
did you solve power problem? I meet the same problem. how do you solve it? thanks .my QQ is 1049568282.
This browser is no longer supported.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support.
Hello,
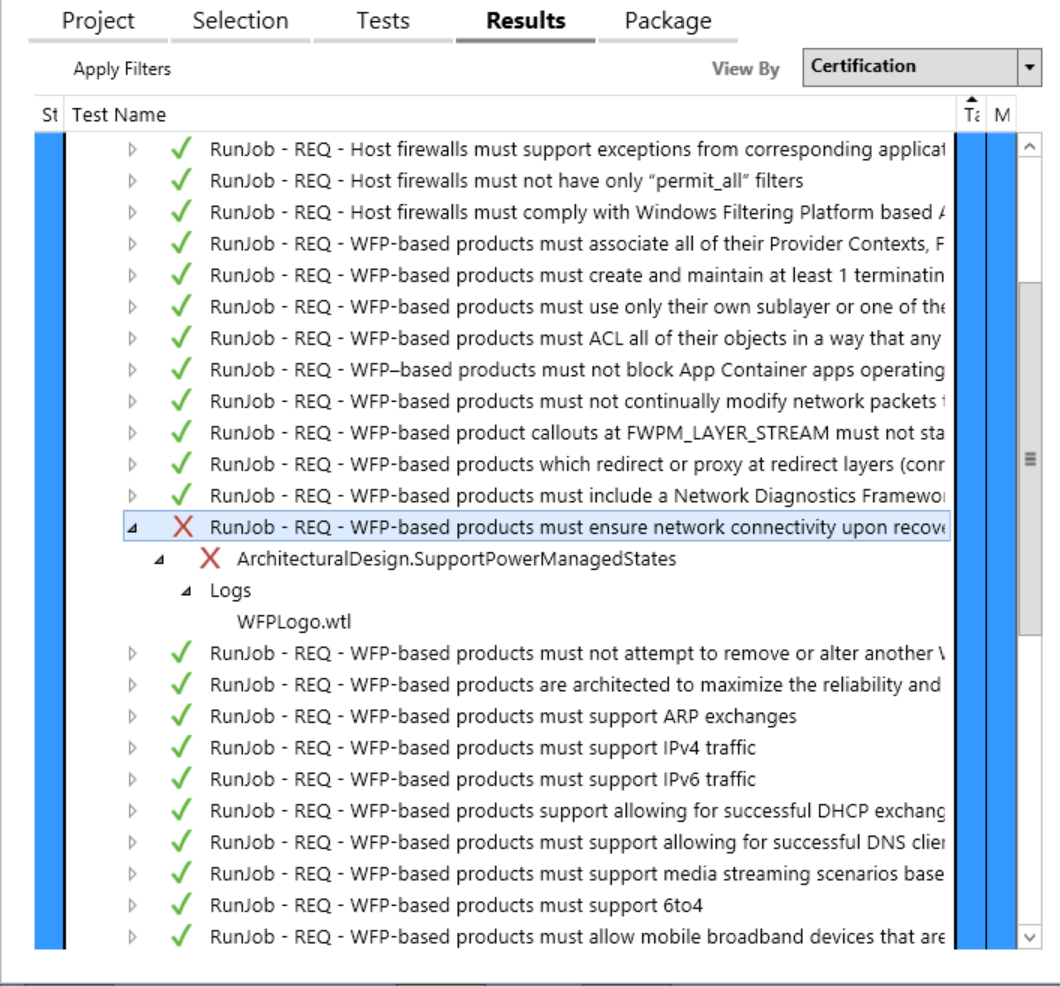
We have a callout driver. We were able to run the HLK tests successfully on Windows 10 and Windows 11. But when we run HCK test on Windows 8.1 & 7 client, in "WindowsFilteringPlatform_Tests > REQ - WFP-based products must ensure network connectivity upon recovering from power managed states -> SupportPowerManagedStates" test, many tests failed with "HlprNSIGetInterfaceProfile: NsiGetAllParametersEx() [status: 0x103]" with a few successes in between.
The relevant info is listed below:
==============================================
Context Index: 384048256
Current: WTTLOG
Parent: ROOT
[Enable Driver Verifier: TRUE]
[Use Answer File: TRUE]
[Has a callout driver: TRUE]
[Is a firewall: FALSE]
[Layered on Microsoft Windows Firewall: FALSE]
[Does MAC Filtering: FALSE]
[Does Virtual Switch Filtering: FALSE]
[Does Packet Injection: TRUE]
[Does Stream Injection: FALSE]
[Does Proxying: TRUE]
[Supports Modern Applications: TRUE]
[Uninstalls cleanly: TRUE]
[Proxies without deadlocking: TRUE]
[Has an identifying Provider: TRUE]
[Associates Provider with all objects: TRUE]
[Has at least 1 filter: TRUE]
[Uses only built-in or their own private SubLayer: TRUE]
[Has an NDF Helper Class: TRUE]
[Does not AV: TRUE]
[Does not alter other's WFP Objects: TRUE]
[Injects without deadlocking: TRUE]
[Injects at STREAM without starvation: TRUE]
[Supports Power Managed States: TRUE]
[ACLs objects so other's can enum them: TRUE]
[Uses latest WinSock specifications: TRUE]
[Properly disabled Windows Firewall: TRUE]
[Uses granular filtering: TRUE]
[Can filter by 5 tuples: TRUE]
[Can filter by application name: TRUE]
[Can filter by Physical Addresses: TRUE]
[Uses WFP for filtering and packet maniplulation: TRUE]
[Supports IPv4 Address Resolution - ARP: TRUE]
[Supports IPv6 Address Resolution - Neighbor Discovery: TRUE]
[Supports Dynamic IP Addressing: TRUE]
[Supports IPv4: TRUE]
[Supports IPv6: TRUE]
[Supports Name Resolution: TRUE]
[Supports 6TO4: TRUE]
[Supports Automatic Updates: TRUE]
[Supports Basic Website Browsing: TRUE]
[Supports File and Printer Sharing: TRUE]
[Supports ICMP Error Messages: TRUE]
[Supports Internet Streaming: TRUE]
[Supports Media Extender Streaming: TRUE]
[Supports MobileBroadband: TRUE]
[Supports Peer Name Resolution Protocol: TRUE]
[Supports Remote Assistance: TRUE]
[Supports Remote Desktop: TRUE]
[Supports Teredo: TRUE]
[Supports Virtual Private Networking: TRUE]
[Interops with other Virtual Switch Extensions: TRUE]
[Does not modify at Egress: TRUE]
[Supports Live Migration: TRUE]
[Supports Removal of Virtual Switch Extensions: TRUE]
[Supports Reordering of Virtual Switch Extension: TRUE]
[Performed interop testing with the WFPSampler TRUE]
Message 10/12/2022 2:50:54.461 PM [Configuration Timer: 15 seconds]
[Number of Packet Injection Commands: 0]
Runtime 10/12/2022 2:50:55.180 PM _
Runtime Index: 2546921180
Machine: ADMIN
Process Name: C:\Windows\System32\WFPLogo.Exe
Process ID: 4120
Thread ID: 4752
Message 10/12/2022 2:50:56.180 PM
Context _ _
Context Index: 1944523683
Current: ArchitecturalDesign\SupportPowerManagedStates
Parent: WTTLOG
Start Test 10/12/2022 2:50:57.180 PM ArchitecturalDesign\SupportPowerManagedStates
Message 10/12/2022 2:50:57.180 PM Priority: 0, Owner: WFP@Microsoft.com
Message 10/12/2022 2:50:59.180 PM Script Run: cmd.exe /C " %WinDir%\System32\NetSh.exe AdvFirewall Firewall Add Rule Name="WFPLogo" Description="Permit Outbound IPv4 with Power States" Dir=Out Action=allow Program=%WinDir%\System32\WFPLogo.Exe LocalIP=1.0.0.1 RemoteIP=1.0.0.254 Protocol=6 Enable=Yes Profile=Any"
Message 10/12/2022 2:51:14.180 PM +VAR+INFO+ 0 : [IPVersion: IPv4][Direction: Outbound][Protocol: TCP (6)][Source / Local Address: 1.0.0.1][Destination / Remote Address: 1.0.0.254][Source / Local Port: 42396][Destination / Remote Port: 48561][Action: PERMIT]
Message 10/12/2022 2:52:49.180 PM LocalTCP::SocketBind : bind() [Local Bound Address: 1.0.0.1][Local Bound Port: 0xa59c] [status: 0]
Runtime 10/12/2022 2:52:45.250 PM _
Runtime Index: 3287206800
Machine: ADMIN
Process Name: C:\Windows\System32\WFPLogo.Exe
Process ID: 4120
Thread ID: 4140
Message 10/12/2022 2:54:40.250 PM VirtualTCP::AnalyzePacket() [IP Version: 0x4][IP Protocol: 0x6][Source Address: 0x1000001][DestinationAddress: 0x10000fe][Source Port: 0xa59c][Destination Port:0xbdb1]
Message 10/12/2022 2:52:50.180 PM LocalTCP::SocketConnect : connect() [status: 0]
Message 10/12/2022 2:54:40.250 PM VirtualTCP::RxPackets() : Exit
Message 10/12/2022 2:52:50.180 PM LocalTCP::SocketSend : send() [bytes sent: 1000] [status: 0]
Runtime 10/12/2022 2:52:45.656 PM _
Runtime Index: 4000363241
Machine: ADMIN
Process Name: C:\Windows\System32\WFPLogo.Exe
Process ID: 4120
Thread ID: 3660
Message 10/12/2022 2:54:41.656 PM VirtualTCP::AnalyzePacket() [IP Version: 0x4][IP Protocol: 0x6][Source Address: 0x1000001][DestinationAddress: 0x10000fe][Source Port: 0xa59c][Destination Port:0xbdb1]
Message 10/12/2022 2:54:41.656 PM VirtualTCP::RxPackets() : Exit
Message 10/12/2022 2:52:51.180 PM LocalTCP::SocketSend : send() [status: 0]
Message 10/12/2022 2:52:51.180 PM AnalyzeTrafficResults() [Analysis: Permitted][local Error: 0][peer Error: 0][packet(s) Rx'd: Yes][packet(s) Tx'd: Yes]
Message 10/12/2022 2:52:51.180 PM LocalTCP::SocketSetOptions() [Option Level: 0xffff][Option Name: 0xffffff7f][Option Length: 0x4]
Message 10/12/2022 2:52:51.180 PM LocalTCP::SocketShutdown : shutdown() [status: 0]
Runtime 10/12/2022 2:52:46.203 PM _
Runtime Index: 577400067
Machine: ADMIN
Process Name: C:\Windows\System32\WFPLogo.Exe
Process ID: 4120
Thread ID: 1768
Message 10/12/2022 2:54:42.203 PM VirtualTCP::AnalyzePacket() [IP Version: 0x4][IP Protocol: 0x6][Source Address: 0x1000001][DestinationAddress: 0x10000fe][Source Port: 0xa59c][Destination Port:0xbdb1]
Message 10/12/2022 2:54:42.203 PM VirtualTCP::RxPackets() : Exit
Message 10/12/2022 2:52:51.180 PM LocalTCP::SocketSetOptions() [Option Level: 0xffff][Option Name: 0x80][Option Length: 0x4]
Message 10/12/2022 2:52:51.180 PM LocalTCP::SocketClose : closesocket() [status: 0]
Runtime 10/12/2022 2:53:12.085 PM _
Runtime Index: 1513411261
Machine: ADMIN
Process Name: C:\Windows\System32\WFPLogo.Exe
Process ID: 4120
Thread ID: 3624
Context _ _
Context Index: 4136458679
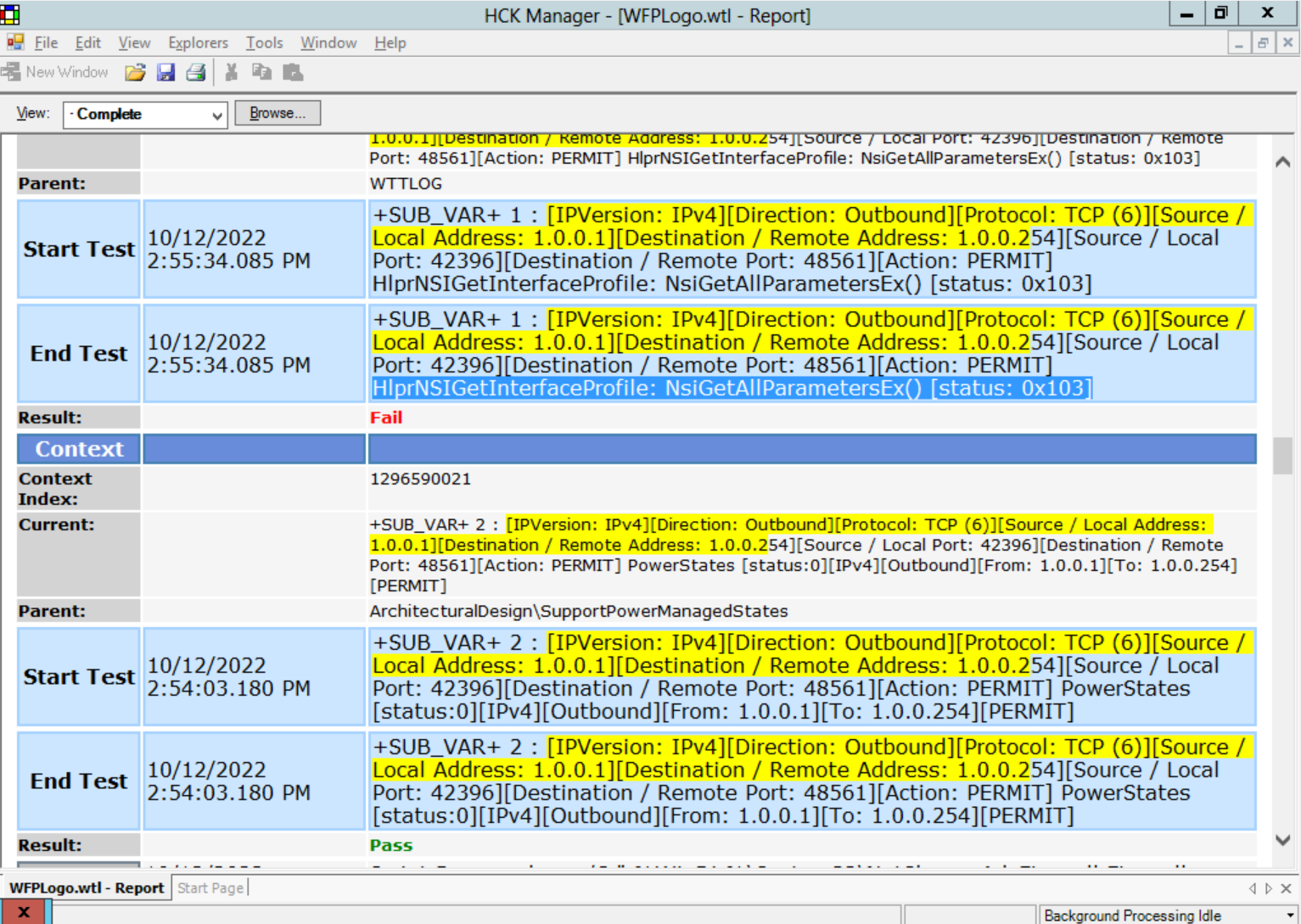
Current: +SUB_VAR+ 1 : [IPVersion: IPv4][Direction: Outbound][Protocol: TCP (6)][Source / Local Address: 1.0.0.1][Destination / Remote Address: 1.0.0.254][Source / Local Port: 42396][Destination / Remote Port: 48561][Action: PERMIT] HlprNSIGetInterfaceProfile: NsiGetAllParametersEx() [status: 0x103]
Parent: WTTLOG
Start Test 10/12/2022 2:55:34.085 PM +SUB_VAR+ 1 : [IPVersion: IPv4][Direction: Outbound][Protocol: TCP (6)][Source / Local Address: 1.0.0.1][Destination / Remote Address: 1.0.0.254][Source / Local Port: 42396][Destination / Remote Port: 48561][Action: PERMIT] HlprNSIGetInterfaceProfile: NsiGetAllParametersEx() [status: 0x103]
End Test 10/12/2022 2:55:34.085 PM +SUB_VAR+ 1 : [IPVersion: IPv4][Direction: Outbound][Protocol: TCP (6)][Source / Local Address: 1.0.0.1][Destination / Remote Address: 1.0.0.254][Source / Local Port: 42396][Destination / Remote Port: 48561][Action: PERMIT] HlprNSIGetInterfaceProfile: NsiGetAllParametersEx() [status: 0x103]
Result: Fail
Context _ _
Context Index: 1296590021
Current: +SUB_VAR+ 2 : [IPVersion: IPv4][Direction: Outbound][Protocol: TCP (6)][Source / Local Address: 1.0.0.1][Destination / Remote Address: 1.0.0.254][Source / Local Port: 42396][Destination / Remote Port: 48561][Action: PERMIT] PowerStates [status:0][IPv4][Outbound][From: 1.0.0.1][To: 1.0.0.254][PERMIT]
Parent: ArchitecturalDesign\SupportPowerManagedStates
Start Test 10/12/2022 2:54:03.180 PM +SUB_VAR+ 2 : [IPVersion: IPv4][Direction: Outbound][Protocol: TCP (6)][Source / Local Address: 1.0.0.1][Destination / Remote Address: 1.0.0.254][Source / Local Port: 42396][Destination / Remote Port: 48561][Action: PERMIT] PowerStates [status:0][IPv4][Outbound][From: 1.0.0.1][To: 1.0.0.254][PERMIT]
End Test 10/12/2022 2:54:03.180 PM +SUB_VAR+ 2 : [IPVersion: IPv4][Direction: Outbound][Protocol: TCP (6)][Source / Local Address: 1.0.0.1][Destination / Remote Address: 1.0.0.254][Source / Local Port: 42396][Destination / Remote Port: 48561][Action: PERMIT] PowerStates [status:0][IPv4][Outbound][From: 1.0.0.1][To: 1.0.0.254][PERMIT]
Result: Pass
Message 10/12/2022 2:54:05.180 PM Script Run: cmd.exe /C " %WinDir%\System32\NetSh.exe AdvFirewall Firewall Delete Rule Name="WFPLogo" Dir=Out Program=%WinDir%\System32\WFPLogo.Exe LocalIP=1.0.0.1 RemoteIP=1.0.0.254 Protocol=6 Profile=Any"
Message 10/12/2022 2:54:21.180 PM Script Run: cmd.exe /C " %WinDir%\System32\NetSh.exe AdvFirewall Firewall Add Rule Name="WFPLogo" Description="Permit Inbound IPv4 with Power States" Dir=In Action=allow Program=%WinDir%\System32\WFPLogo.Exe LocalIP=1.0.0.1 RemoteIP=1.0.0.254 Protocol=17 Enable=Yes Profile=Any"
Message 10/12/2022 2:54:36.180 PM +VAR+INFO+ 1 : [IPVersion: IPv4][Direction: Inbound][Protocol: Raw UDP (17)][Source / Remote Address: 1.0.0.254][Destination / Local Address: 1.0.0.1][Source / Remote Port: 42818][Destination / Local Port: 45141][Action: PERMIT]
Message 10/12/2022 2:56:34.180 PM LocalRawUDP::SocketBind : bind() [Local Bound Address: 1.0.0.1][Local Bound Port: 0xb055] [status: 0]
Message 10/12/2022 2:56:35.180 PM LocalRawUDP::SocketSetToNonBlocking : ioctlsocket() [status: 0]
Message 10/12/2022 2:56:35.180 PM [IPv4][ipProtocol: 17][ipHeaderLength: 20][totalLength: 1028][sourceAddress: 0x10000fe][destinationAddress: 0x1000001]
Message 10/12/2022 2:56:35.180 PM [sourcePort: 0xa742][destinationPort: 0xb055]
Message 10/12/2022 2:56:35.180 PM IsExpectedDataBuffer() [pBuffer: 0X00000041EF167BF0][size: 1028][isExpected: TRUE]
Message 10/12/2022 2:56:36.180 PM LocalRawUDP::SocketRecv : recv() [bytes received: 1028] [status: 0]
Message 10/12/2022 2:56:36.180 PM LocalRawUDP::SocketSetToNonBlocking : ioctlsocket() [status: 0]
Message 10/12/2022 2:56:36.180 PM AnalyzeTrafficResults() [Analysis: Permitted][local Error: 0][peer Error: 0][packet(s) Rx'd: Yes][packet(s) Tx'd: Yes]
Message 10/12/2022 2:56:36.180 PM LocalRawUDP::SocketClose : closesocket() [status: 0]
Context _ _
Context Index: 2630202630
Current: +SUB_VAR+ 1 : [IPVersion: IPv4][Direction: Inbound][Protocol: Raw UDP (17)][Source / Remote Address: 1.0.0.254][Destination / Local Address: 1.0.0.1][Source / Remote Port: 42818][Destination / Local Port: 45141][Action: PERMIT] HlprNSIGetInterfaceProfile: NsiGetAllParametersEx() [status: 0x103]
Parent: WTTLOG
Start Test 10/12/2022 2:59:15.085 PM +SUB_VAR+ 1 : [IPVersion: IPv4][Direction: Inbound][Protocol: Raw UDP (17)][Source / Remote Address: 1.0.0.254][Destination / Local Address: 1.0.0.1][Source / Remote Port: 42818][Destination / Local Port: 45141][Action: PERMIT] HlprNSIGetInterfaceProfile: NsiGetAllParametersEx() [status: 0x103]
End Test 10/12/2022 2:59:15.085 PM +SUB_VAR+ 1 : [IPVersion: IPv4][Direction: Inbound][Protocol: Raw UDP (17)][Source / Remote Address: 1.0.0.254][Destination / Local Address: 1.0.0.1][Source / Remote Port: 42818][Destination / Local Port: 45141][Action: PERMIT] HlprNSIGetInterfaceProfile: NsiGetAllParametersEx() [status: 0x103]
Result: Fail
Context _ _
Context Index: 2825241481
Current: +SUB_VAR+ 2 : [IPVersion: IPv4][Direction: Inbound][Protocol: Raw UDP (17)][Source / Remote Address: 1.0.0.254][Destination / Local Address: 1.0.0.1][Source / Remote Port: 42818][Destination / Local Port: 45141][Action: PERMIT] PowerStates [status:0][IPv4][Inbound][From: 1.0.0.254][To: 1.0.0.1][PERMIT]
Parent: ArchitecturalDesign\SupportPowerManagedStates
Start Test 10/12/2022 2:57:58.180 PM +SUB_VAR+ 2 : [IPVersion: IPv4][Direction: Inbound][Protocol: Raw UDP (17)][Source / Remote Address: 1.0.0.254][Destination / Local Address: 1.0.0.1][Source / Remote Port: 42818][Destination / Local Port: 45141][Action: PERMIT] PowerStates [status:0][IPv4][Inbound][From: 1.0.0.254][To: 1.0.0.1][PERMIT]
End Test 10/12/2022 2:57:58.180 PM +SUB_VAR+ 2 : [IPVersion: IPv4][Direction: Inbound][Protocol: Raw UDP (17)][Source / Remote Address: 1.0.0.254][Destination / Local Address: 1.0.0.1][Source / Remote Port: 42818][Destination / Local Port: 45141][Action: PERMIT] PowerStates [status:0][IPv4][Inbound][From: 1.0.0.254][To: 1.0.0.1][PERMIT]
Result: Pass
Message 10/12/2022 2:57:59.180 PM Script Run: cmd.exe /C " %WinDir%\System32\NetSh.exe AdvFirewall Firewall Delete Rule Name="WFPLogo" Dir=In Program=%WinDir%\System32\WFPLogo.Exe LocalIP=1.0.0.1 RemoteIP=1.0.0.254 Protocol=17 Profile=Any"
Message 10/12/2022 2:58:15.180 PM Script Run: cmd.exe /C " %WinDir%\System32\NetSh.exe AdvFirewall Firewall Add Rule Name="WFPLogo" Description="Permit Outbound IPv6 with Power States" Dir=Out Action=allow Program=%WinDir%\System32\WFPLogo.Exe LocalIP=fe80::6010:68f4:c68a:795c RemoteIP=fe80::1:0:0:FE Protocol=17 Enable=Yes Profile=Any"
Message 10/12/2022 2:58:30.180 PM +VAR+INFO+ 2 : [IPVersion: IPv6][Direction: Outbound][Protocol: UDP (17)][Source / Local Address: fe80::6010:68f4:c68a:795c][Destination / Remote Address: fe80::1:0:0:FE][Source / Local Port: 43363][Destination / Remote Port: 48605][Action: PERMIT]
Message 10/12/2022 3:00:07.180 PM LocalUDP::SocketBind : bind() [Local Bound Address: fe80::6010:68f4:c68a:795c][Local Bound Port: 0xa963] [status: 0]
Message 10/12/2022 3:00:07.180 PM LocalUDP::SocketSendTo : sendto() [bytes sent: 1000] [status: 0]
Runtime 10/12/2022 2:59:54.077 PM _
Runtime Index: 148845850
Machine: ADMIN
Process Name: C:\Windows\System32\WFPLogo.Exe
Process ID: 4120
Thread ID: 2452
Message 10/12/2022 3:09:06.077 PM VirtualUDP::AnalyzePacket() [IP Version: 0x6][IP Protocol: 0x11][Source Address: fe80::6010:68f4:c68a:795c][DestinationAddress: fe80::1:0:0:fe][Source Port: 0xa963][Destination Port: 0xbddd]
Message 10/12/2022 3:09:06.077 PM VirtualUDP::RxPackets() : Exit
Message 10/12/2022 3:00:08.180 PM LocalUDP::SocketSendTo : sendto() [bytes sent: 1000] [status: 0]
Runtime 10/12/2022 2:59:54.484 PM _
Runtime Index: 2423474273
Machine: ADMIN
Process Name: C:\Windows\System32\WFPLogo.Exe
Process ID: 4120
Thread ID: 4668
Message 10/12/2022 3:09:07.484 PM VirtualUDP::AnalyzePacket() [IP Version: 0x6][IP Protocol: 0x11][Source Address: fe80::6010:68f4:c68a:795c][DestinationAddress: fe80::1:0:0:fe][Source Port: 0xa963][Destination Port: 0xbddd]
Message 10/12/2022 3:09:07.484 PM VirtualUDP::RxPackets() : Exit
Message 10/12/2022 3:00:08.180 PM AnalyzeTrafficResults() [Analysis: Permitted][local Error: 0][peer Error: 0][packet(s) Rx'd: Yes][packet(s) Tx'd: Yes]
Message 10/12/2022 3:00:08.180 PM LocalUDP::SocketShutdown : shutdown() [status: 0]
Message 10/12/2022 3:00:08.180 PM LocalUDP::SocketClose : closesocket() [status: 0]
Context _ _
Context Index: 3646449111
Current: +SUB_VAR+ 1 : [IPVersion: IPv6][Direction: Outbound][Protocol: UDP (17)][Source / Local Address: fe80::6010:68f4:c68a:795c][Destination / Remote Address: fe80::1:0:0:FE][Source / Local Port: 43363][Destination / Remote Port: 48605][Action: PERMIT] PowerStates [status:0][IPv6][Outbound][From: fe80::6010:68f4:c68a:795c][To: fe80::1:0:0:FE][PERMIT]
Parent: ArchitecturalDesign\SupportPowerManagedStates
Start Test 10/12/2022 3:01:28.180 PM +SUB_VAR+ 1 : [IPVersion: IPv6][Direction: Outbound][Protocol: UDP (17)][Source / Local Address: fe80::6010:68f4:c68a:795c][Destination / Remote Address: fe80::1:0:0:FE][Source / Local Port: 43363][Destination / Remote Port: 48605][Action: PERMIT] PowerStates [status:0][IPv6][Outbound][From: fe80::6010:68f4:c68a:795c][To: fe80::1:0:0:FE][PERMIT]
End Test 10/12/2022 3:01:28.180 PM +SUB_VAR+ 1 : [IPVersion: IPv6][Direction: Outbound][Protocol: UDP (17)][Source / Local Address: fe80::6010:68f4:c68a:795c][Destination / Remote Address: fe80::1:0:0:FE][Source / Local Port: 43363][Destination / Remote Port: 48605][Action: PERMIT] PowerStates [status:0][IPv6][Outbound][From: fe80::6010:68f4:c68a:795c][To: fe80::1:0:0:FE][PERMIT]
Result: Pass
Message 10/12/2022 3:01:29.180 PM Script Run: cmd.exe /C " %WinDir%\System32\NetSh.exe AdvFirewall Firewall Delete Rule Name="WFPLogo" Dir=Out Program=%WinDir%\System32\WFPLogo.Exe LocalIP=fe80::6010:68f4:c68a:795c RemoteIP=fe80::1:0:0:FE Protocol=17 Profile=Any"
Message 10/12/2022 3:01:45.180 PM Script Run: cmd.exe /C " %WinDir%\System32\NetSh.exe AdvFirewall Firewall Add Rule Name="WFPLogo" Description="Permit Inbound IPv6 with Power States" Dir=In Action=allow Program=%WinDir%\System32\WFPLogo.Exe LocalIP=fe80::6010:68f4:c68a:795c RemoteIP=fe80::1:0:0:FE Protocol=6 Enable=Yes Profile=Any"
Message 10/12/2022 3:02:00.180 PM +VAR+INFO+ 3 : [IPVersion: IPv6][Direction: Inbound][Protocol: TCP (6)][Source / Remote Address: fe80::1:0:0:FE][Destination / Local Address: fe80::6010:68f4:c68a:795c][Source / Remote Port: 44227][Destination / Local Port: 48272][Action: PERMIT]
Context _ _
Context Index: 208905465
Current: +SUB_VAR+ 1 : [IPVersion: IPv6][Direction: Inbound][Protocol: TCP (6)][Source / Remote Address: fe80::1:0:0:FE][Destination / Local Address: fe80::6010:68f4:c68a:795c][Source / Remote Port: 44227][Destination / Local Port: 48272][Action: PERMIT] HlprNSIGetInterfaceProfile: NsiGetAllParametersEx() [status: 0x103]
Parent: WTTLOG
Start Test 10/12/2022 3:04:26.085 PM +SUB_VAR+ 1 : [IPVersion: IPv6][Direction: Inbound][Protocol: TCP (6)][Source / Remote Address: fe80::1:0:0:FE][Destination / Local Address: fe80::6010:68f4:c68a:795c][Source / Remote Port: 44227][Destination / Local Port: 48272][Action: PERMIT] HlprNSIGetInterfaceProfile: NsiGetAllParametersEx() [status: 0x103]
End Test 10/12/2022 3:04:26.085 PM +SUB_VAR+ 1 : [IPVersion: IPv6][Direction: Inbound][Protocol: TCP (6)][Source / Remote Address: fe80::1:0:0:FE][Destination / Local Address: fe80::6010:68f4:c68a:795c][Source / Remote Port: 44227][Destination / Local Port: 48272][Action: PERMIT] HlprNSIGetInterfaceProfile: NsiGetAllParametersEx() [status: 0x103]
Result: Fail
Message 10/12/2022 3:03:38.180 PM LocalTCP::SocketBind : bind() [Local Bound Address: fe80::6010:68f4:c68a:795c][Local Bound Port: 0xbc90] [status: 0]
Message 10/12/2022 3:03:38.180 PM LocalTCP::SocketListen : listen() [status: 0]
Message 10/12/2022 3:03:38.180 PM LocalTCP::SocketSetToNonBlocking : ioctlsocket() [status: 0]
Runtime 10/12/2022 3:03:20.766 PM _
Runtime Index: 3303498572
Machine: ADMIN
Process Name: C:\Windows\System32\WFPLogo.Exe
Process ID: 4120
Thread ID: 5164
Message 10/12/2022 3:16:03.766 PM VirtualTCP::AnalyzePacket() [IP Version: 0x6][IP Protocol: 0x6][Source Address: fe80::6010:68f4:c68a:795c][DestinationAddress: fe80::1:0:0:fe][Source Port: 0xbc90][Destination Port: 0xacc3]
Message 10/12/2022 3:03:38.180 PM LocalTCP::SocketAccept : accept() [status: 0]
Message 10/12/2022 3:03:38.180 PM LocalTCP::SocketSetToNonBlocking : ioctlsocket() [status: 0x2726]
Message 10/12/2022 3:03:38.180 PM LocalTCP::SocketSetToNonBlocking : ioctlsocket() [status: 0]
Message 10/12/2022 3:03:39.180 PM IsExpectedDataBuffer() [pBuffer: 0X00000041EF17EF60][size: 1000][isExpected: TRUE]
Message 10/12/2022 3:03:40.180 PM LocalTCP::SocketRecv : recv() [bytes received: 1000] [status: 0]
Message 10/12/2022 3:03:40.180 PM LocalTCP::SocketSetToNonBlocking : ioctlsocket() [status: 0x2726]
Message 10/12/2022 3:03:40.180 PM AnalyzeTrafficResults() [Analysis: Permitted][local Error: 0][peer Error: 0][packet(s) Rx'd: Yes][packet(s) Tx'd: Yes]
Message 10/12/2022 3:03:40.180 PM LocalTCP::SocketSetOptions() [Option Level: 0xffff][Option Name: 0xffffff7f][Option Length: 0x4]
Message 10/12/2022 3:03:40.180 PM LocalTCP::SocketShutdown : shutdown() [status: 0]
Runtime 10/12/2022 3:03:22.688 PM _
Runtime Index: 2441991038
Machine: ADMIN
Process Name: C:\Windows\System32\WFPLogo.Exe
Process ID: 4120
Thread ID: 2772
Message 10/12/2022 3:16:07.688 PM VirtualTCP::AnalyzePacket() [IP Version: 0x6][IP Protocol: 0x6][Source Address: fe80::6010:68f4:c68a:795c][DestinationAddress: fe80::1:0:0:fe][Source Port: 0xbc90][Destination Port: 0xacc3]
Message 10/12/2022 3:03:40.180 PM LocalTCP::SocketShutdown : shutdown() [status: 0x2749]
Message 10/12/2022 3:16:07.688 PM VirtualTCP::RxPackets() : Exit
Message 10/12/2022 3:03:40.180 PM LocalTCP::SocketSetOptions() [Option Level: 0xffff][Option Name: 0x80][Option Length: 0x4]
Message 10/12/2022 3:03:40.180 PM LocalTCP::SocketClose : closesocket() [status: 0]
Message 10/12/2022 3:03:40.180 PM LocalTCP::SocketSetOptions() [Option Level: 0xffff][Option Name: 0x80][Option Length: 0x4]
Message 10/12/2022 3:03:41.180 PM LocalTCP::SocketClose : closesocket() [status: 0]
Context _ _
Context Index: 1679150077
Current: +SUB_VAR+ 2 : [IPVersion: IPv6][Direction: Inbound][Protocol: TCP (6)][Source / Remote Address: fe80::1:0:0:FE][Destination / Local Address: fe80::6010:68f4:c68a:795c][Source / Remote Port: 44227][Destination / Local Port: 48272][Action: PERMIT] PowerStates [status:0][IPv6][Inbound][From: fe80::1:0:0:FE][To: fe80::6010:68f4:c68a:795c][PERMIT]
Parent: ArchitecturalDesign\SupportPowerManagedStates
Start Test 10/12/2022 3:04:59.180 PM +SUB_VAR+ 2 : [IPVersion: IPv6][Direction: Inbound][Protocol: TCP (6)][Source / Remote Address: fe80::1:0:0:FE][Destination / Local Address: fe80::6010:68f4:c68a:795c][Source / Remote Port: 44227][Destination / Local Port: 48272][Action: PERMIT] PowerStates [status:0][IPv6][Inbound][From: fe80::1:0:0:FE][To: fe80::6010:68f4:c68a:795c][PERMIT]
End Test 10/12/2022 3:04:59.180 PM +SUB_VAR+ 2 : [IPVersion: IPv6][Direction: Inbound][Protocol: TCP (6)][Source / Remote Address: fe80::1:0:0:FE][Destination / Local Address: fe80::6010:68f4:c68a:795c][Source / Remote Port: 44227][Destination / Local Port: 48272][Action: PERMIT] PowerStates [status:0][IPv6][Inbound][From: fe80::1:0:0:FE][To: fe80::6010:68f4:c68a:795c][PERMIT]
Result: Pass
Message 10/12/2022 3:05:00.180 PM Script Run: cmd.exe /C " %WinDir%\System32\NetSh.exe AdvFirewall Firewall Delete Rule Name="WFPLogo" Dir=In Program=%WinDir%\System32\WFPLogo.Exe LocalIP=fe80::6010:68f4:c68a:795c RemoteIP=fe80::1:0:0:FE Protocol=6 Profile=Any"
End Test 10/12/2022 3:05:15.180 PM ArchitecturalDesign\SupportPowerManagedStates
Result: Fail
Message 10/12/2022 3:05:15.180 PM
==============================================
All the "PowerStates" tests passes but all the "HlprNSIGetInterfaceProfile: NsiGetAllParametersEx() [status: 0x103]" tests fails. Couldn't find any relevant information regarding NsiGetAllParametersEx() that could help.
Here is what we have tried so far:
All the other WFP test cases except for this "SupportPowerManagedStates" were able to pass successfully.
Thanks in advance for your help!
-- Vipul
did you solve power problem? I meet the same problem. how do you solve it? thanks .my QQ is 1049568282.