Configure point-to-site VPN clients: certificate authentication - Linux
This article helps you connect to your Azure virtual network (VNet) using VPN Gateway point-to-site (P2S) and Certificate authentication from a Linux client. There are multiple sets of steps in this article, depending on the tunnel type you selected for your P2S configuration, the operating system, and the VPN client that is used to connect.
Before you begin
Before beginning, verify that you are on the correct article. The following table shows the configuration articles available for Azure VPN Gateway P2S VPN clients. Steps differ, depending on the authentication type, tunnel type, and the client OS.
| Authentication | Tunnel type | Generate config files | Configure VPN client |
|---|---|---|---|
| Azure certificate | IKEv2, SSTP | Windows | Native VPN client |
| Azure certificate | OpenVPN | Windows | - OpenVPN client - Azure VPN client |
| Azure certificate | IKEv2, OpenVPN | macOS-iOS | macOS-iOS |
| Azure certificate | IKEv2, OpenVPN | Linux | Linux |
| Microsoft Entra ID | OpenVPN (SSL) | Windows | Windows |
| Microsoft Entra ID | OpenVPN (SSL) | macOS | macOS |
| RADIUS - certificate | - | Article | Article |
| RADIUS - password | - | Article | Article |
| RADIUS - other methods | - | Article | Article |
Important
Starting July 1, 2018, support is being removed for TLS 1.0 and 1.1 from Azure VPN Gateway. VPN Gateway will support only TLS 1.2. Only point-to-site connections are impacted; site-to-site connections won't be affected. If you’re using TLS for point-to-site VPNs on Windows 10 or later clients, you don’t need to take any action. If you're using TLS for point-to-site connections on Windows 7 and Windows 8 clients, see the VPN Gateway FAQ for update instructions.
Generate certificates
For certificate authentication, a client certificate must be installed on each client computer. The client certificate you want to use must be exported with the private key, and must contain all certificates in the certification path. Additionally, for some configurations, you'll also need to install root certificate information.
For information about working with certificates, see Point-to site: Generate certificates.
Generate VPN client configuration files
All of the necessary configuration settings for the VPN clients are contained in a VPN client profile configuration zip file. The VPN client profile configuration files that you generate are specific to the P2S VPN gateway configuration for the virtual network. If there are any changes to the P2S VPN configuration after you generate the files, such as changes to the VPN protocol type or authentication type, you need to generate new VPN client profile configuration files and apply the new configuration to all of the VPN clients that you want to connect. For more information about P2S connections, see About point-to-site VPN.
To generate configuration files using the Azure portal:
In the Azure portal, go to the virtual network gateway for the virtual network to which you want to connect.
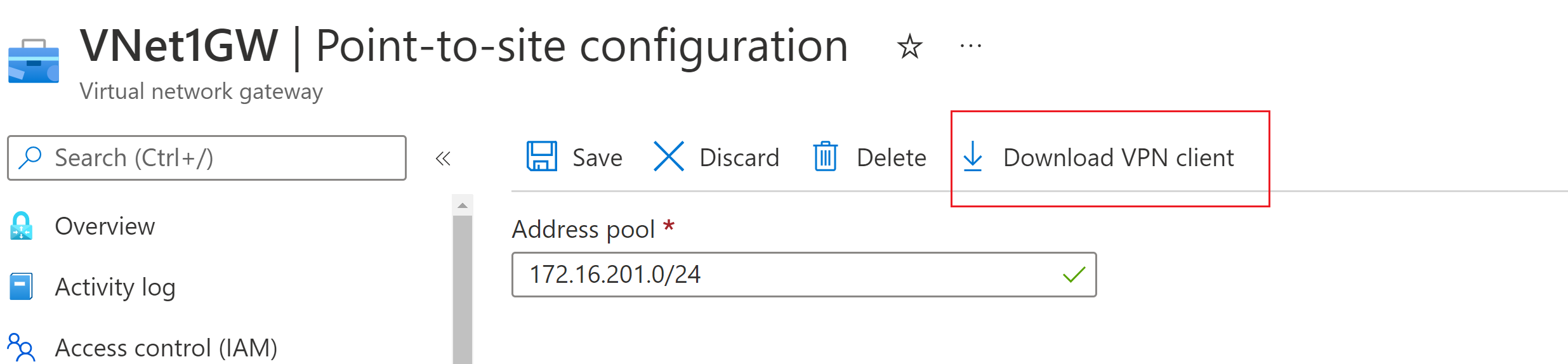
On the virtual network gateway page, select Point-to-site configuration to open the Point-to-site configuration page.
At the top of the Point-to-site configuration page, select Download VPN client. This doesn't download VPN client software, it generates the configuration package used to configure VPN clients. It takes a few minutes for the client configuration package to generate. During this time, you might not see any indications until the packet generates.
Once the configuration package is generated, your browser indicates that a client configuration zip file is available. It's named the same name as your gateway.
Unzip the file to view the folders. You'll use some, or all, of these files to configure your VPN client. The files that are generated correspond to the authentication and tunnel type settings that you configured on the P2S server.
Next, configure the VPN client. Select from the following instructions:
- IKEv2 tunnel type steps for strongSwan
- OpenVPN tunnel type steps for OpenVPN client
IKEv2 - strongSwan steps
Install strongSwan
The following configuration was used when specifying commands:
- Computer: Ubuntu Server 18.04
- Dependencies: strongSwan
Use the following commands to install the required strongSwan configuration:
sudo apt-get update
sudo apt-get upgrade
sudo apt install strongswan
sudo apt install strongswan-pki
sudo apt install libstrongswan-extra-plugins
sudo apt install libtss2-tcti-tabrmd0
Install certificates
A client certificate is required for authentication when using the Azure certificate authentication type. A client certificate must be installed on each client computer. The exported client certificate must be exported with the private key, and must contain all certificates in the certification path. Make sure that the client computer has the appropriate client certificate installed before proceeding to the next section.
For information about client certificates, see Generate certificates - Linux.
View VPN client profile files
Go to the downloaded VPN client profile configuration files. You can find all of the information that you need for configuration in the Generic folder. Azure doesn’t provide a mobileconfig file for this configuration.
If you don't see the Generic folder, check the following items, then generate the zip file again.
- Check the tunnel type for your configuration. It's likely that IKEv2 wasn’t selected as a tunnel type.
- On the VPN gateway, verify that the SKU isn’t Basic. The VPN Gateway Basic SKU doesn’t support IKEv2. Then, select IKEv2 and generate the zip file again to retrieve the Generic folder.
The Generic folder contains the following files:
- VpnSettings.xml, which contains important settings like server address and tunnel type.
- VpnServerRoot.cer, which contains the root certificate required to validate the Azure VPN gateway during P2S connection setup.
After viewing the files, continue with the steps that you want to use:
strongSwan GUI steps
This section walks you through the configuration using the strongSwan GUI. The following instructions were created on Ubuntu 18.0.4. Ubuntu 16.0.10 doesn’t support strongSwan GUI. If you want to use Ubuntu 16.0.10, you’ll have to use the command line. The following examples may not match screens that you see, depending on your version of Linux and strongSwan.
Open the Terminal to install strongSwan and its Network Manager by running the command in the example.
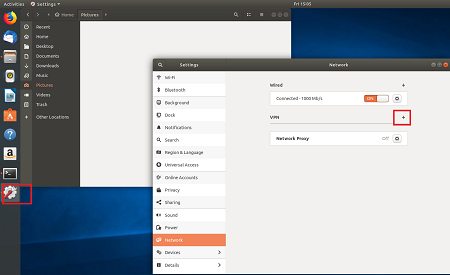
sudo apt install network-manager-strongswanSelect Settings, then select Network. Select the + button to create a new connection.
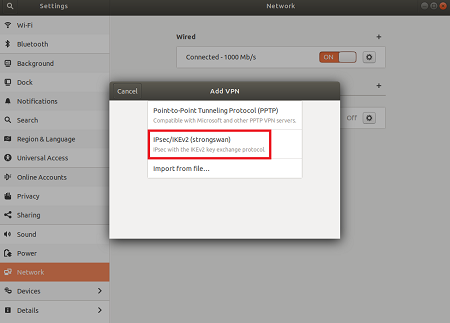
Select IPsec/IKEv2 (strongSwan) from the menu, and double-click.
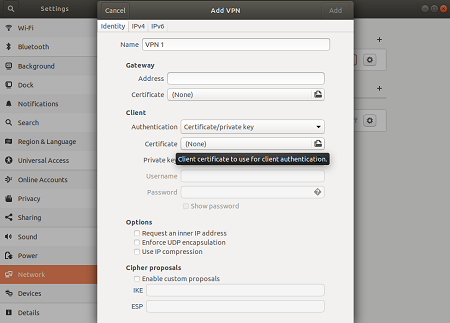
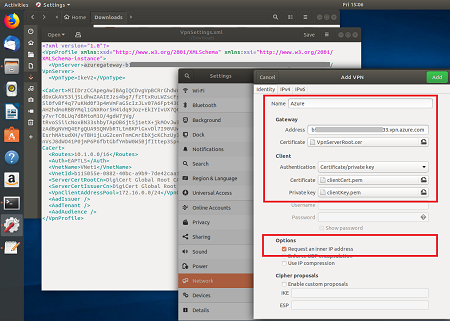
On the Add VPN page, add a name for your VPN connection.
Open the VpnSettings.xml file from the Generic folder contained in the downloaded VPN client profile configuration files. Find the tag called VpnServer and copy the name, beginning with 'azuregateway' and ending with '.cloudapp.net'.
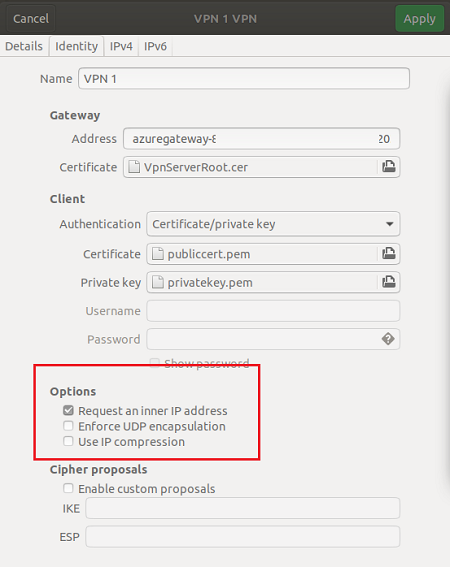
Paste the name in the Address field of your new VPN connection in the Gateway section. Next, select the folder icon at the end of the Certificate field, browse to the Generic folder, and select the VpnServerRoot file.
In the Client section of the connection, for Authentication, select Certificate/private key. For Certificate and Private key, choose the certificate and the private key that were created earlier. In Options, select Request an inner IP address. Then, select Add.
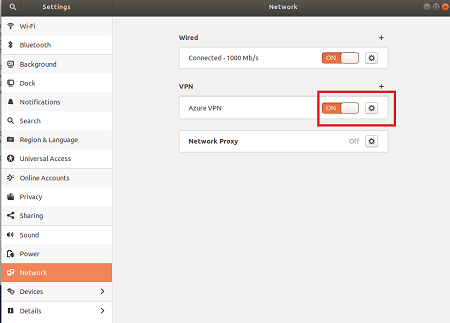
Turn the connection On.
strongSwan CLI steps
This section walks you through the configuration using the strongSwan CLI.
From the VPN client profile configuration files Generic folder, copy or move the VpnServerRoot.cer to /etc/ipsec.d/cacerts.
Copy or move the files you generated to /etc/ipsec.d/certs and /etc/ipsec.d/private/ respectively. These files are the client certificate and the private key, they need to be located in their corresponding directories. Use the following commands:
sudo cp ${USERNAME}Cert.pem /etc/ipsec.d/certs/ sudo cp ${USERNAME}Key.pem /etc/ipsec.d/private/ sudo chmod -R go-rwx /etc/ipsec.d/private /etc/ipsec.d/certsRun the following command to take note of your hostname. You’ll use this value in the next step.
hostnamectl --staticOpen the VpnSettings.xml file and copy the
<VpnServer>value. You’ll use this value in the next step.Adjust the values in the following example, then add the example to the /etc/ipsec.conf configuration.
conn azure keyexchange=ikev2 type=tunnel leftfirewall=yes left=%any # Replace ${USERNAME}Cert.pem with the key filename inside /etc/ipsec.d/certs directory. leftcert=${USERNAME}Cert.pem leftauth=pubkey leftid=%client # use the hostname of your machine with % character prepended. Example: %client right= #Azure VPN gateway address. Example: azuregateway-xxx-xxx.vpn.azure.com rightid=% #Azure VPN gateway FQDN with % character prepended. Example: %azuregateway-xxx-xxx.vpn.azure.com rightsubnet=0.0.0.0/0 leftsourceip=%config auto=add esp=aes256gcm16Add the secret values to /etc/ipsec.secrets.
The name of the PEM file must match what you have used earlier as your client key file.
: RSA ${USERNAME}Key.pem # Replace ${USERNAME}Key.pem with the key filename inside /etc/ipsec.d/private directory.Finally run the following commands:
sudo ipsec restart sudo ipsec up azure
OpenVPN steps
This section helps you configure Linux clients for certificate authentication that uses the OpenVPN tunnel type. To connect to Azure, download the OpenVPN client and configure the connection profile.
Note
OpenVPN Client version 2.6 is not yet supported.
Open a new Terminal session. You can open a new session by pressing 'Ctrl + Alt + t' at the same time.
Enter the following command to install needed components:
sudo apt-get install openvpn sudo apt-get -y install network-manager-openvpn sudo service network-manager restartNext, go to the VPN client profile folder and unzip to view the files.
Export the P2S client certificate you created and uploaded to your P2S configuration on the gateway. For steps, see VPN Gateway point-to-site.
Extract the private key and the base64 thumbprint from the .pfx. There are multiple ways to do this. Using OpenSSL on your computer is one way.
openssl pkcs12 -in "filename.pfx" -nodes -out "profileinfo.txt"The profileinfo.txt file will contain the private key and the thumbprint for the CA, and the Client certificate. Be sure to use the thumbprint of the client certificate.
Open profileinfo.txt in a text editor. To get the thumbprint of the client (child) certificate, select the text including and between "-----BEGIN CERTIFICATE-----" and "-----END CERTIFICATE-----" for the child certificate and copy it. You can identify the child certificate by looking at the subject=/ line.
Open the vpnconfig.ovpn file and find the section shown below. Replace everything between "cert" and "/cert".
# P2S client certificate # please fill this field with a PEM formatted cert <cert> $CLIENTCERTIFICATE </cert>Open the profileinfo.txt in a text editor. To get the private key, select the text including and between "-----BEGIN PRIVATE KEY-----" and "-----END PRIVATE KEY-----" and copy it.
Open the vpnconfig.ovpn file in a text editor and find this section. Paste the private key replacing everything between "key" and "/key".
# P2S client root certificate private key # please fill this field with a PEM formatted key <key> $PRIVATEKEY </key>Don't change any other fields. Use the filled in configuration in client input to connect to the VPN.
To connect using the command line, type the following command:
sudo openvpn --config <name and path of your VPN profile file>&To disconnect using command line, type the following command:
sudo pkill openvpnTo connect using the GUI, go to system settings.
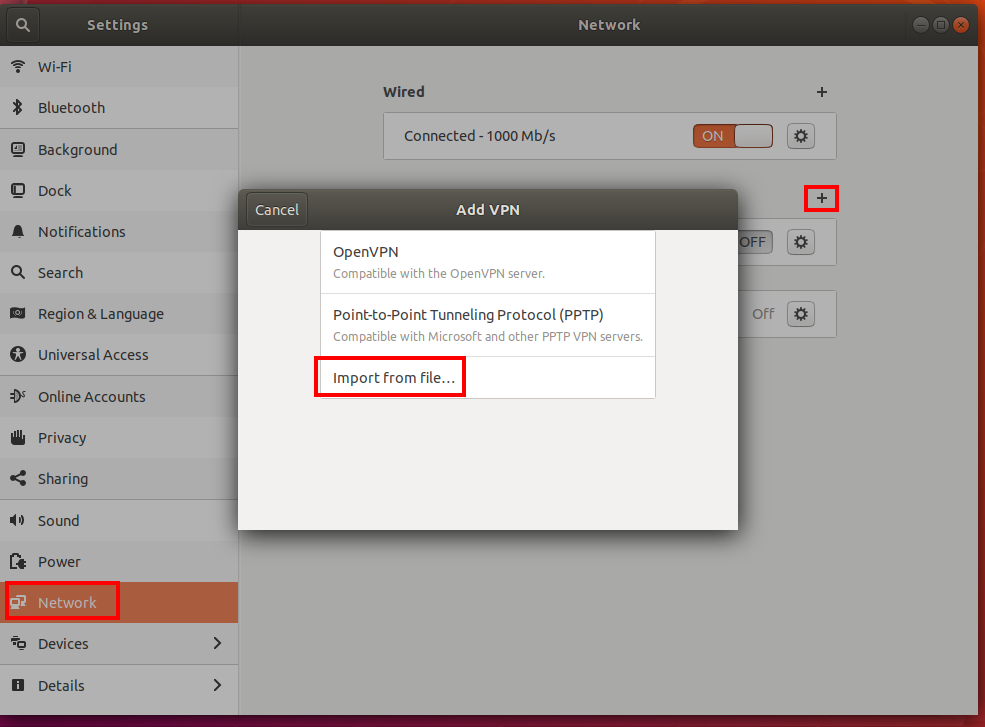
Select + to add a new VPN connection.
Under Add VPN, pick Import from file….
Browse to the profile file and double-click or pick Open.
Select Add on the Add VPN window.
You can connect by turning the VPN ON on the Network Settings page, or under the network icon in the system tray.
Next steps
For additional steps, return to the original point-to-site article that you were working from.
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for