In your case, you've created an NSG rule that denies outbound internet access. However, this might also inadvertently block necessary communication for your SQL Server. SQL Server Management Studio (SSMS) uses various protocols and ports for connectivity, and these rules might not be allowed by default in the NSG.
NSG DenyInternetOutBound on VM with azure-ad MFA login

Hello, everyone,
we have three SQl servers in Azure and a VM to be used for SQL management.
The SQL servers are set up with Azure AD authentication, the SQL admins are forced to use MFA.
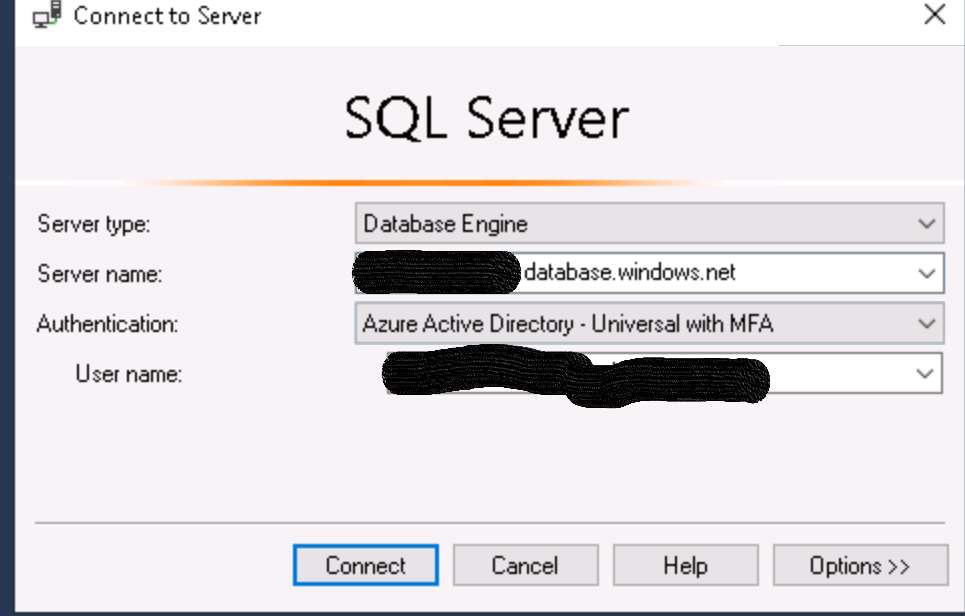
In the VM the SQL Server Management Studio is installed and the access works well.
Now I want to protect the VM with a NSG that prevents access to the internet.
I have created an NSG which is bound to the subnet
If I now make a DenyInternetOutBound rule, I can no longer access the SQL servers.The login does not work anymore, the login page does not appear.
AzureADAllow, AzureCloudAllow and SqlWestEuropeAllow roules are configured
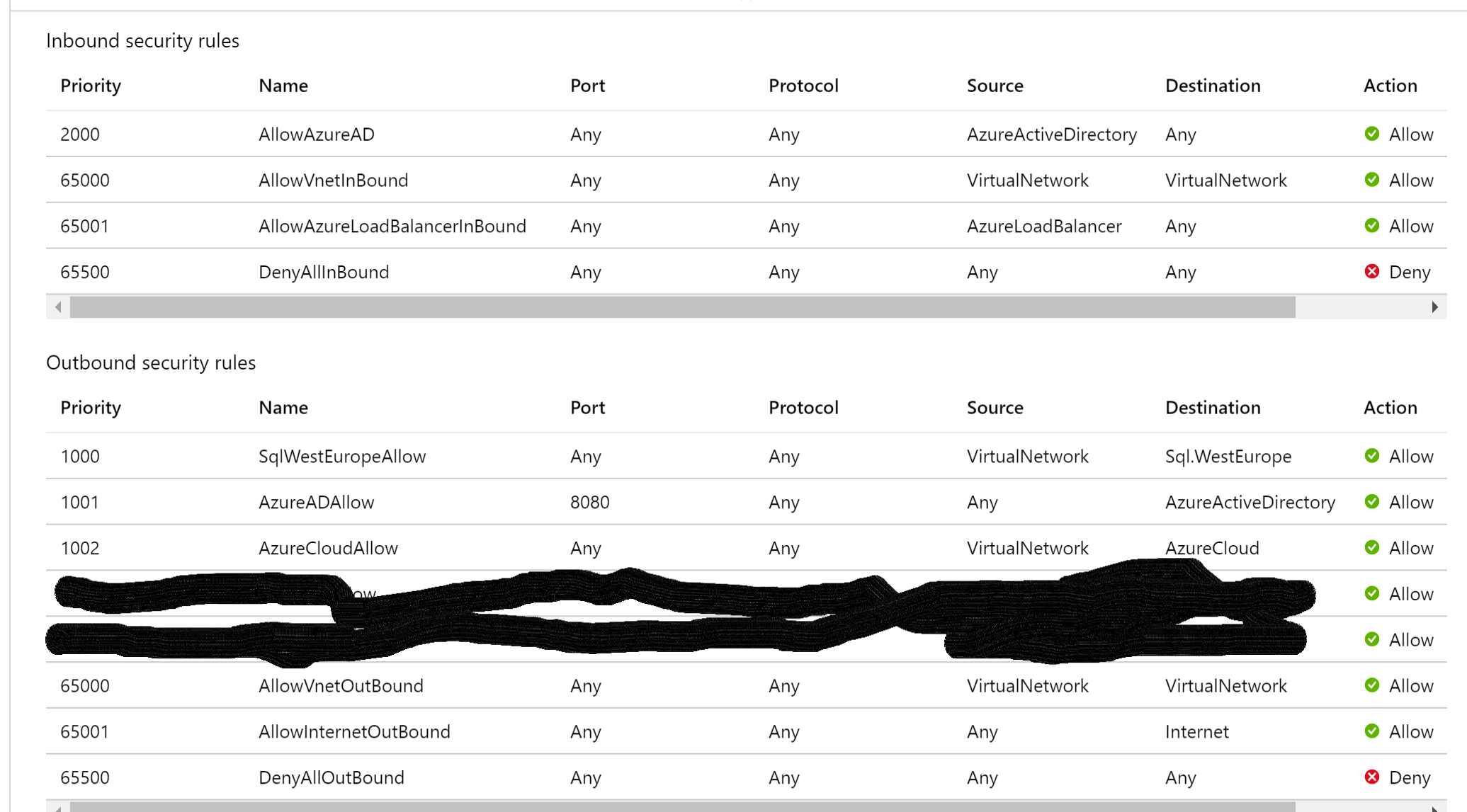
Does anyone know how I can use denyinternet rule with ad login with MFA?
thanks
Guido
