Hello @CsK and thanks for reaching out. Great to see you could find a solution to your issue. I'm adding my answer to cover each of your questions and add some more content that may help you and others from the community:
- I exposed that 1 scope mentioned in there and no app roles. It now returns the code 401 when I try to test it in Swagger which is expected but how do I acquire a Bearer token for testing it in Postman? You can import and use the Azure AD v2.0 Protocols Postman Collections
- I know that I can configure Swagger to use login on the UI but it seems that everything needs a redirect uri. You need to set the appropiate Swagger redirect uri (E.g. https://app.swaggerhub.com/oauth2_redirect)
- Do I need to set a redirect uri anyway to be able to test it? Yes it is
- Or is this the right scenario for me?
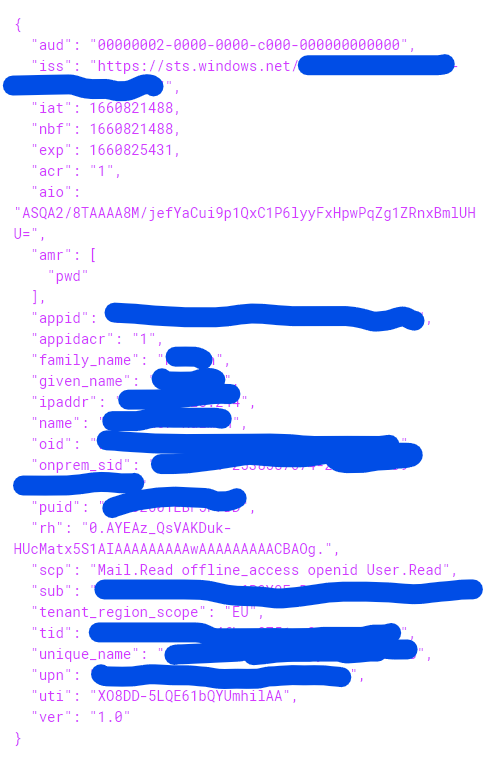
It is. The basic setup is to acquire an id token in order to get logged-in your frontend app to later acquire an access token to get authorized by your backend app. Out of the box each app expects tokens containing their app/client id in the token
audclaim. Alternatively, and usually in the backend, you might enable validation of access tokens issued to another apps. That's whereoptions.TokenValidationParameters.ValidAudiencecomes handy.
For more information about frontend to backend setups please take a look to:
- Scenario: A web app that authenticates users and calls web APIs
- Scenario: SPA that signs in users and calls web API
Let us know if you need additional assistance. If the answer was helpful, please accept it and complete the quality survey so that others can find a solution.