Hello @LukeCloudWalker-6128
Thanks a lot for your explanation as well as all the details given before.
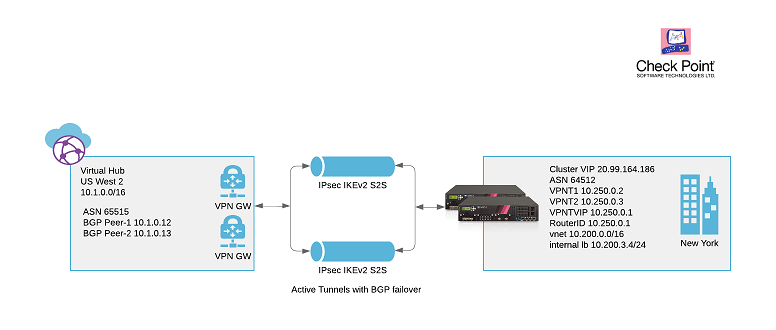
I would like to start from the peering output as it is shown below:
== Peers ==
"Local address","Peer address","Gateway instance","ASN", "Status", "Connected duration", "Routes received","Messages sent","Messages received"
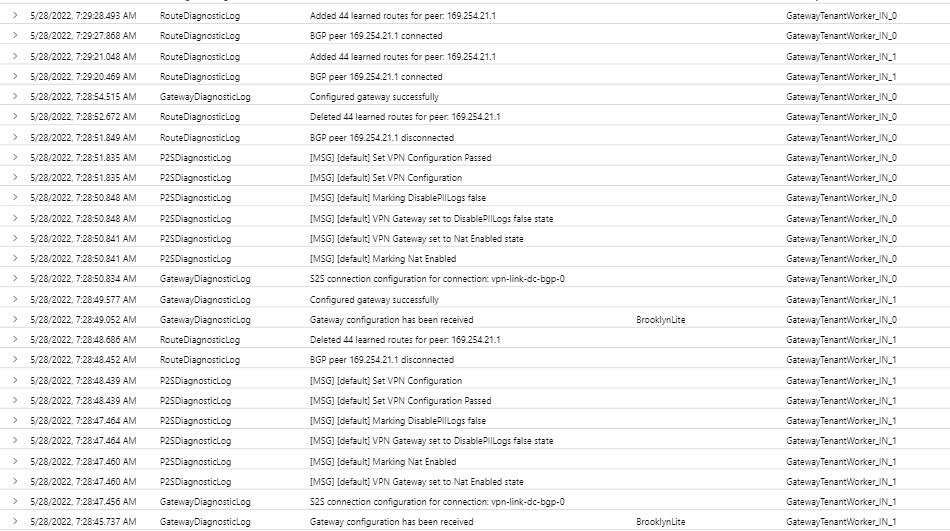
"10.0.0.12", "169.254.21.1", "Instance0", "64514", "Connected", "0:17:18", "44", "155", "125"
"10.0.0.13", "169.254.21.1", "Instance1", "64514", "Connected", "0:17:14", "44", "157", "126"
Based on the output above, On your virtual gateway hub(Virtual Wan) there are 2 instances which are Instance0("10.0.0.12") and Instance1("10.0.0.13") peering to the same peer address which is 169.254.21.1(which is your floating IP or Virtual IP on your Checkpoint cluster).
So, for me it is like to have just one tunnel because the best practice should be a separate tunnel IP addresses per each instance but you can have just one as your intended network design.
Having said that, we can take a look at the next explanation below from public documentation:
An Azure Virtual WAN connection is composed of 2 tunnels. A Virtual WAN VPN gateway is deployed in a virtual hub in active-active mode, which implies that there are separate tunnels from on-premises devices terminating on separate instances. This is the recommendation for all users. However, if the user chooses to only have 1 tunnel to one of the Virtual WAN VPN gateway instances, if for any reason (maintenance, patches etc.) the gateway instance is taken offline, the tunnel will be moved to the secondary active instance and the user may experience a reconnect. BGP sessions won't move across instances
That is the first observation but let me continue with the other ones :)
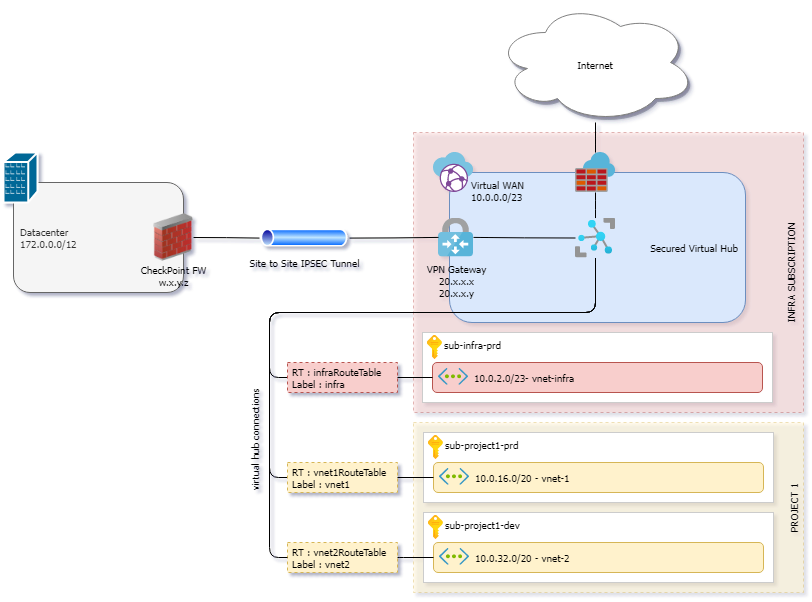
-On your network topology I could see that you have sub-project1-prd,sub-project1-dev and sub-infra-prd.
so the question that I have is... Are they a separate subcription or resource groups located on differents regions?
-I have seen that there are some default routes with different origin or source peer address which are "10.0.0.68" and "10.0.0.69"....
So, Do they belong to your on-premises IP allocation?
-If you want to keep the current design... I am wondering if you have applied a "next-hop-self" policy on your Checkpoint FW under BGP protocol. Could you confirm it pls?
Looking forward to your feedback,
Please "Accept the answer" if the information helped you. This will help us and others in the community as well.