Hi @Deepaklal-FT ,
Welcome to Microsoft Q&A Platform. Thank you for reaching out & hope you are doing well.
I understand that you would like to know how to block IP address(Client IP) in Azure Application gateway (WAF V2).
The Azure Application Gateway Web Application Firewall (WAF) v2 can be associated to a WAF policy which contain all the WAF settings and configurations. This includes exclusions, custom rules, managed rules, and so on. Custom rules allow you to create your own rules that are evaluated for each request that passes through the WAF.
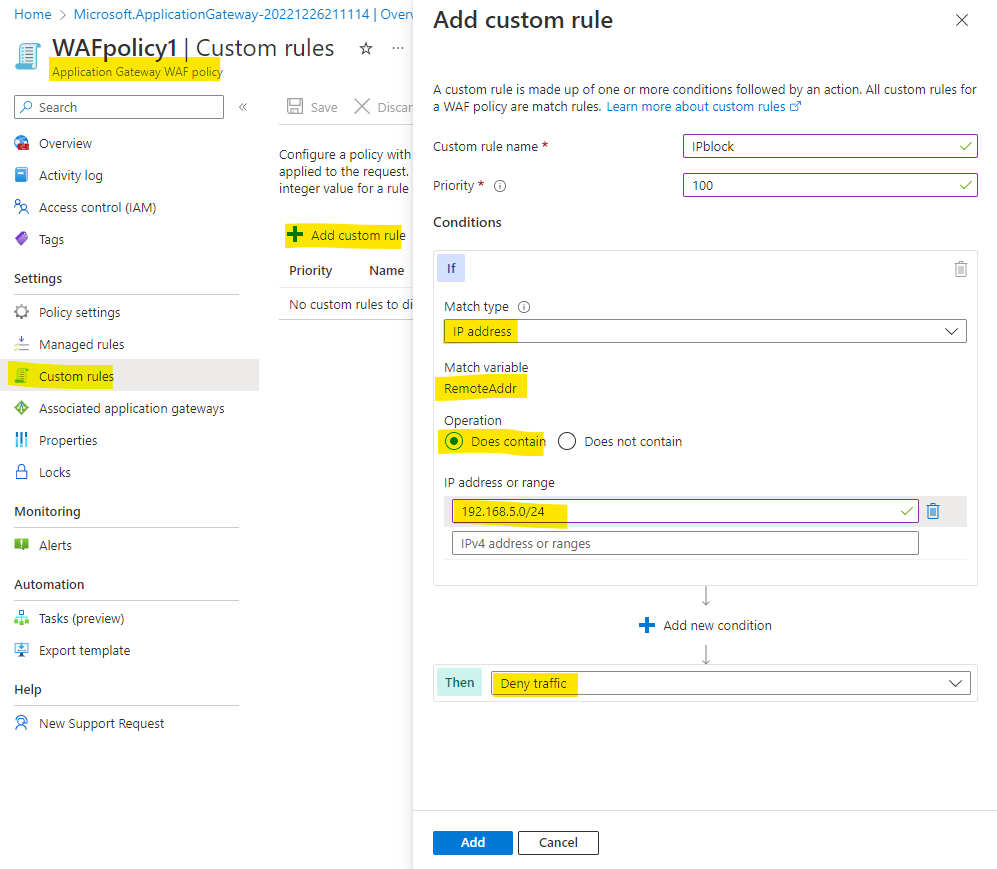
So, you can create a Custom rule on Azure Application Gateway WAF v2 to block all requests from an IP address/range.
You can use the "RemoteAddr" variable which is the IPv4 Address/Range of the remote computer connection with operator IPMatch to create such a rule and block all requests from a particular IP address and range.
Example reference : https://learn.microsoft.com/en-us/azure/web-application-firewall/ag/create-custom-waf-rules#example-3
NOTE : The example provided is in Azure PowerShell but the same can be achieved via Azure Portal (see screenshot below).
To create custom rules, you first need to create a Web Application Firewall policy for Application Gateway.
Refer : https://learn.microsoft.com/en-us/azure/web-application-firewall/ag/create-waf-policy-ag
Once the WAF policy is created, you can create a custom rule as below:
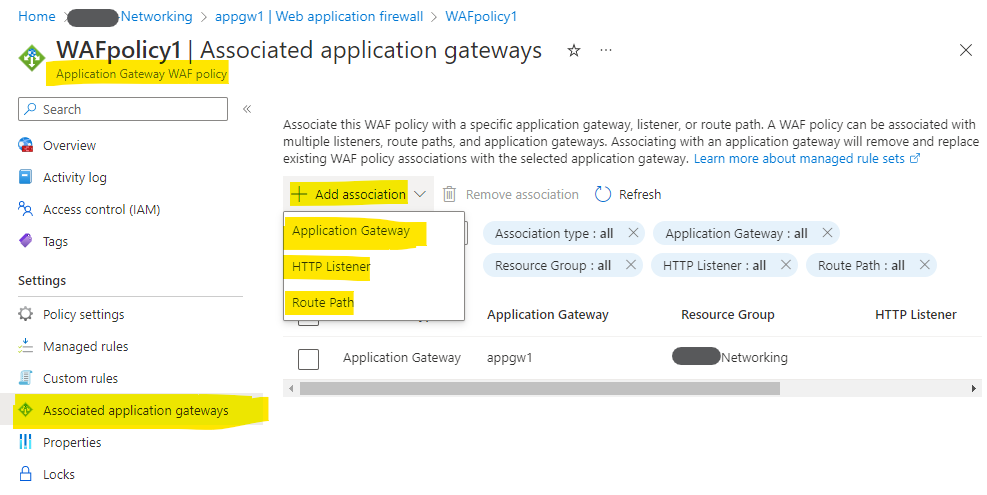
Then associate the WAF policy to any of the below combination:
- Your application gateway - When you associate a WAF policy globally, every site behind your Application Gateway WAF is protected with the same managed rules, custom rules, exclusions, and any other configured settings.
- Any specific listener - With per-site WAF policies, you can protect multiple sites with differing security needs behind a single WAF by using per-site policies.
- Any path-based rules - If there are certain pages within a single site that require different policies, you can make changes to the WAF policy that only affect a given URI.
Refer : https://learn.microsoft.com/en-us/azure/web-application-firewall/ag/policy-overview
Kindly let us know if the above helps or you need further assistance on this issue.
----------------------------------------------------------------------------------------------------------------
Please "Accept the answer" if the information helped you. This will help us and others in the community as well.


