UPDATE 4/19:
Since a lot of customers are facing this issue, I got the latest update from the product team on this:
- Fix is tentatively expected for mid/late May.
- Blog on Short-term mitigation here: https://devblogs.microsoft.com/devops/service-connection-guidance-for-aks-customers-using-kubernetes-tasks/
Issue:
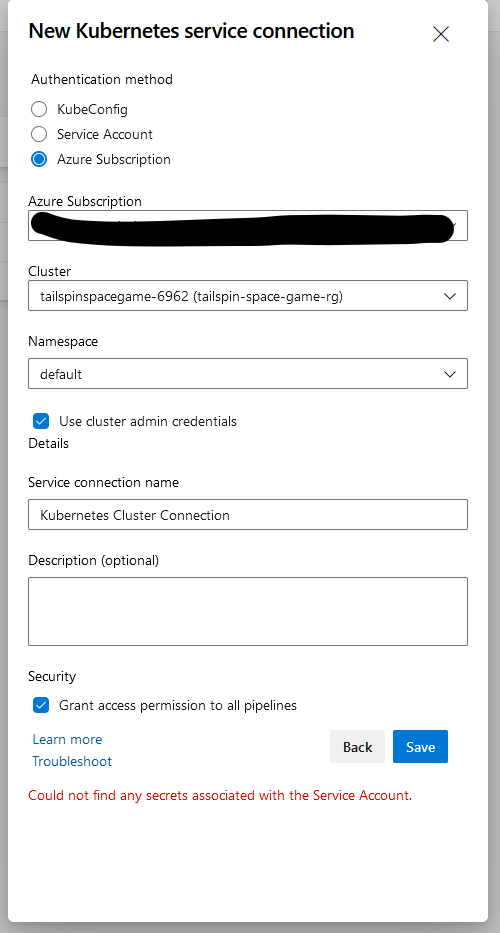
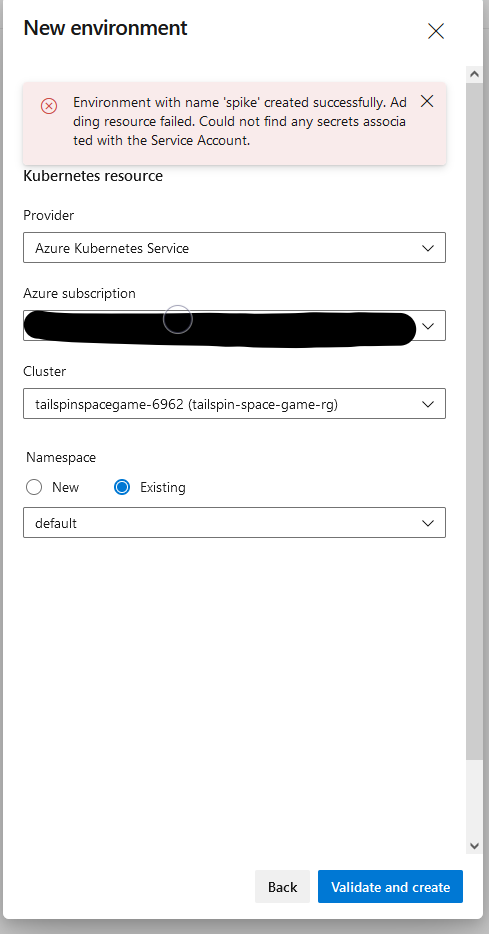
When creating Kubernetes service connection using Azure Subscription as the authentication method, it fails with error: Could not find any secrets associated with the Service Account.
Cause:
Unfortunately, there was a change to the AKS version 1.24.x that no longer automatically generates the associated secret for service account. The change was done on the AKS part, but not on the Azure DevOps side. The product team is currently investigating this issue.
The change log for AKS 1.4.x version says -
The LegacyServiceAccountTokenNoAutoGeneration feature gate is beta, and enabled by default. When enabled, Secret API objects containing service account tokens are no longer auto-generated for every ServiceAccount. Use the TokenRequest API to acquire service account tokens, or if a non-expiring token is required, create a Secret API object for the token controller to populate with a service account token by following this guide.
Work done:
There is an internal work item open with the Product team to resolve this. There is no ETA that can be shared at this point but it is in progress.
Workarounds:
For the time being, the easiest fix is to use one of the other two options to configure the Service Connection, KubeConfig or Service Account. You can find both the options explained step-by-step on this Developer Community ticket: New Kubernetes service connection causes an error Could not find any secrets associated with the Service Account. or you can follow the steps required when you attempt to configure a KubeConfig/Service Account Kubernetes Service Connection as explained in the public documentation here: Service connections in Azure Pipelines - Azure Pipelines | Microsoft Learn.
Downgrading to 1.23. version is another option. However, I highly recommend one of these two options (i.e. KubeConfig or Service Account) for the time being and not being stuck for a longer period. There is no estimated time when the Subscription option will be available again. However, Microsoft is working on fixing the situation as they are currently actively investigating the best option to resolve this.
Additional resources to go through on the same issue:
- https://developercommunity.visualstudio.com/t/New-Kubernetes-service-connection-causes/10138123
- https://developercommunity.visualstudio.com/t/MS-DevOps-Environment--Cannot-Add-Resou/10154315
----------
If this answers your query, do click “Accept the answer” and Up-Vote for the same, which might be beneficial to other community members reading this thread.
And, if you have any further query, do let us know in the comments and I would be happy to investigate further.