@test A
Kindly follow the given process:
- Get a workload identity license added in your tenant.
- Once added navigate to Conditional access blade and under Assignments select workload identities and choose the service principal of your AAD registered app:
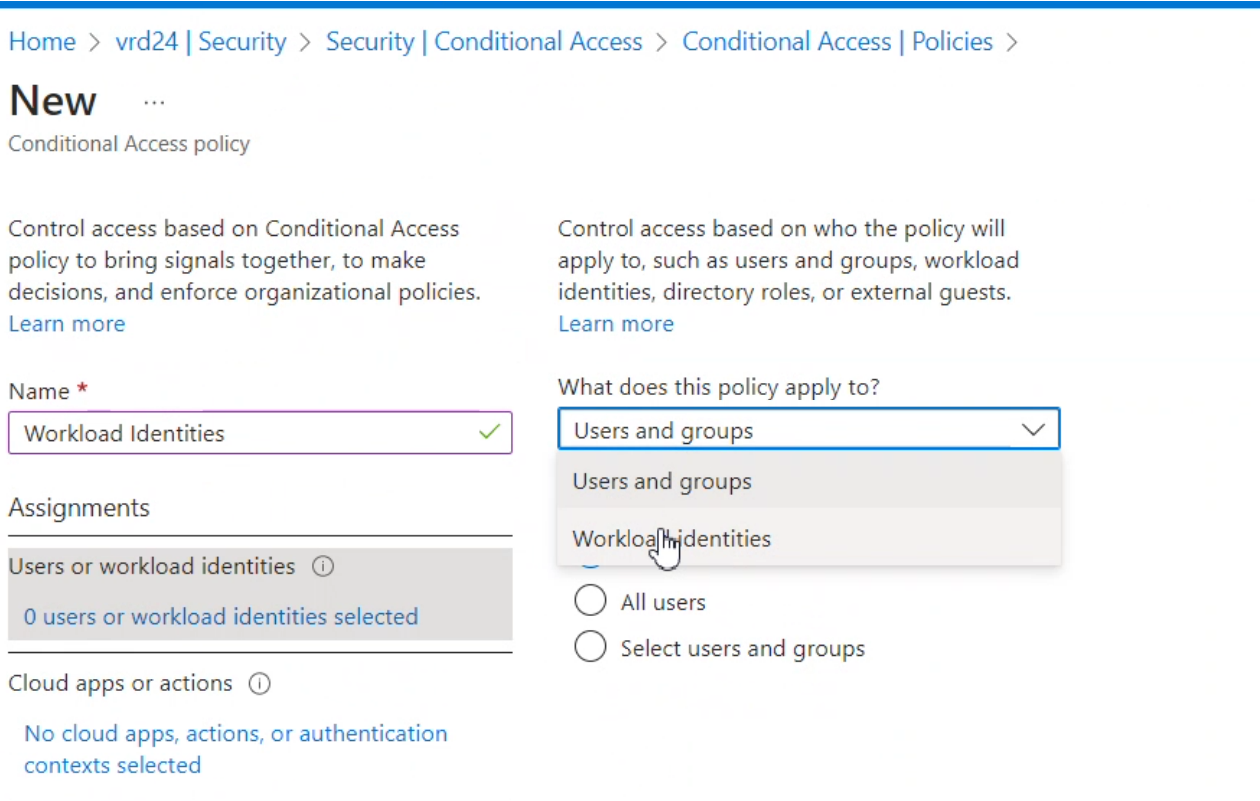
- Under Cloud apps or actions select all cloud apps:
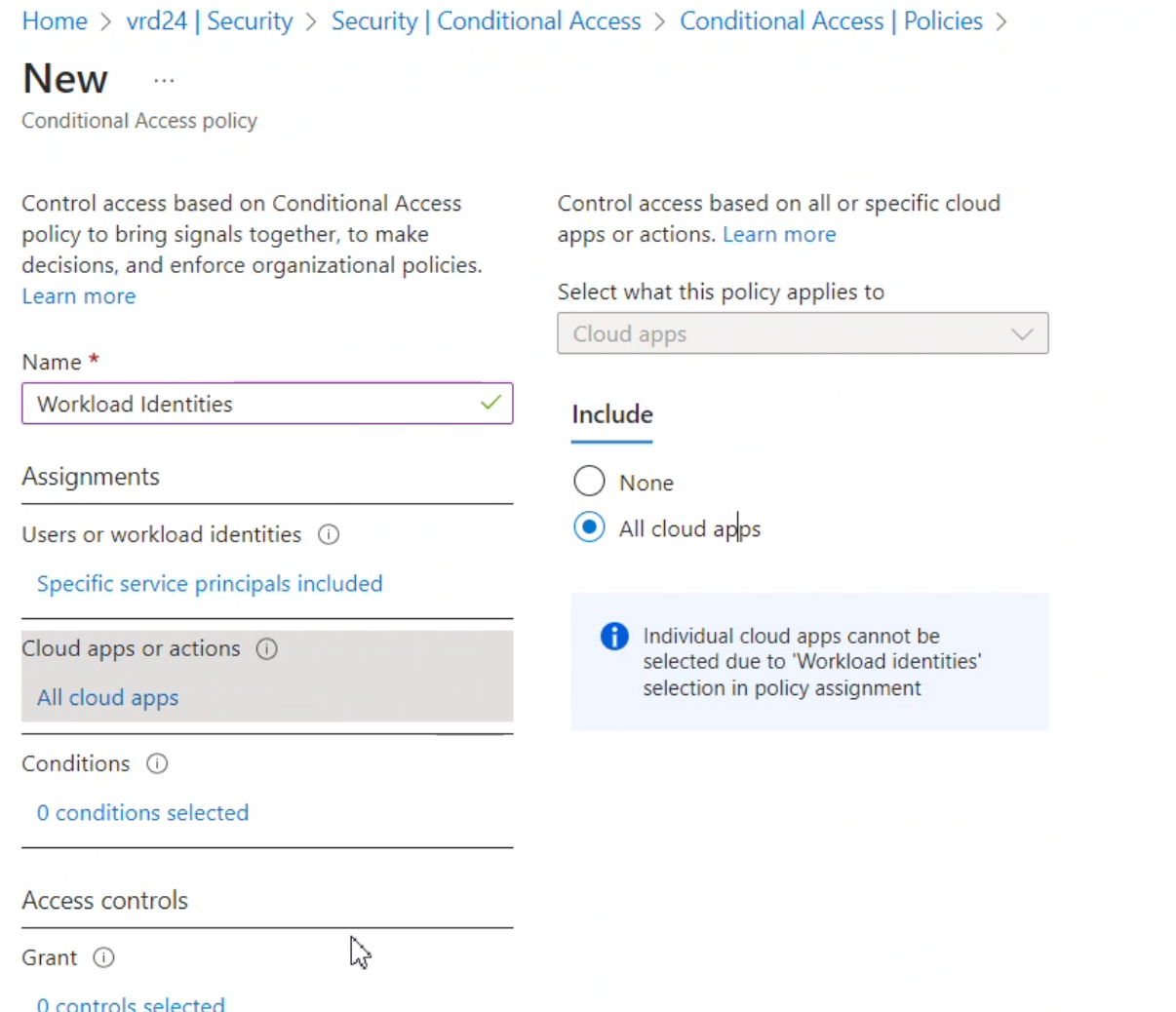
- Select the conditions under which your action evaluating access would be allowed or blocked. Currently only "Service principal Risk" and "Locations" are available for selection.
-
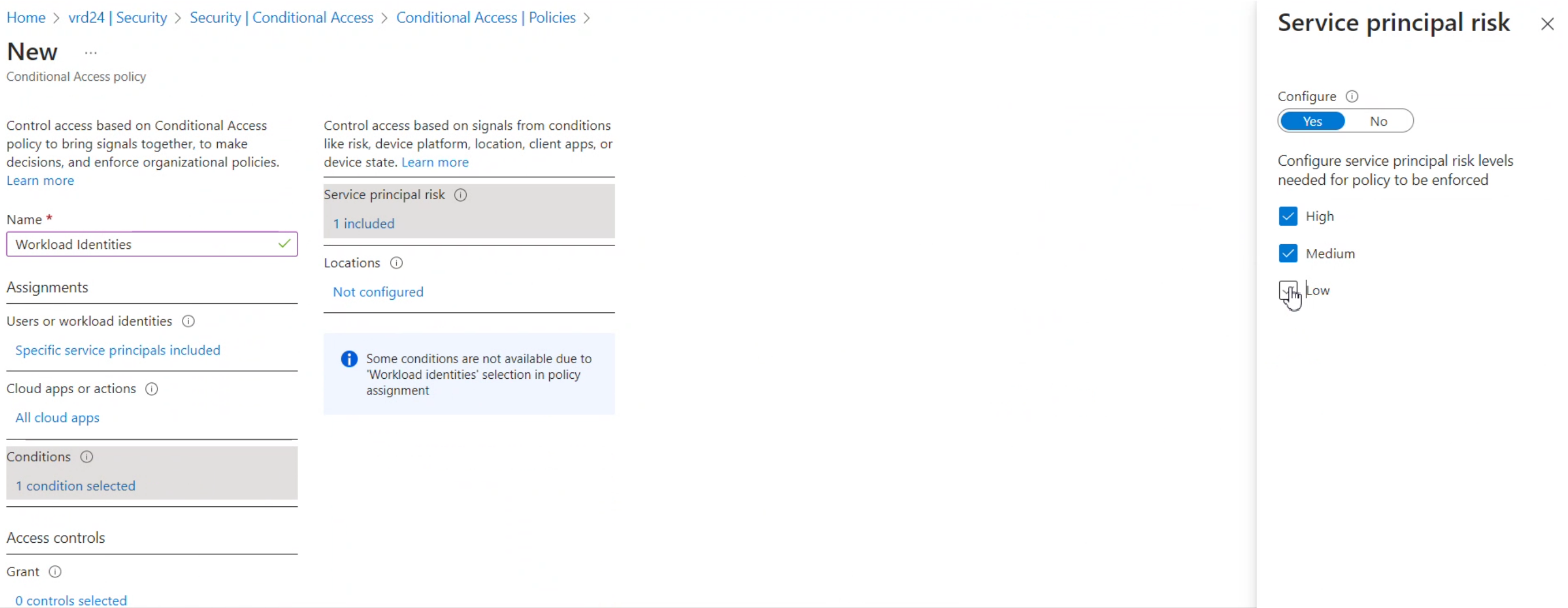
- Under Grant, select "Block"
Conclusion: Any access done when this service principal (Registered App) is evaluated as risky or out side trusted Location will be blocked
Please do let me know if you have any further queries.
Thanks,
Akshay Kaushik
Please "Accept the answer" (Yes/No), and share your feedback if the suggestion works as per your business need. This will help us and others in the community as well.

