Unfortunately, this scenario is not supported. "Valid existing certificate" flag is respected only when requested template and source template (specified in inner certificate to renew) match. In your case template in inner certificate and new template doesn't match. See [MS-WCCE] §3.2.2.6.2.1.4.8, second requirement. There is no way to overcome this using different template and supersedence.
Superseding certificate templates and signatures
Hi everyone.
My goal is to migrate my certificate infrastructure from Legacy CSP to CNG. I've configured new CA and new certificate templates with all the new settings. So far, so good.
What I'm trying to achieve is to seamlessly migrate from old templates to the new ones. I'm making use of the template supersedence feature, and it works fine for the machine certificates. But I'm having trouble with user certificate templates superseding.
We are using smartcards to store user certificates and we do no allow users to request new certificates by themselves, they are only allowed the existing certificates re-enroll. My current user certificate template issuance requirements setup as follows, and I want it to stay intact on the new templates:
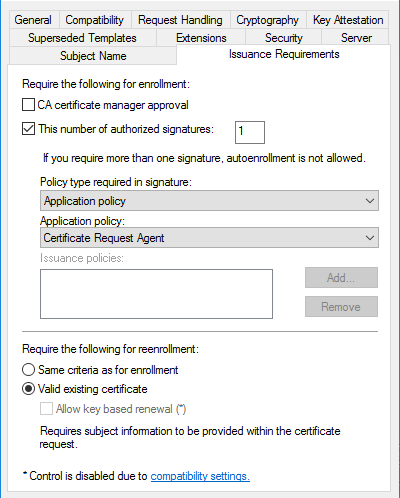
I have set up the new user certificate template with the same issuance requirements and added the old user certificate template name on the "Superseded Templates" tab. Now when the autoenrollment procedure fires, it offers to a client a certificate by the new template, but it still requires CRA signature prior to certificate issuance. It does not recognize existing valid certificate issued by the old superseded template as a valid mean for reenrollment. That means that every smartcard user should personally visit IT to enroll the new certificate. It's a hell of a burden both to smartcard users and to the IT support staff.
I was unable to find anywhere on the Internet the answer to this issue. Am I doing something wrong, or is this the expected behavior? Does the supersedence feature intended to work seamlessly only on the templates without any issuance requirements (no manager approval, no signatures)?
Thanks everyone for the input.
