Gita,
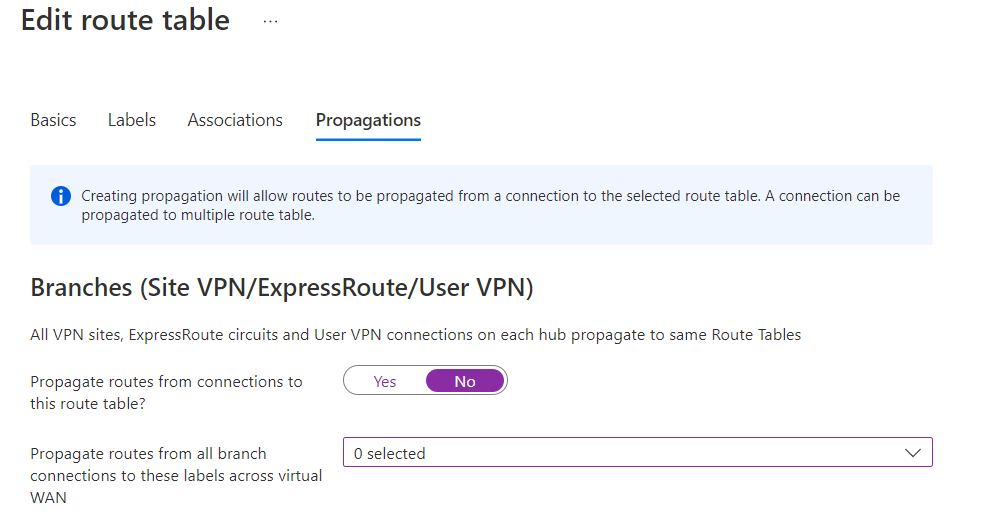
For your first question - propagations - "Propagate routes from connections to this route table" is set to false, and "Propagate routes from all branch connections to these labels across virtual WAN" is set to "Default".
The first one seems obvious - don't propagate from spoke connections to the route table. The second one I read as what the branches alone propagate to - is Default wrong for that?
For the second question, on the Associations tab, "Associate this route table across all connections" is disabled and set to no. The Virtual Networks selection list is set to only the internal VNet connections that participate in this route table. In the summary list below that, each VNet appears associated to the correct route table, but propagating to noneRouteTable.
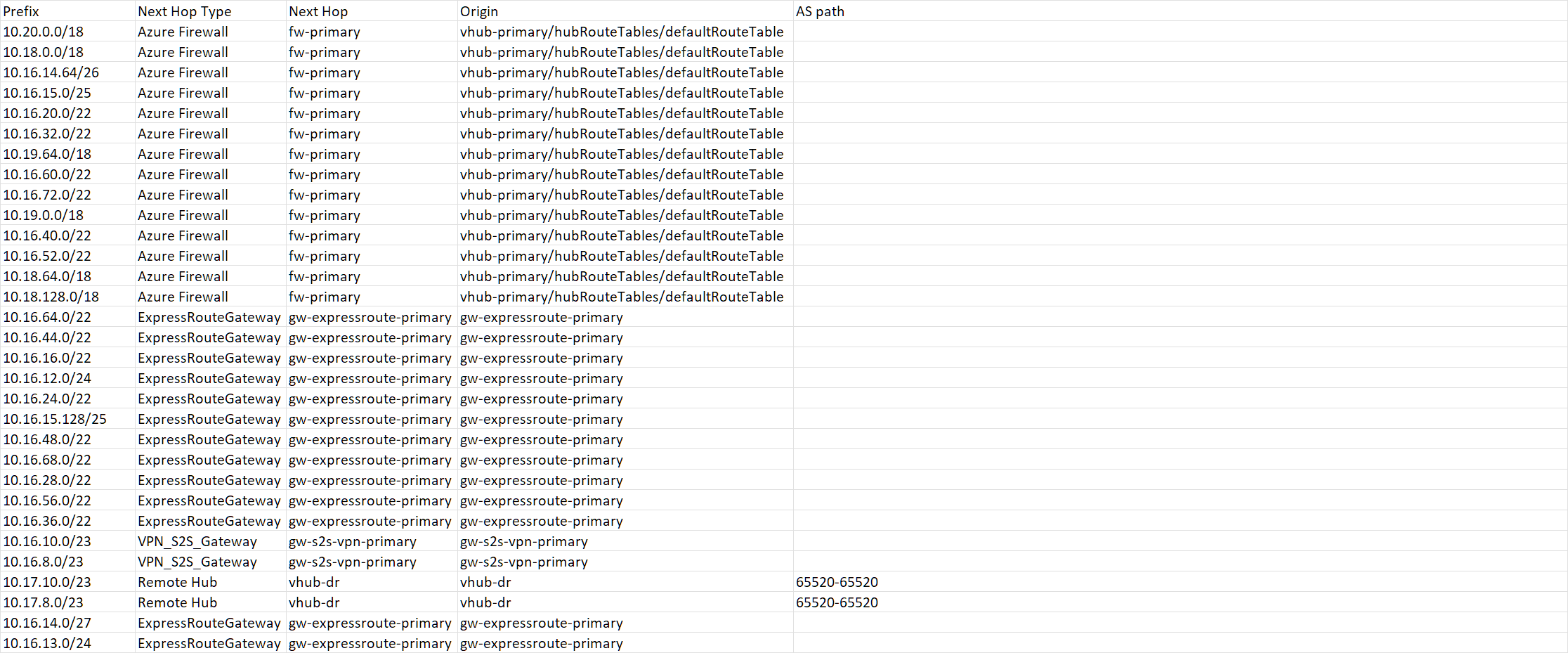
For the last question, I read your intent to mean "add static routes for the VNets that I want my branches to be able to reach" to the Default route table, and I have, with a route through my firewall. Aside from setting those routes, I didn't see anything in that article which mentioned preventing Default from propagating. In any case, it shows that branches are associated with Default and propagating to Default.
The key distinction here is that I'm not listing the address space for ALL of the VNets, I'm listing the address space for only the VNets I want to be contactable. Those appear correctly in the effective routes for the Default route table. It's the networks that I DIDN'T add which are showing up as having a next hop of my ExpressRouteGateway (which would be wrong even if I wanted to advertise a route, which I don't).
If you'd like more detail, I'm absolutely happy to provide it - but would prefer to do so privately, so that I don't need to sanitize a lot of details.
Thanks so much for responding!