Active assignments of certain directory roles (for example "Application Administrator") that are limited to the scope of a service principal or application do not show up in /rolemanagement/directory/roleAssignmentScheduleRequests or /rolemanagement/directory/roleAssignmentScheduleInstances. Assignments with scope "Directory" however, do show up.
The assignments were done in the PIM portal. 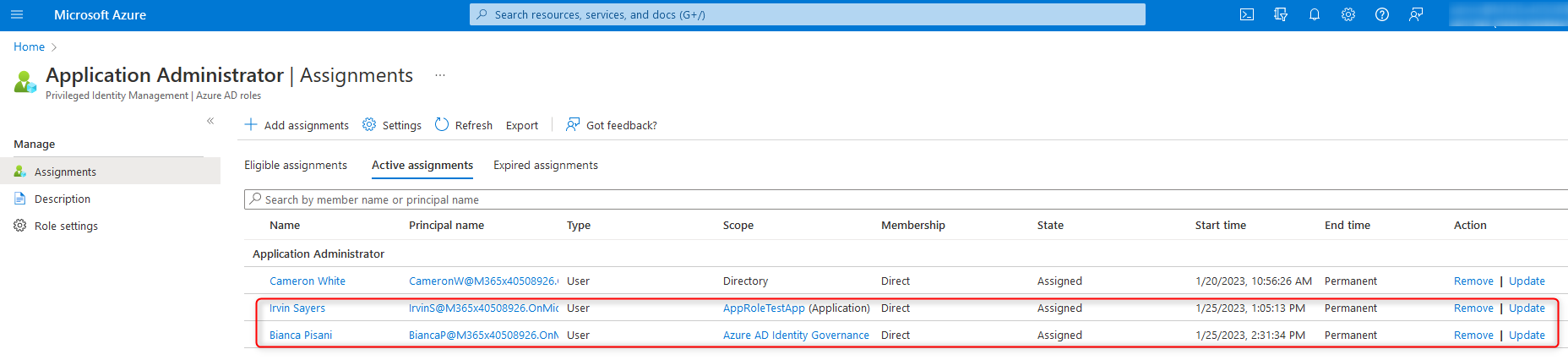
When using the Graph Explorer, the roleAssignmentRequests for those assignments do show up (https://graph.microsoft.com/v1.0/roleManagement/directory/roleAssignmentScheduleRequests)
Role: Application Administrator
Scope: Azure AD Identity Governance - Dynamics 365 Management (ServicePrincipal)
Principal: Bianca Pisani (User):
{
"id": "7b27f620-40f6-4820-9d6b-52aa47e87a16",
"status": "Provisioned",
"createdDateTime": "2023-01-25T13:31:33.537Z",
"completedDateTime": "2023-01-25T13:31:33.627Z",
"approvalId": null,
"customData": null,
"action": "adminAssign",
"principalId": "d74749ec-b59f-40db-91fa-1ffb3193da38",
"roleDefinitionId": "9b895d92-2cd3-44c7-9d02-a6ac2d5ea5c3",
"directoryScopeId": "/16f0f7f3-a69a-4a4f-94f5-5f43c71e95f5",
"appScopeId": null,
"isValidationOnly": false,
"targetScheduleId": "7b27f620-40f6-4820-9d6b-52aa47e87a16",
"justification": "Test 2",
"createdBy": {
"application": null,
"device": null,
"user": {
"displayName": null,
"id": "f60dbb25-9126-49b7-90f7-2bb7071015a0"
}
},
"scheduleInfo": {
"startDateTime": "2023-01-25T13:31:33.6253103Z",
"recurrence": null,
"expiration": {
"type": "noExpiration",
"endDateTime": null,
"duration": null
}
},
"ticketInfo": {
"ticketNumber": null,
"ticketSystem": null
}
}
Role: Application Administrator
Scope: AppRoleTestApp (Application)
Principal: Irvin Sayers (User)
{
"id": "856ca662-0724-4a1c-b70e-187888ff8983",
"status": "Provisioned",
"createdDateTime": "2023-01-25T12:05:13.11Z",
"completedDateTime": "2023-01-25T12:05:13.133Z",
"approvalId": null,
"customData": null,
"action": "adminAssign",
"principalId": "3b6b1d1d-cbaa-4012-a121-c5a9513df3e3",
"roleDefinitionId": "9b895d92-2cd3-44c7-9d02-a6ac2d5ea5c3",
"directoryScopeId": "/6021b74b-58f2-4ea1-ae9b-1430aed60cd2",
"appScopeId": null,
"isValidationOnly": false,
"targetScheduleId": "856ca662-0724-4a1c-b70e-187888ff8983",
"justification": "Test",
"createdBy": {
"application": null,
"device": null,
"user": {
"displayName": null,
"id": "f60dbb25-9126-49b7-90f7-2bb7071015a0"
}
},
"scheduleInfo": {
"startDateTime": "2023-01-25T12:05:13.1317387Z",
"recurrence": null,
"expiration": {
"type": "noExpiration",
"endDateTime": null,
"duration": null
}
},
"ticketInfo": {
"ticketNumber": null,
"ticketSystem": null
}
}
Allthough the status of those requests is "provisioned", corresponding schedule objects are not returned in
https://graph.microsoft.com/v1.0/roleManagement/directory/**roleAssignmentSchedules** or
https://graph.microsoft.com/v1.0/roleManagement/directory/**roleAssignmentScheduleInstances**
When reading assignments via https://graph.microsoft.com/v1.0/roleManagement/directory/**roleAssignments** however, they are returned:
Role: Application Administrator
Scope: Azure AD Identity Governance - Dynamics 365 Management (ServicePrincipal)
Principal: Bianca Pisani (User):
{
"id": "kl2Jm9Msx0SdAqasLV6lw-xJR9eftdtAkfof-zGT2jjz9_AWmqZPSpT1X0PHHpX1-1",
"principalId": "d74749ec-b59f-40db-91fa-1ffb3193da38",
"directoryScopeId": "/16f0f7f3-a69a-4a4f-94f5-5f43c71e95f5",
"roleDefinitionId": "9b895d92-2cd3-44c7-9d02-a6ac2d5ea5c3"
}
Role: Application Administrator
Scope: AppRoleTestApp (Application)
Principal: Irvin Sayers (User)
{
"id": "kl2Jm9Msx0SdAqasLV6lwx0dazuqyxJAoSHFqVE98-NLtyFg8lihTq6bFDCu1gzS-1",
"principalId": "3b6b1d1d-cbaa-4012-a121-c5a9513df3e3",
"directoryScopeId": "/6021b74b-58f2-4ea1-ae9b-1430aed60cd2",
"roleDefinitionId": "9b895d92-2cd3-44c7-9d02-a6ac2d5ea5c3"
}
Is this an intended behavior?
