d9f",
"error": {
"message": "Operation failed because client does not have permission to perform the operation on the key vault. Please check your permissions in the key vault access policies https://learn.microsoft.com/en-us/azure/key-vault/general/assign-access-policy-portal."
},
"source": "keyvault-cus.azconn-cus-001.p.azurewebsites.net"
}
The only difference when i give wrong permission is the code
"401 Unauthorized is the status code to return when the client provides no credentials or invalid credentials. 403 Forbidden is the status code to return when a client has valid credentials but not enough privileges to perform an action on a resource."
Sounds like your logic app vault connection is using an account that validate the connection but is either with a wrong password or failing to authenticate in same level
How are you testing that? Are you using something like postman. maybe an expired token : https://learn.microsoft.com/en-us/azure/key-vault/general/rest-error-codes#http-401-unauthenticated-request