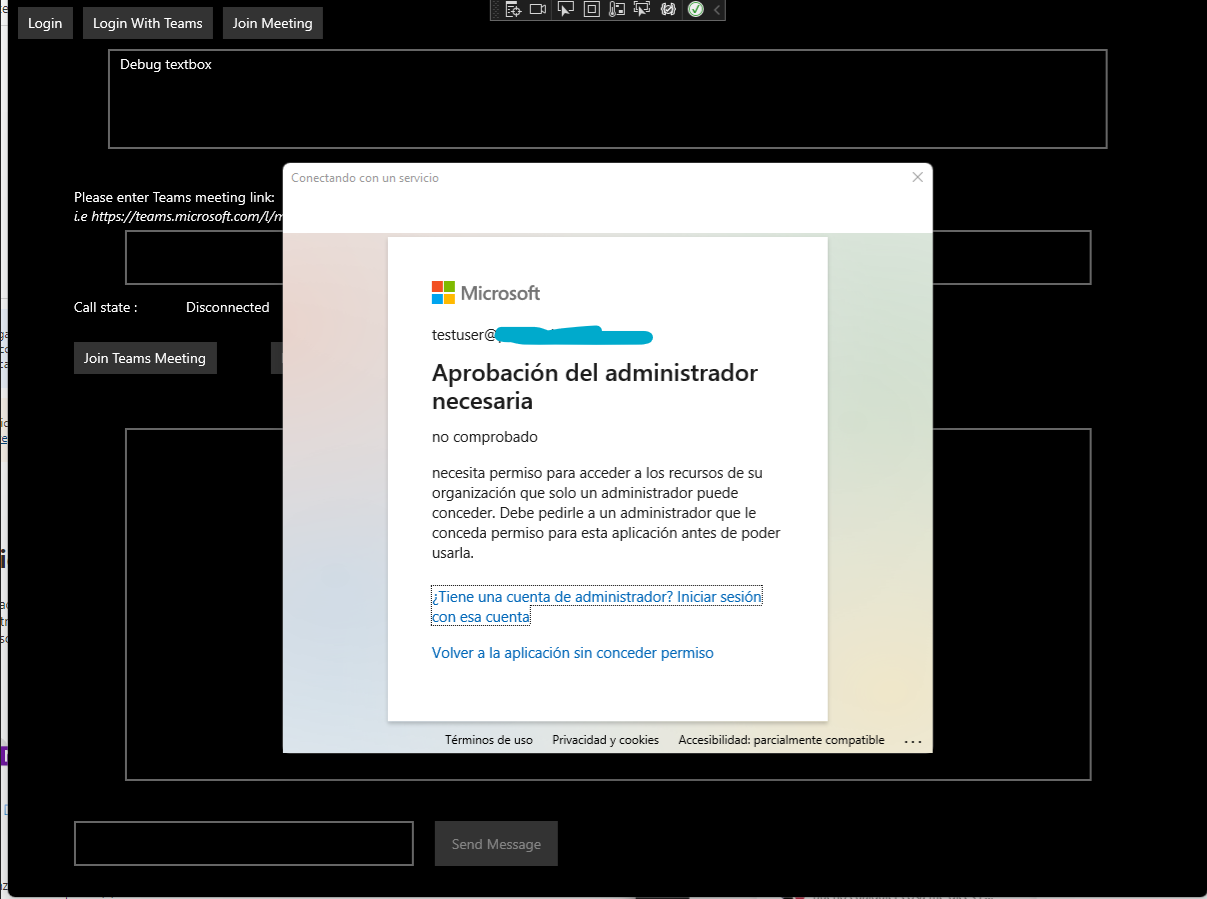
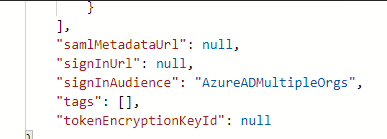
Hello @Carlos Corona , to ensure access to multi-tenant application to all users you need to:
- Mark your app as publisher verified. This will help with the first error.
- Use the
organizationsorcommontenant in your Azure AD endpoints. This will allow external users can acquire tokens. E.g.https://login.microsoftonline.com/organizations/oauth2/v2.0/authorize?client_id=[my client id]
Let us know if this answer was helpful to you or if you need additional assistance. If it was helpful, please remember to accept it and complete the quality survey so that others in the community with similar questions can more easily find a rated solution.