@G Cocci Are you still blocked?
I understand that you have enabled the Managed Identity on the IoTHub and assigned to it the "Azure Event Hub Data Sender" role on the Event Hub.
Can you confirm have you assigned System-assigned managed identity or User-assigned managed identity?
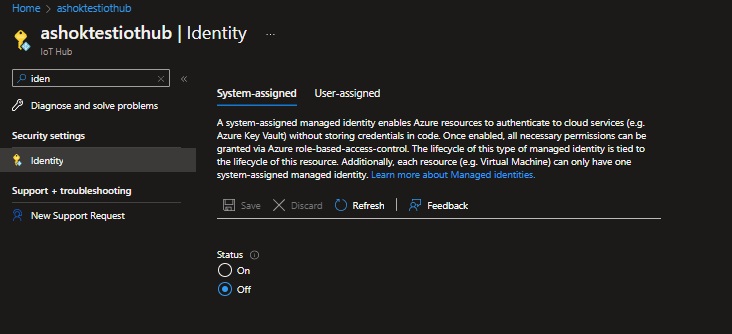
Please note that, Only system-assigned managed identity gives IoT Hub access to private resources. If you want to use user-assigned managed identity, then the public access on those private resources needs to be enabled in order to allow connectivity.
Also, Make sure VNET and IP rules are properly configured.
To allow other services to find your IoT hub as a trusted Microsoft service, your hub must use the managed identity. Once a managed identity is provisioned, you need to grant the Azure RBAC permission to your hub's managed identity to access your custom endpoint. Follow the article Managed identities support in IoT Hub to provision a managed identity with Azure RBAC permission, and add the custom endpoint to your IoT Hub. Make sure you turn on the trusted Microsoft first party exception to allow your IoT Hub's access to the custom endpoint if you have the firewall configurations in place.
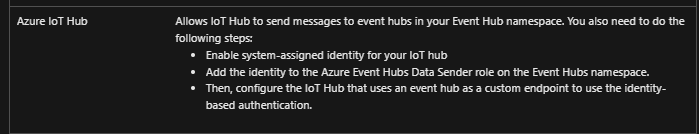
From the doc, you need to do the following steps:
- Enable system-assigned identity for your IoT hub
- Add the identity to the Azure Event Hubs Data Sender role on the Event Hubs namespace.
- Then, configure the IoT Hub that uses an event hub as a custom endpoint to use the identity-based authentication.
Is it possible to do this configuration with both resources with blocked access from public network?
For more details, please refer to IoT Hub support for managed identities and IoT Hub support for virtual networks with Private Link and Managed Identity.
Let us know if it helps to resolve the issue or have any further queries.
If the response is helpful, please click "Accept Answer" and upvote it.
