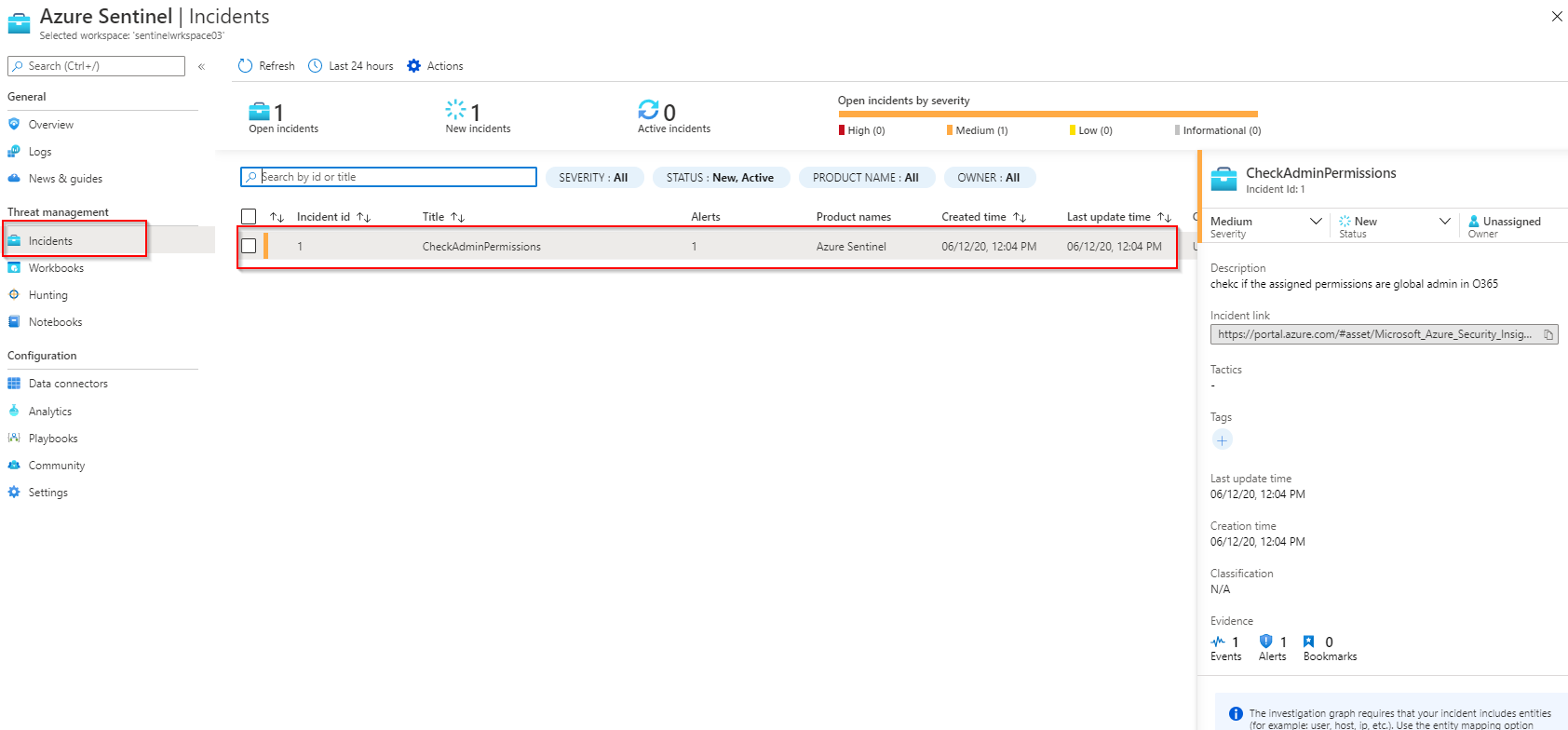
You can use event query from Analytics blade to create a Rule which will trigger an Incident if any user gets assigned a Global Administrator (Company administrator) role from Office 365 portal.
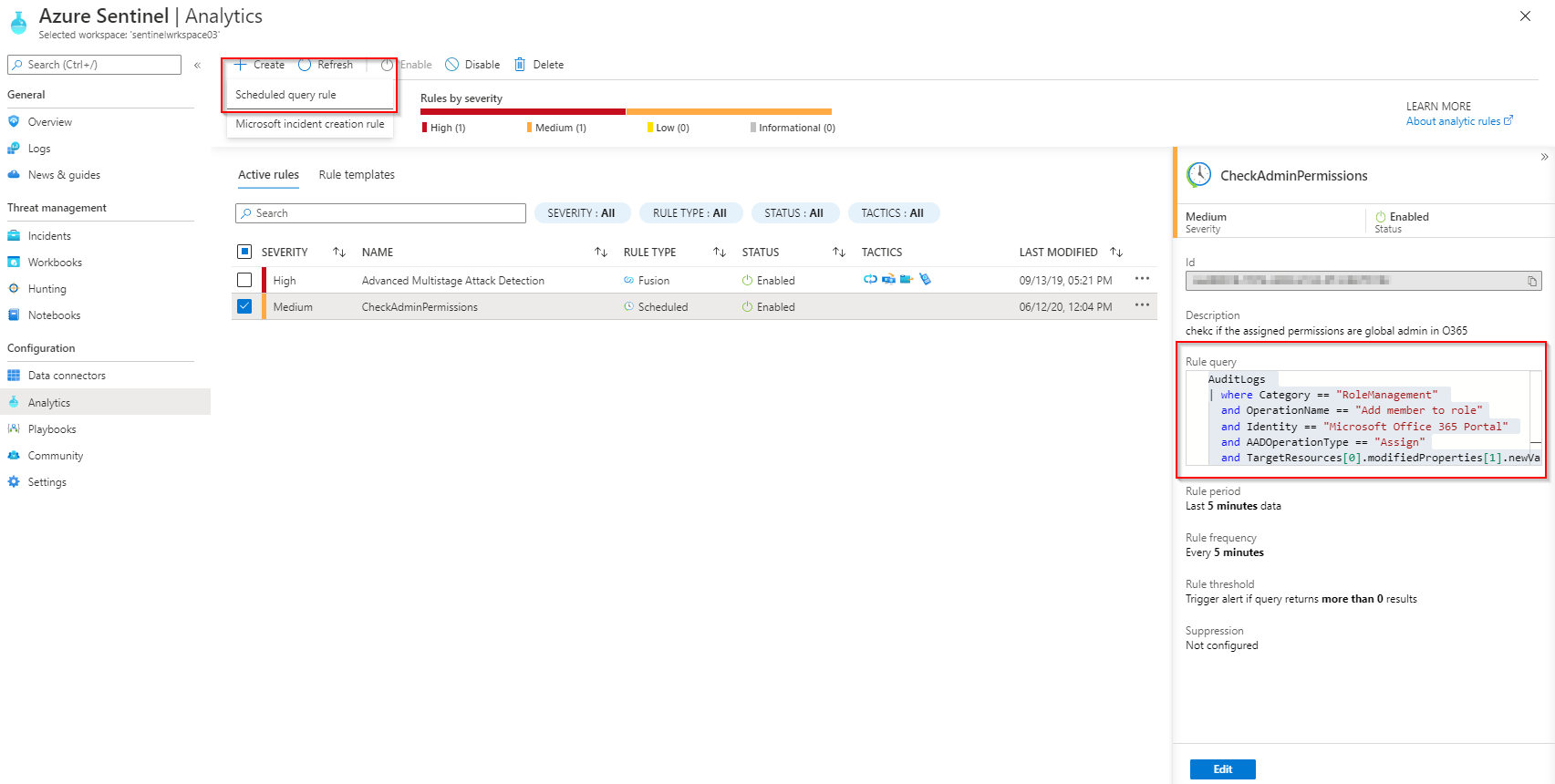
Please find below the event rule which you can use on Azure AD Audit logs -
AuditLogs
| where Category == "RoleManagement"
and OperationName == "Add member to role"
and Identity == "Microsoft Office 365 Portal"
and AADOperationType == "Assign"
and TargetResources[0].modifiedProperties[1].newValue contains "Company Administrator"
Once this rule is run Sentinel will display incidents under "Incidents" blade which you can further investigate. You can also modify the above query and the event rule to display only relevant information.