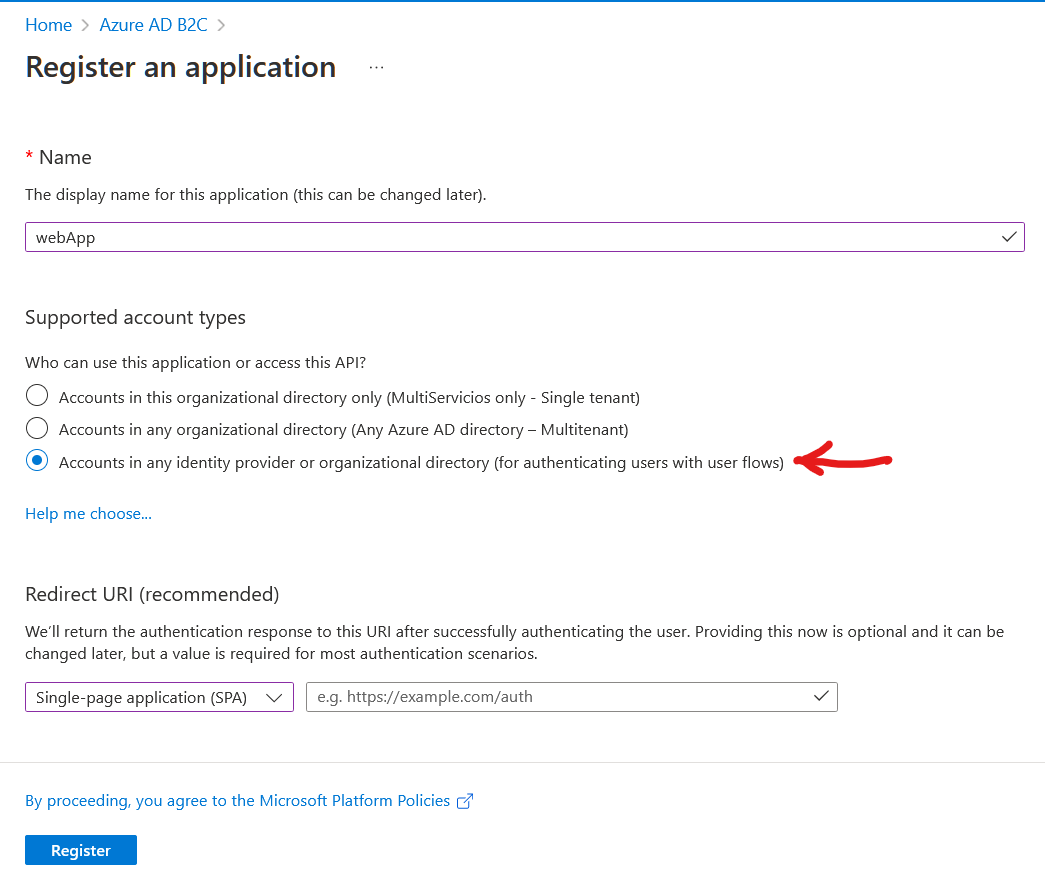
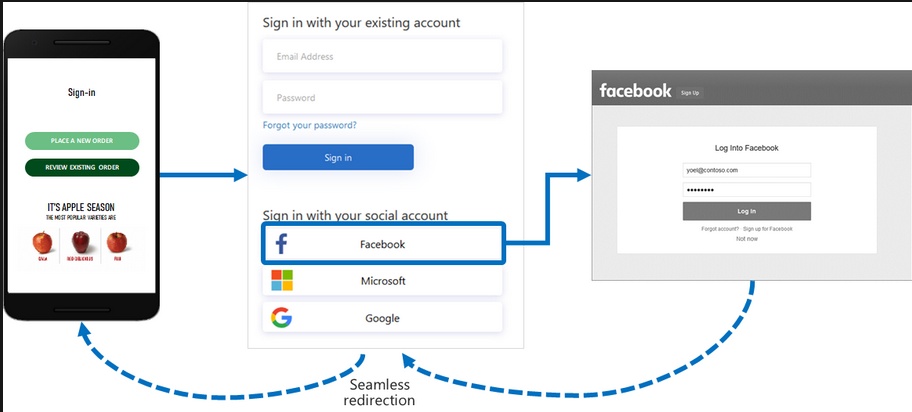
Hi @Luis Diego Cáceres García ,
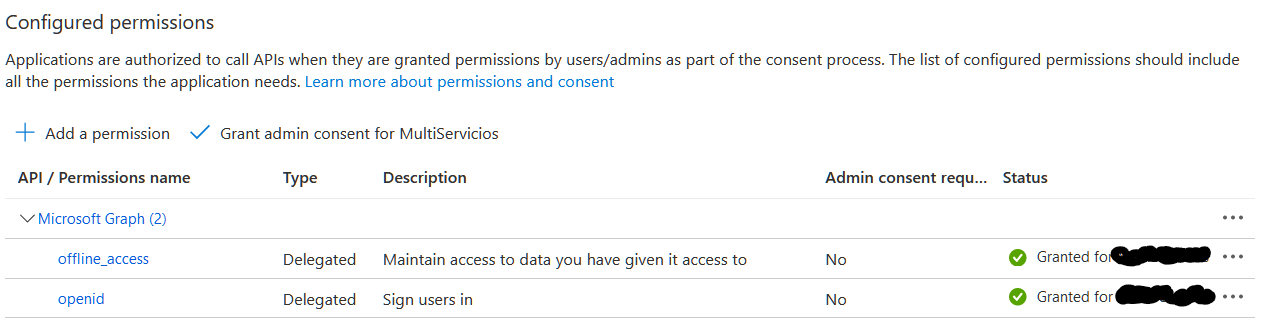
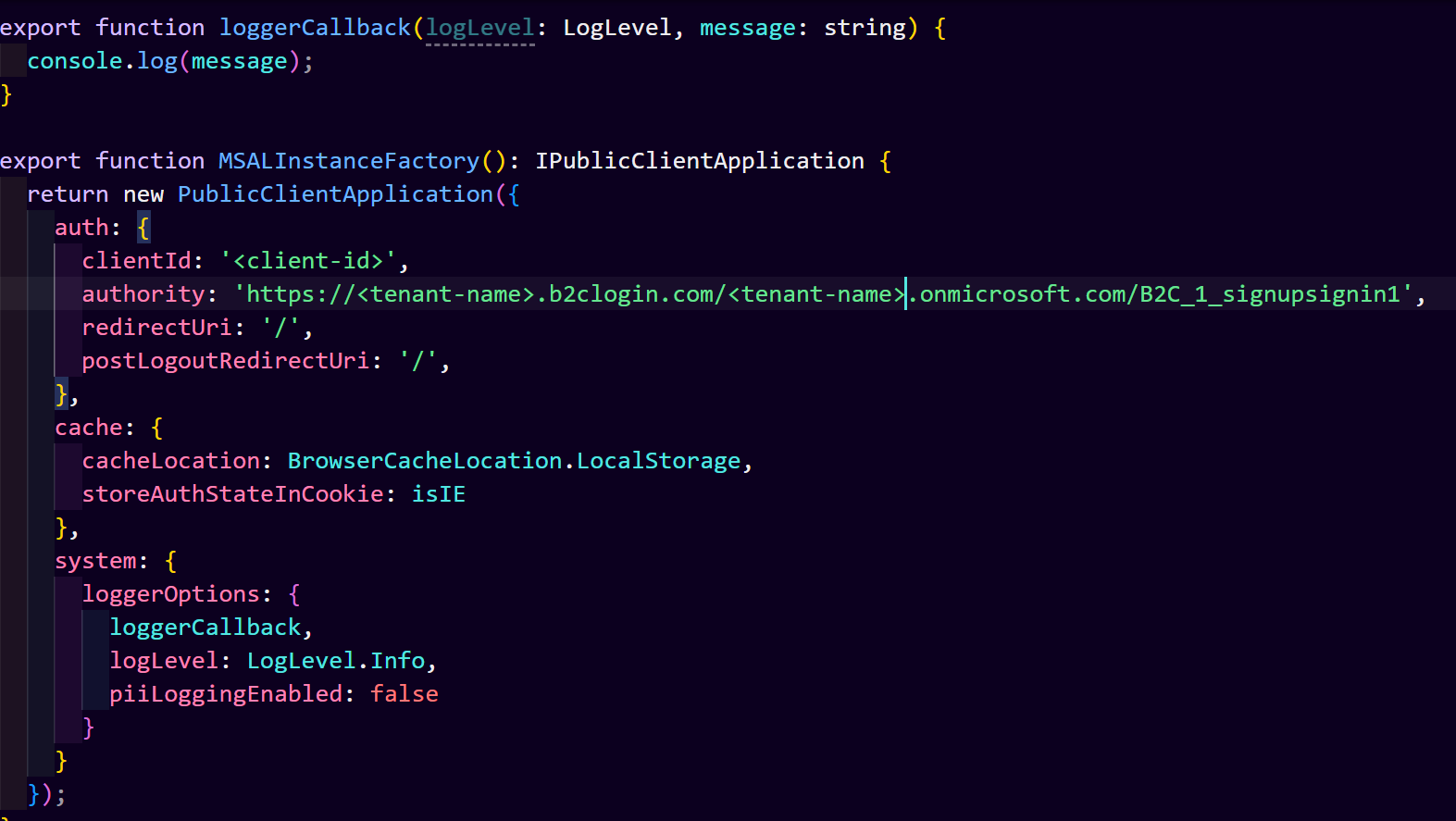
As mentioned earlier, for B2C the authority URL would be "https://<tenantName>.b2clogin.com/<tenantName>.onmicrosoft.com/B2C_1_signupsignin.
When you added B2C's authority URL, then error states that authority need to add in knownAuthorities config parameter to trust the B2C authority.
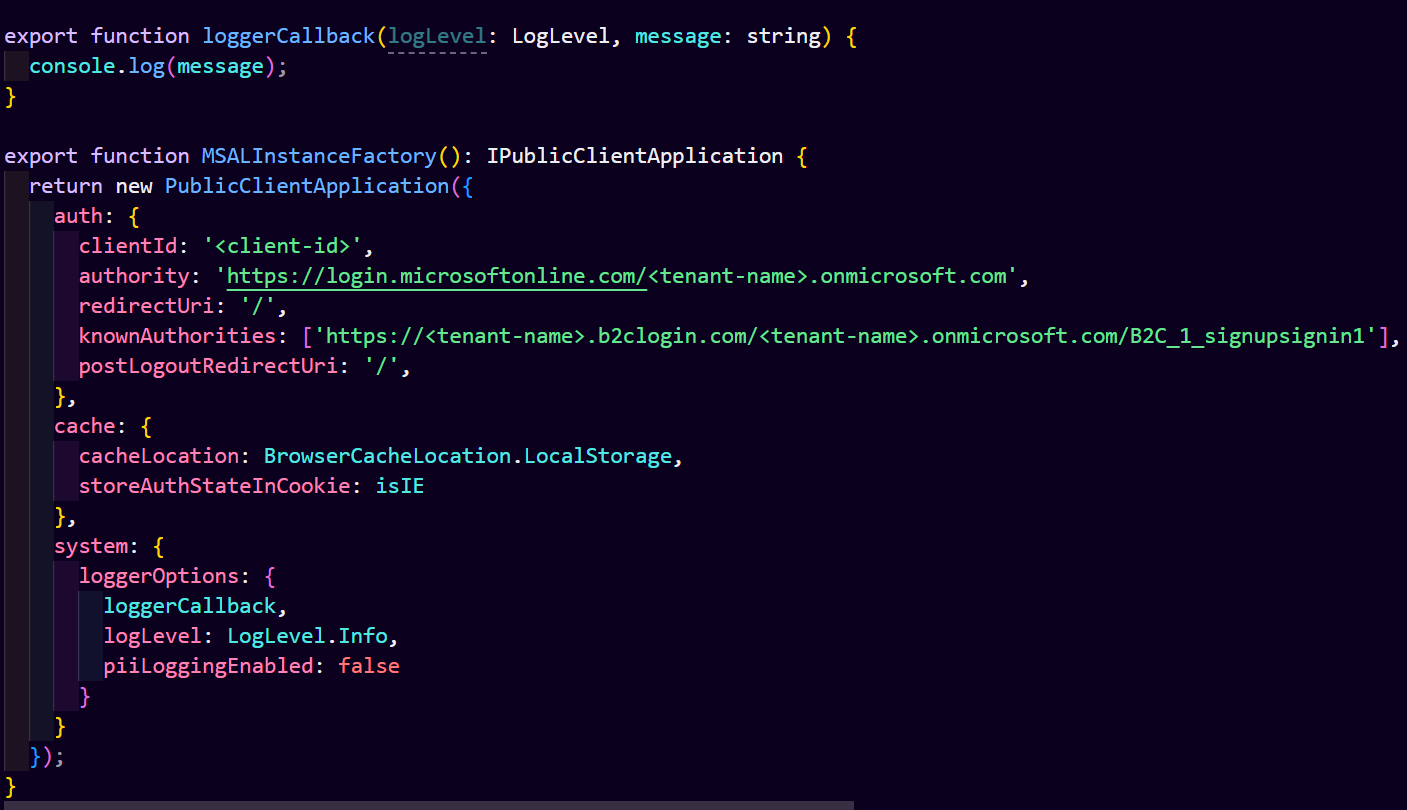
You need to add below configration in knownAuthorities:
export const msalConfig: Configuration = {
auth: {
clientId: 'xxx-xx-xx-xxx-xxxx',
authority: b2cPolicies.authorities.signUpSignIn.authority,
knownAuthorities: [b2cPolicies.authorityDomain] //Mark your B2C tenant's domain as trusted.
}
where b2cPolicies configured policies in B2C tenant and authority domain.
export const b2cPolicies = {
names: {
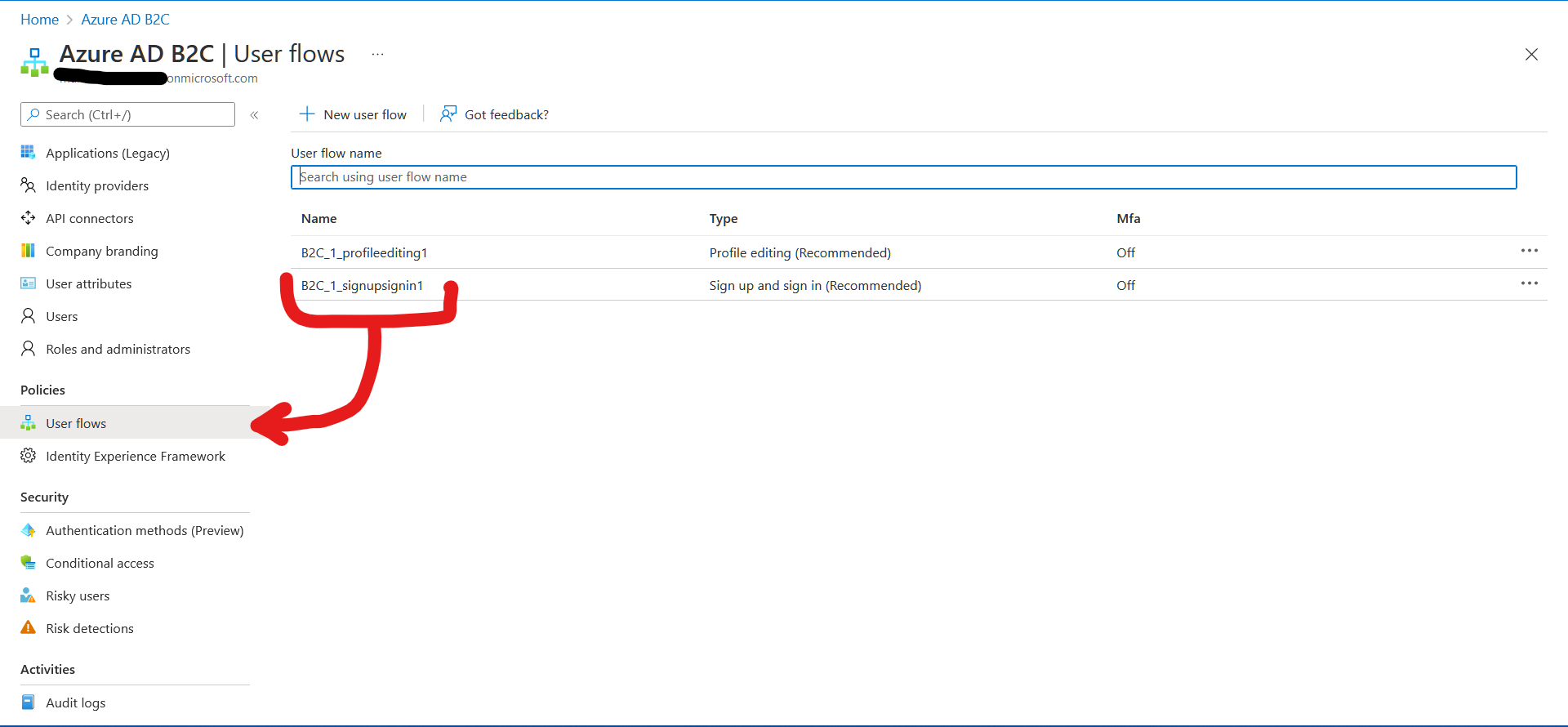
signUpSignIn: "B2C_1_signupsignin",
editProfile: "B2C_1_profileEditing"
},
authorities: {
signUpSignIn: {
authority: "https://shwb2c.b2clogin.com/shwb2c.onmicrosoft.com/B2C_1_signupsignin",
},
editProfile: {
authority: "https://shwb2c.b2clogin.com/shwb2c.onmicrosoft.com/B2C_1_profileEditing"
}
},
authorityDomain: "shwb2c.b2clogin.com"
};
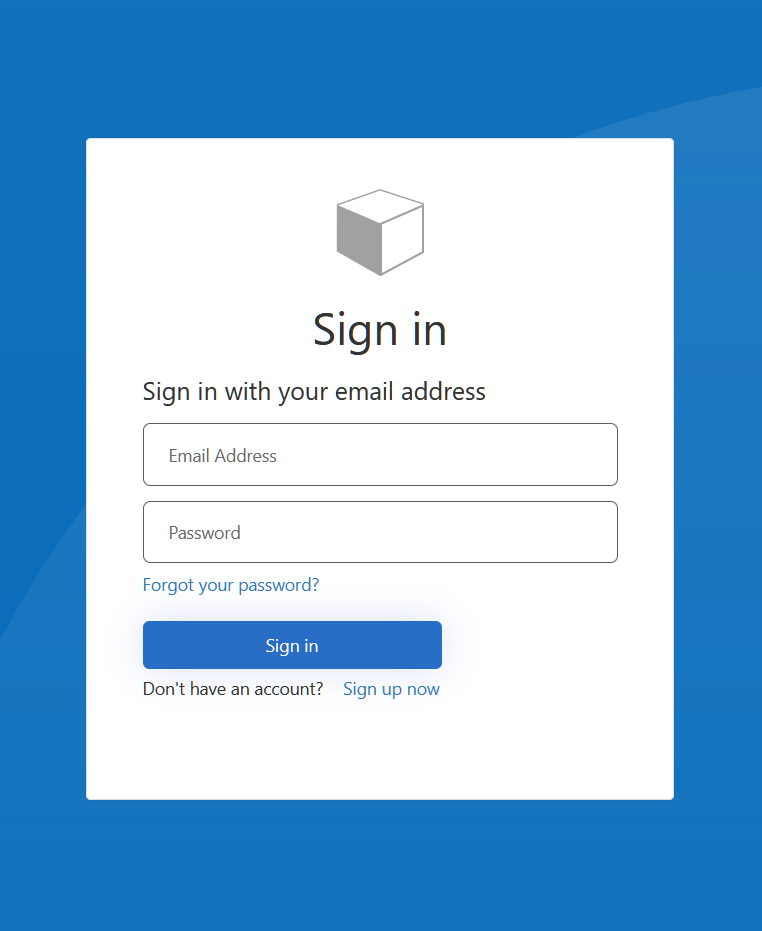
I tested the scenario in my lab and able to authenticate successfully in B2C tenant.
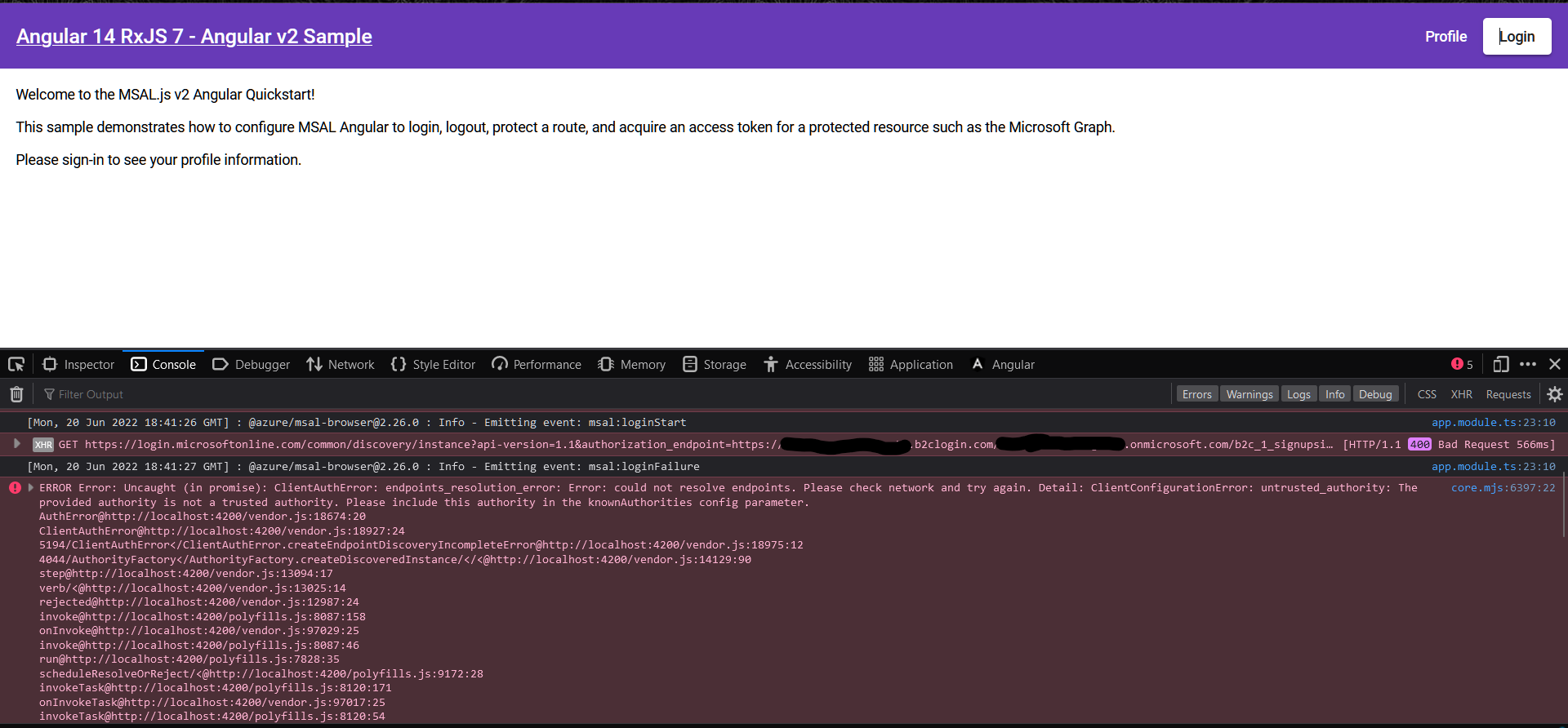
As you updated authority URL to https://login.microsoftonline.com which redirect application page to Azure AD sign in audience rather than B2C sign in page.
Hope this will help.
Thanks,
Shweta
--------------------------------------
Please remember to "Accept Answer" if answer helped you.